TSMC Suffers WannaCry Attack
News began surfacing on August 6, that TSMC, or to give the company its unabbreviated name Taiwan Semiconductor Manufacturing Company, suffered a malware incident over the previous weekend. It was revealed that the chip manufacturer suffered a WannaCry attack which resulted in plant closures, all of which had an impact on production. TSMC is the company responsible for manufacturing a very large percentage of Apple’s processing units, most been used in mobile devices like the iPhone. It is also further widely believed that the company is producing the technology behind the A12 core processor chips in the new iPhone scheduled for release later this year.
TSMC Press Statement
The company was incredibly quick to release a statement detailing what had happened. The statement was released on August 5, two days after fabrication plants had to be shut down. According to the company, the following was the cause of the infection,
“This virus outbreak occurred due to misoperation during the software installation process for a new tool, which caused a virus to spread once the tool was connected to the Company's computer network. Data integrity and confidential information were not compromised. TSMC has taken actions to close this security gap and further strengthen security measures.”
Further, the company confirmed that it was indeed the WannaCry ransomware, now infamous, that was behind the infection. TSMC said a software tool was installed and was not properly isolated or confirmed to be virus-free.
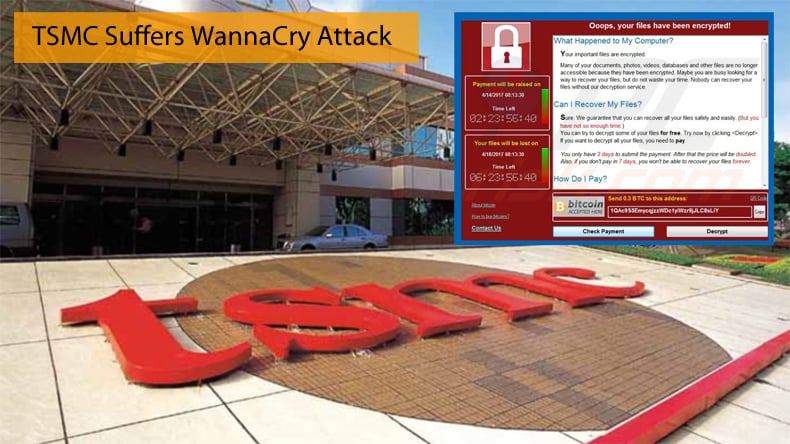
When that tool connected to the network the WannaCry variant led to continual reboots. This resulted in the malware infecting critical fabrication tools and automated materials handling systems which used Windows 7 without patched software as the interface. As a result, tools were inoperable resulting in a plant shutdown. By the time the statement was released to the public the company confirmed that it was able to recover 80% of its equipment affected by the malware attack and that a full recovery was expected by August 6.
Financial Impact
TSMC further confirmed that the attack would indeed result in production and shipping delays. In the company’s own words,
“We estimate the impact to third quarter revenue to be about three percent, and impact to gross margin to be about one percentage point. The Company is confident shipments delayed in the third quarter will be recovered in the fourth quarter 2018 and maintains its forecast of high single-digit revenue growth for 2018 in U.S. dollars given on July 19, 2018.”
It is almost a fact of life that news of a cyber attack resulting in a factory shutdown will impact the company’s performance inin relevant markets. The company has released newly revised financial data which includes this new reality. The company estimates that the attack will result in a loss of 2%, approximately 170 million USD, in the company’s revenue for the July-September period. In an earlier statement made to reporters, the company estimated the incident would lower quarterly sales by 3%. The reduction was based on the previous revenue forecast of 8.45 billion USD to 8.55 billion USD for the current quarter and gross margin of 48% to 50%.
The market, in turn, responded to the news negatively. Shares of TSMC fell 0.61% on Monday to close at NT$245.50, while rival United Microelectronics Corp. of Taiwan gained 1.41% and China's Semiconductor Manufacturing International Co. dropped 1.22%. MediaTek, the world's No. 2 mobile chip provider and a key TSMC customer, also saw its shares edge lower by 0.36%. When compared to how Equifax shares tanked on news of their massive data breach last year, TSMC’s cyber attack appears minor. This is in part to the company’s quick response to the problem and the speed at which normal business could be returned to. When the initial outbreak of WannaCry occurred in May 2017 it took the British NHS until October of that year to know the full extent of the attack in comparison.
Cause of the Infection
Recently there has been a rise in accusations of cyber espionage in Asia. This is as a result of a rising technology cold war between Beijing and Washington following trade tariffs imposed by President Trump and the threat of a trade war. China has also been accused of being behind such campaigns. Given this current climate industry executives and investors worry that TSMC, a crucial player in the world's semiconductor supply chain, could become a target for hackers and other state-sponsored groups looking to steal vital technical details. TSMC was quick to quell such fears.
The company’s CEO, C.C. Wei, told reporters that is was the company’s belief that the infection was a result of negligence and human error rather than industrial espionage. Wei further assured investors and the general public that all key chip design blueprints and production data for customers stayed intact without theft or damage. If the company’s public statements reflect what actually happened it may indicate that companies, in general, are focussed on attacks occurring from outside the company attempting to gain access rather than potential security weaknesses from inside the company. In this regard vulnerabilities inside the internal firewalls should be seen as an important factor in a complete corporate security policy.
Based on statements made in TSMC’s annual cybersecurity report may have predicted such events. Within the report the company stated,
“Even though we have established a comprehensive Internet and computing security network, we cannot guarantee that our computing systems which control or maintain vital corporate functions, such as our manufacturing operations and enterprise accounting, would be completely immune to crippling cyber attacks by any third party to gain unauthorized access to our internal network systems, to sabotage our operations and goodwill or otherwise. In the event of a serious cyber attack, our systems may lose important corporate data and our production lines may be shut down indefinitely pending the resolution of such attack. While we also seek to annually review and assess our cybersecurity policies and procedures to ensure their adequacy and effectiveness, we cannot guarantee that we will not be susceptible to new and emerging risks and attacks in the evolving landscape of cybersecurity threats.”
It would seem that those behind the report may have foreshadowed the incident that occurred on August 3.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion