Ryuk and TrickBot Now Partners in Crime
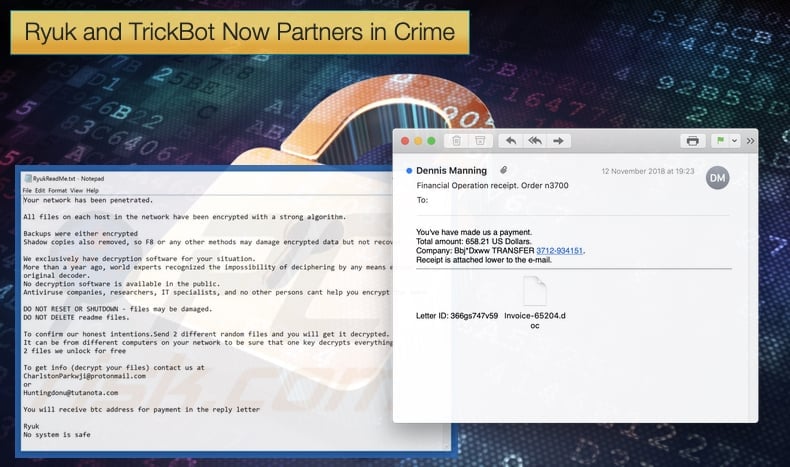
The Ryuk ransomware, named after a character from the popular Death Note anime, has become known as targeted ransomware. Discovered in August 2018, it was seen been used by hackers to first scope out potential targets. Once a suitable target was found the ransomware gained access to the targeted computer via Remote Desktop Services and then proceed to steal credentials. This targeted approach allowed hackers to target businesses and other high profile targets in order to extort greater sums of money. Now new research suggests that the operators of Ryuk and the infamous TrickBot have partnered up to earn even more money from their illicit trade.
Ryuk made international headlines when it was linked to a ransomware attack which affected the newspaper distribution networks of large media houses including the Wall Street Journal, New York Times, and Los Angeles Times. It has been estimated that those behind Ryuk have already netted approximately 3.7 million USD. New research published by both FireEye and CrowdStrike show that those behind Ryuk are looking to extort even more funds by partnering with the group behind TrickBot.
In both security firms’ research, it is explained how TrickBot is being used by other actors to gain access to infected networks. Once these bots infect a computer, they would create reverse shells back to other hackers, for example, the ones behind Ryuk, so that they can manually infiltrate the rest of the network and install their payloads. FireEye has called this type of access TEMP.MixMaster as a catch-all term to describe any incidents that they have seen where Ryuk is installed following a TrickBot infection.
They are of the belief that the TrickBot operators are renting their service to a limited number of cybercriminals who use it to gain access to networks where TrickBot is installed. In other terms, the operators are offering TrickBot as a Malware-as-a-Service (MaaS). Researchers stated that
“The TrickBot administrator group, which is suspected to be based in Eastern Europe, most likely provide the malware to a limited number of cyber-criminal actors to use in operations,”
TrickBot Distribution Methods
Much of CrowdStrike’s research dealt with how TrickBot is distributed. It is probably this aspect that enticed the operators of Ryuk to partner up. TrickBot is commonly distributed through large spam email campaigns including attachments that install the malware onto a computer. Researchers have also seen that TrickBot can be installed via a different malware called Emotet that is also distributed through spam emails. In the latest detected instances, the spam emails attempt to resemble legitimate companies. Emails pretending to be from HSBC, Lloyds Bank, and Deloitte have been seen and they take the format of payroll schedules or similar documents. Emails used in the campaign are laced with malware which has macros enabled, then payloads are downloaded and TrickBot installed on the victim's computer.
Hackers behind the campaign then install Ryuk throughout the network. This is done by downloading the PowerShell post-exploitation toolkit called Empire, a tool used to help distribute payloads and also remain to assist in malware remaining undetected. This does not necessarily mean that those behind Ryuk have completely changed tactics. Researchers are still confident that future campaigns of Ryuk will still be spread by Remote Desktop Services. Rather the partnering should be viewed as offering the hackers another target of opportunity in order to gain a foothold in a network and further increase the money made by the group.
Maybe not the Work of North Korea
When Ryuk was initially seen in the wild some researchers within the InfoSec community were quick to attribute the attack campaigns to the infamous Lazarus group. The group goes by many names but is seen as one of North Korea’s primary state-sponsored advanced persistent threat groups. The attribution to Lazarus was based on the similarities between Ryuk and the Hermes ransomware. Perhaps one of the more famous instances of Hermes in action was seen when it was deployed against the Far Eastern International Bank (FEIB) in Taiwan. Here the hackers exploited the SWIFT global financial network to steal roughly 60 million USD which was transferred to several countries. Researchers based at BAE Systems identified some of the tools used in the attack and found connections to tools and tactics employed by Lazarus.
With the link between Ryuk and Hermes, it seemed Lazarus may be behind Ryuk deployment. However, the research done by FireEye and CrowdStrike discussed above debunks this theory. Researchers noted that while similarities between the two ransomware variants exist Hermes was been sold on underground black markets as early as 2017. These researchers are of the opinion that although Lazarus did use Hermes in the FEIB attack it is likely that those behind Ryuk had access to Hermes’ source code and compiled a new version.
Researchers also pointed out that the group behind TrickBot is believed to operate from Eastern Europe. Researchers at CrowdStrike believe that the cybercriminal known as “Grim Spider” is behind Ryuk and that the cybercriminal is part of a larger group who are behind TrickBot. The attack which affected major US media outlets MacAfee analyzed the attack and said that “the Ryuk attacks may not necessarily be backed by a nation-state, but rather share the hallmarks of a cybercrime operation,” back in 2018. More recently the security firm noted that,
“The most likely hypothesis in the Ryuk case is that of a cybercrime operation developed from a tool kit offered by a Russian-speaking actor. From the evidence, we see sample similarities over the past several months that indicate a tool kit is being used,”
McAfee has, perhaps wisely, refrained from attributing the latest Ryuk and TrickBot instance to any one group.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion