PGA infected in Possible Ransomware Attack
Recently many security firms have detailed the rise of cryptojacking as a favored method of hackers for increasing their payroll. What was noticed was the detections of ransomware had declined massively while cryptojacking detections had skyrocketed exponentially. This led some to believe that ransomware was slowing dying. Recent events prove this not to be the case or in the very least hackers using ransomware variants did not get the memo their favored malware variant is dead.
Over the weekend news began surfacing that TSMC, the company responsible for the processors in many of Apple’s mobile devices, suffered a WannaCry attack. Last year the City of Atlanta was devastated by a ransomware attack which cost the city 2.6 million USD to recover from. Yesterday Golf Week published an article stating that the PGA had suffered an attack by hackers which resulted in officials been locked out of crucial files related to this week’s PGA Championship at Bellerive Country Club and the upcoming Ryder Cup in France.
Details of the Attack
On Tuesday, August 7, 2018, staff at one of golf’s most prestigious governing bodies realized that their network had been compromised. This realization came when staff attempted to work on certain files and were greeted with a message which read as follows: “Your network has been penetrated. All files on each host in the network have been encrypted with a strong algorithm.” The message further stated that any attempts to try and decrypt the affected files would result in the loss of those files. It can be assumed that the files would then be unrecoverable. To those working at the PGA, it was clear that the aim of the hackers was to extortion. It can be safely assumed then that the PGA had suffered a ransomware attack.
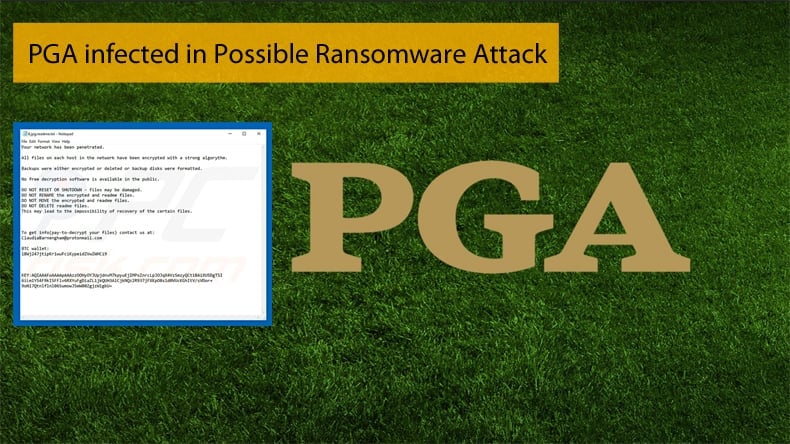
The files contained creative materials for the PGA Championship at Bellerive and next month’s Ryder Cup in France. That includes extensive promotional banners and logos used in digital and print communications, and on digital signage around the grounds at Bellerive. The stolen files also include development work on logos for future PGA Championships. Some of the work began more than a year ago and cannot be easily replicated. The ransom message included a Bitcoin wallet number, but no specific ransom amount was demanded the return of the files. As to whether the PGA paid or not is not known. A spokesperson for the PGA of America said the organization would be declining comment on the hacking because it is an ongoing situation.
The Ransomware may have been Bitpaymer
Lawrence Abrams of Bleeping Computer is of the opinion that the ransomware variant used may have been Bitpaymer. Mr. Abrams bases his assumption on the fact that the world algorithms is misspelled in the ransom note. This has often been the case in past infections using the Bitpaymer ransomware. Although this variant has been around for a while it has kept a low profile, particularly when compared to other variants like Locky or WannaCry. However, based on ID Ransomware detections Bitpaymer has shown a moderate increase in activity recently.
Bitpaymer has been used in the past to target corporate networks rather than the shotgun approach which people associate with ransomware. This is similar in approach to how SamSam has operated in the past. Bitpaymer gains access to the system via hacking into Remote Desktop Services connected to the Internet. Once inside a network, they traverse through it and encrypt every computer they can get access to. Some of the more recent variants have been appending the .locked extension to encrypted files and dropping ransom notes of the same name as the encrypted files but with “.readme_txt” appended to it. For example, an encrypted file called test.jpg would also have a ransom note named test.jpg.readme_txt. Although no ransom demand was fixed in the case of the PGA attack those using this variant are known to charge very large ransom amounts to decrypt computers. In one case one BitPaymer infection in the past asked for 53 bitcoins to decrypt an entire network. At the time of writing that would be approximately 336,197 USD to decrypt the network.
Another important feature of Bitpaymer is that it is considered to be a secure ransomware. Unfortunately for the PGA, this means that either the association pay the ransom or rely on previous backups if they have been doing so. Bitpaymer was also recently used in an attack against an Alaskan town which resulted in the town having to use typewriters for a week. In a recent report published by ESET the firm provided evidence linking Bitpaymer, which they refer to as FriedEx, to the same criminal group running the infamous Necurs spam botnet and the Dridex banking trojan.
Ransomware not Dead
Given the recent spate of ransomware incidents, any assumption as to the death of ransomware appears to be wrong in the extreme. It would seem that rather than the shotgun approach of infecting as many computers as possible in the shortest amount of time, that was incredibly popular among hackers, the favored tactic is applying a targeted approach. Generally, hackers who apply such an approach are of a higher caliber or more experienced than the run of the mill hacker. This would further mean that the deploying of ransomware is still a viable attack method and employed by more experienced hackers.
Ransomware is certainly not dead, rather it has become sneakier. This has the potential to make it more of a threat to specific organizations and other targets.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion