Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is Emotet?
Emotet trojan (also known as Geodo) is high-risk malware designed to record personal data and proliferate other viruses. Research shows that Emotet infiltrates systems without users' consent.
After successful infiltration, this malware modifies system settings and uses the infiltrated computer to proliferate itself further. Cyber criminals usually spread this virus using spam email campaigns.
Emotet malware overview
A main feature of Emotet is to gather various sensitive information, including logins/passwords and browsing activity. Collected data often includes banking information. Therefore, the presence of Emotet can lead to serious privacy issues and significant financial loss (cyber criminals can misuse the data to transfer money or make various purchases).
Malware distribution is also an issue. Emotet works as a trojan - it opens "backdoors" for other high-risk viruses (e.g., Dridex) to infiltrate the system. These additional viruses might be more dangerous. Therefore, having Emotet installed on your system can lead to a chain of system infections.
Emotet is also capable of connecting the infected computer to a botnet, which is used to proliferate spam emails that distribute this malware. In addition, this malware hides within system folders and registers as a 'system service', thereby modifying Windows Registry settings so that it auto-runs when the system is started.
Emotet hide its tracks and, therefore, is virtually impossible for regular users to detect. If you suspect that Emotet is present, immediately scan the system with a legitimate anti-virus/anti-spyware suite. In fact, have a reputable suite installed and running and scan the system periodically.
| Name | Emotet trojan |
| Threat Type | Trojan, password-stealing virus, banking malware, spyware. |
| Detection Names | Avast (Win32:Trojan-gen), BitDefender (Trojan.GenericKDZ.62408), ESET-NOD32 (A Variant Of Win32/Kryptik.HARE), Kaspersky (Trojan-Banker.Win32.Emotet.evmh), Full List (VirusTotal) |
| Symptoms | Trojans are designed to stealthily infiltrate the victim's computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software 'cracks'. |
| Damage | Stolen passwords and banking information, identity theft, the victim's computer added to a botnet. |
| Additional Information | Presence of Emotet trojan can be detected with EmoCheck tool developed by Japan CERT. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Similar trojan-type malware examples
There are dozens of trojans similar to Emotet including, for example, Adwind, Pony, and Trickbot. Their behavior might differ slightly (in terms of information tracking, crypto-mining, botnet connections, and similar), however, all of these viruses are extremely harmful and pose a direct threat to your privacy and browsing safety.
How did Emotet infect my computer?
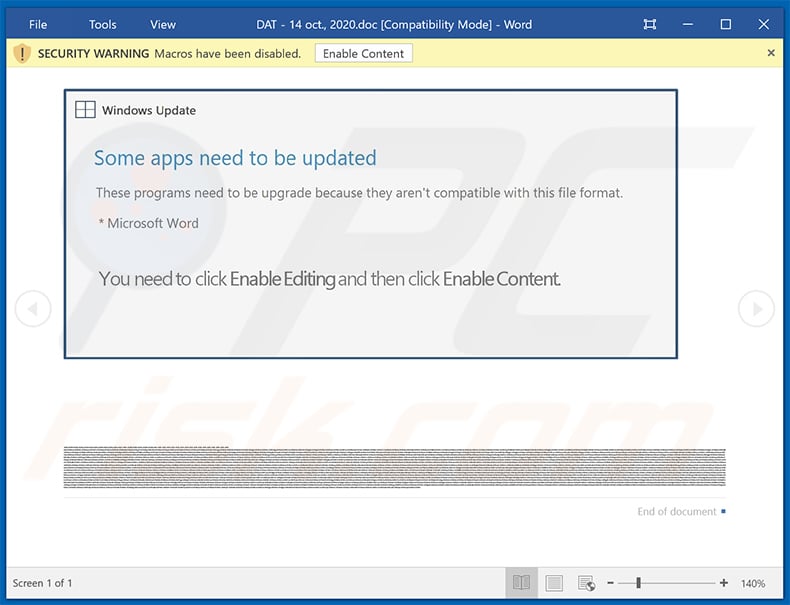
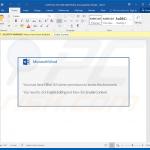
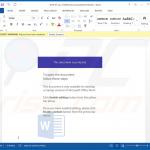
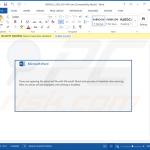
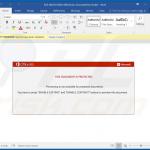
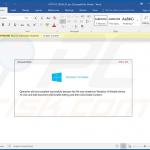
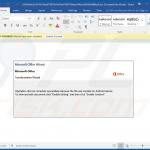
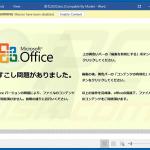
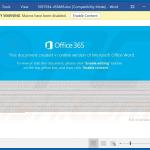
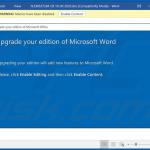
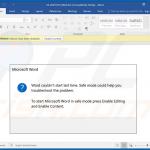
In most cases, Emotet is proliferated using spam email campaigns. The emails are delivered together with malicious attachments (usually Microsoft Word documents) or links, leading to execution of a malicious JavaScript file.
Once opened, malicious MS Word documents ask users to enable macro commands (otherwise the content will supposedly not be displayed properly), however, in doing so, users inadvertently grant the document permission to connect to a remote server and execute a JavaScript file designed to download and install Emotet into the system.
Links that are attached to emails have an essentially identical function - they lead to malicious JavaScript files. Cyber criminals typically disguise attachments/links as bills, invoices, and other finance-related documents that seem important.
These emails usually deliver messages warning users about certain problems (e.g., unpaid bills, lost invoices, etc.) and advising them to open attached documents/files. Doing so results in infiltration of Emotet malware. This is a common technique used to distribute trojan-type viruses.
It is very effective, since many careless users open received attachments without understanding the possible consequences. This behavior often leads to various computer infections.
How to avoid installation of malware?
The main reasons for computer infections are poor knowledge and careless behavior. The key to safety is caution. Therefore, pay close attention when browsing the internet and downloading, installing, and updating software. Never open email attachments or links that seem irrelevant or have been received from a suspicious email address.
We strongly recommend that you delete these emails immediately. Download your programs from official sources only, using direct download links. The same applies to updating software. Keep installed applications up-to-date, however, this should be achieved using implemented update functions or tools provided by the official developer only.
As mentioned above, having a legitimate anti-virus/anti-spyware suite installed and running is also paramount. If your computer is already infected with Emotet, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Update September 17, 2019 - For a short period of time Emotet's Command & Control (C&C) servers were shut down and, thus, infected machines were no longer controlled by Emotet's developers. However, in late August cyber criminals have re-started their distribution campaigns and Emotet is now back in the game.
There are two main distribution methods that cyber criminals currently use: 1) the aforementioned email spam campaigns, and; 2) hijacking of legitimate websites and injecting them with malicious scripts that download/install Emotet into visitors' computers.
According to Confense Labs' researchers, Emotet's developers are currently targeting around 66000 email address for over 30000 domain names under 385 top-level domains. It is also worth noting that crooks target not only home users, but various companies and even governmental agencies as well.
Spam emails typically come with a malicious attachment (link/file) which, once opened, injects Emotet into the system. In some cases, the attachments inject other malware (e.g., TrickBot) which eventually download and install Emotet. It is known that spam campaigns (at least at this current moment) used to spread Emotet are typically related to finances.
List of legitimate websites hijacked by Emotet's developers includes (but it is not limited to):
- biyunhui[.]com
- broadpeakdefense[.]com
- charosjewellery[.]co.uk
- customernoble[.]com
- holyurbanhotel[.]com
- keikomimura[.]com
- lecairtravels[.]com
- mutlukadinlarakademisi[.]com
- nautcoins[.]com
- taxolabs[.]com
- think1[.]com
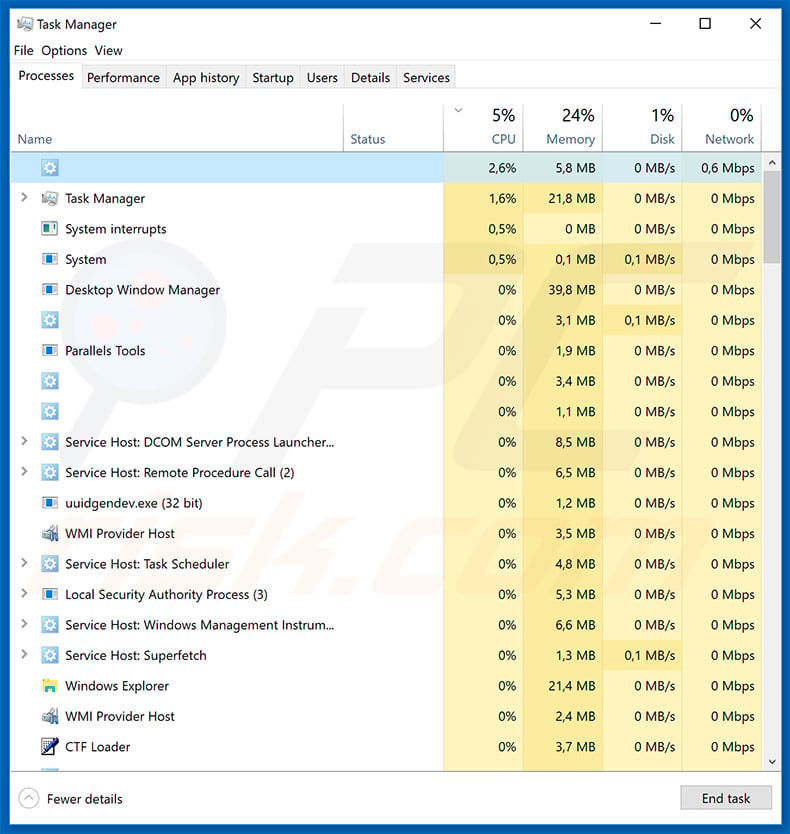
Emotet trojan process (blank name) in Windows Task Manager:
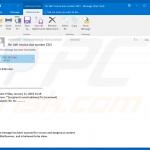
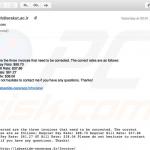
Samples of spam emails distributing Emotet malware:
Examples of other malicious MS Office documents designed to spread Emotet trojan:
Update February 4, 2020 - Cyber criminals have recently started a new email spam campaign in order to spread Emotet trojan.
The spam campaign is related to Coronavirus and the emails typically contain messages encouraging recipients to open attachments (mostly Microsoft Word documents) which supposedly contain information regarding the infection (e.g., list of infected people, details how to act in case of infection and so forth).
Crooks also disguise under names of various authorities in order to create the impression of legitimacy.
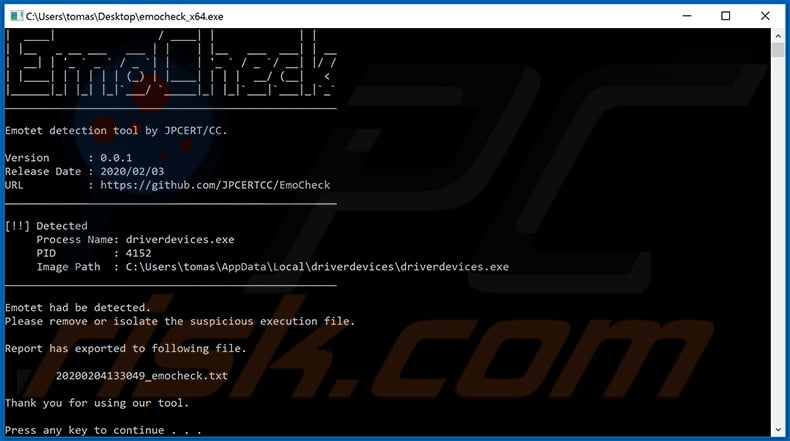
Japan CERT has recently released a tool called EmoCheck, that is designed to detect whether the system is infected with Emotet trojan or not. Therefore, if you're not sure if this malware is present, you can easily detect it with the EmoCheck tool (you can download this tool from Japan CERT's GitHub page).
Screenshot of EmoCheck tool:
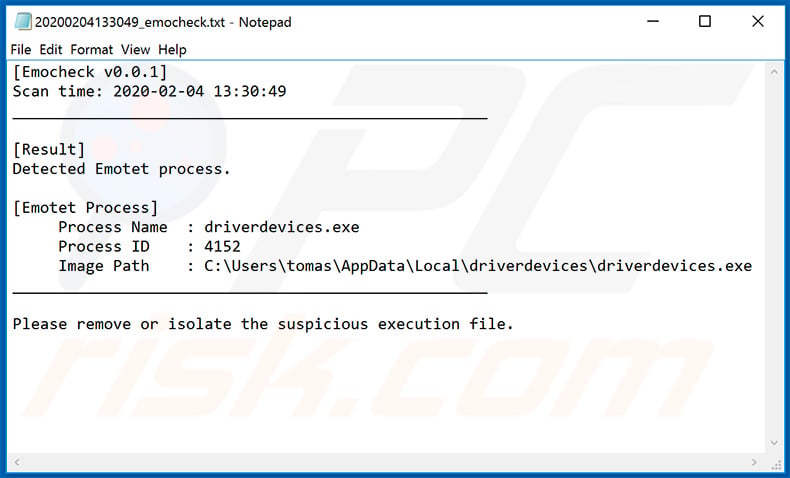
Screenshot of log file created by the EmoCheck tool:
Update February 6, 2020 - During the first few months of each year companies, small businesses and regular people have to fill various tax forms to provide government with finance-related information.
Cyber criminals often take advantage of this period by creating fake governmental (phishing) sites that steal personal data, sending deceptive emails that contain malicious attachments and so on so forth.
2020 is no exception - people behind Emotet trojan started a new spam campaign which delivers emails containing either attached malicious documents (typically Microsoft Word files) or links leading to such files. In the email samples we analyzed attachments were presented as W-9 tax forms.
However, there's very likely to be a number of other variants of such Emotet-distributing spam campaigns that present malicious attachments as other tax-related documents. Once opened, these attachments barely different from the aforementioned ones - they simply display messages stating that the content cannot be displayed unless the macros are enabled.
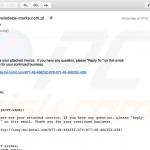
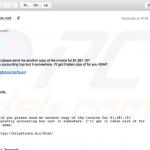
Examples of tax-related email spam campaigns distributing Emotet trojan:
Update February 10, 2020 - A yet another updated version of Emotet trojan has been recently released. This new variant has been implemented with a feature allowing hackers to infect computers connected to nearby Wi-Fi networks.
After infiltrating a device, Emotet starts scanning for nearby Wi-Fi networks and, if found, attempts to bruteforce their passwords in order to connect. Once connected, Emotet searches for other devices (connected to the same network) which have non-hidden shares.
After finding such devices, Emotet attempts to, again, bruteforce the administrator's password in order to infiltrate the system and drop/execute the malicious payload - itself. In order to gain persistence, Emotet also installs a new service titled "Windows Defender System Service".
Update March 19, 2020 - TrickBot and Emotet developers are taking advantage of the current situation regarding Coronavirus in order to make the malicious files "less detectable". What cyber criminals do is insert quotes from various speeches about the Coronavirus (e.g., quoting Donald Trump, CNN articles, etc.) into the description of each malicious file.
By doing so, crooks decrease the chance of anti-virus suites detecting malware. You can find more details in Lawrence Abram's article posted in Bleeping Computer.
Update July 22, 2020 - Cyber criminals have recently started a huge spam campaign to spread Emotet trojan. This is the first major spam campaign after five months of hiatus.
Nonetheless, the tactic itself remains the same - crooks send hundreds of thousands of spam emails containing malicious attachments (Microsoft Office documents) which are designed to inject malware into the system.
Research results show that these documents, at least at this current moment, communicate with hijacked servers, most of which are used to host WordPress sites. You can find more information in our "Emotet surges back to Life". It also worth mentioning that Emotet, as a botnet, is now heavily used to spread Qakbot banking trojan.
This indicates that Emotet's developers have started a partnership with Qakbot's developers, since Emotet was mostly used to spread TrickBot - another high-risk trojan.
Update July 29, 2020 - New tactics have been observed in the proliferation of the Emotet malware via email spam campaigns. This malicious software has been updated with an email attachment stealing module. Therefore, from infected systems Emotet can obtain genuine email attachments, which are then used to increase the legitimacy of scam mail spreading this malware.
The aforementioned technique adds to a previous distribution tactic, by which a virulent URL or file is added to an existing email chain. Thereby tricking users into opening malicious links/attachments that are inserted into conversations between trustworthy contacts. More information on these developments can be found in an article by Sergiu Gatlan on Bleeping Computer.
Update August 17, 2020 - Cyber criminals have recently started a new email spam campaign targeting employees of various organizations. It is common for crooks to target huge companies and organizations, because the profits are way larger, even when the chances of infecting someone's computer are way smaller.
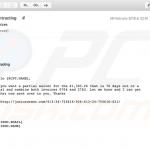
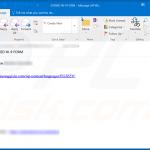
Example of an email from this email spam campaign:
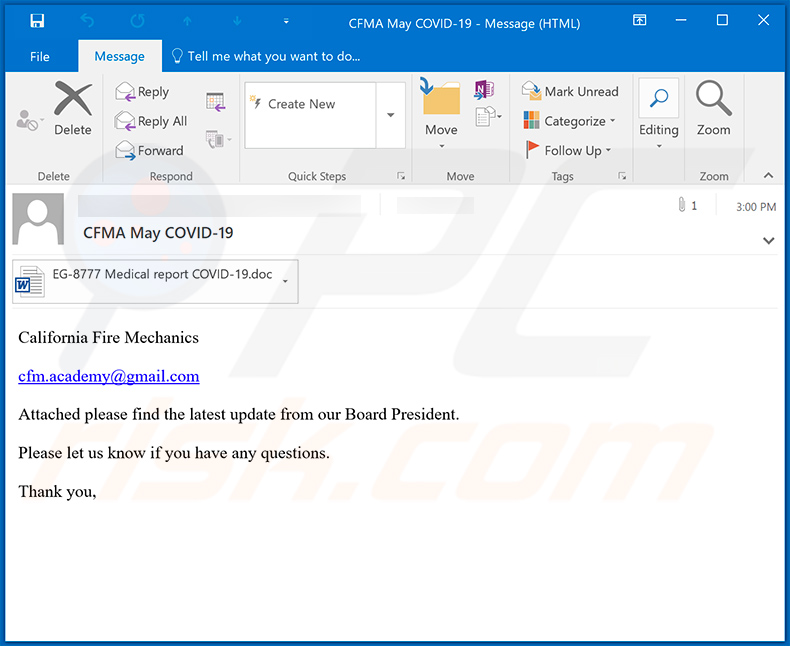
Text presented within:
Subject: CFMA May COVID-19
California Fire Mechanics
cfm.academy@gmail.com
Attached please find the latest update from our Board President.
Please let us know if you have any questions.
Thank you,
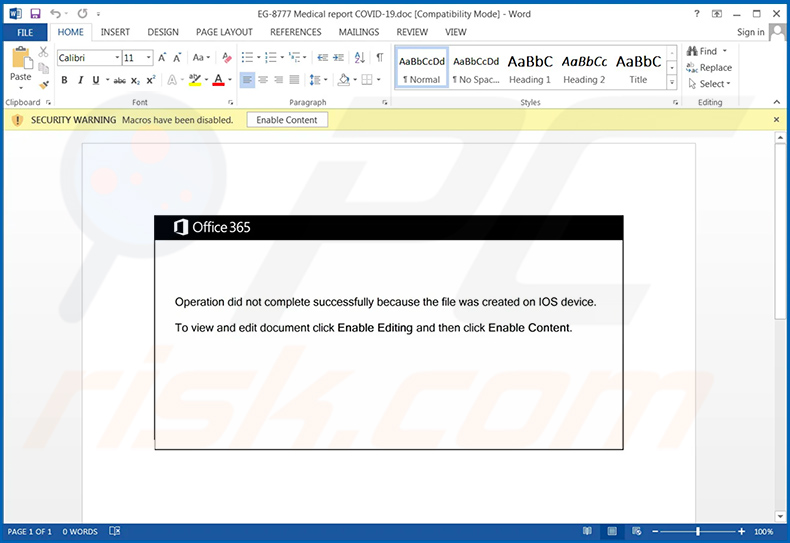
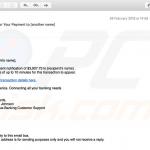
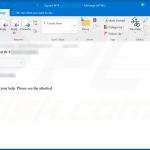
Screenshot of the malicious MS Word document attached to this email:
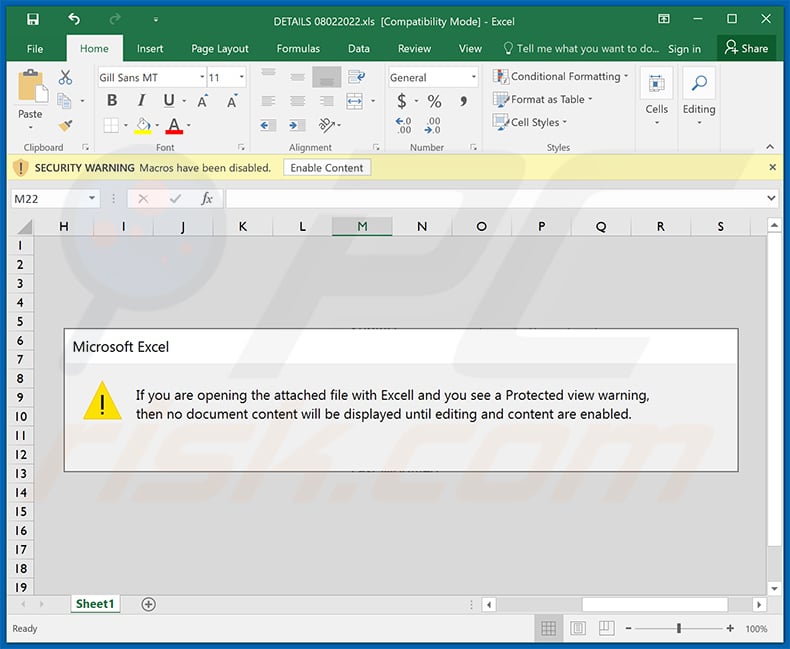
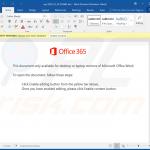
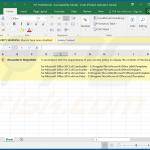
An example of a malicious MS Excel document used to inject Emotet trojan into the system:
Update 9 June 2022 - Now Emotet is capable of injecting a credit card stealer module that collects cardholder name, expiration date, card numbers, and other details stored in Google Chrome user profiles. After collecting data, Emotet sends stolen information to C2 servers.
Update September 19, 2022 - Emotet's botnet is now being used to install a Cobalt Strike beacon on infected computers (as a second-state payload) and distribute ransomware. Now cybercriminals use Emotet to spread Quantum and BlackCat ransomware. Before June 2022, Emotet was used to distribute Conti ransomware.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
How to remove malware manually?
Manual malware removal is a complicated task - usually it is best to allow antivirus or anti-malware programs to do this automatically. To remove this malware we recommend using Combo Cleaner Antivirus for Windows.
If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here is an example of a suspicious program running on a user's computer:
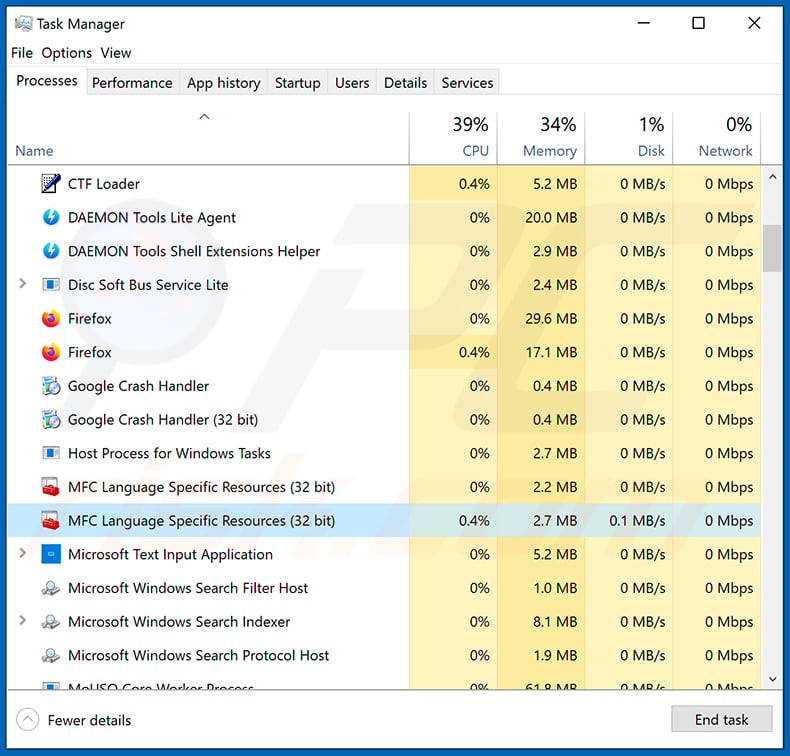
If you checked the list of programs running on your computer, for example, using task manager, and identified a program that looks suspicious, you should continue with these steps:
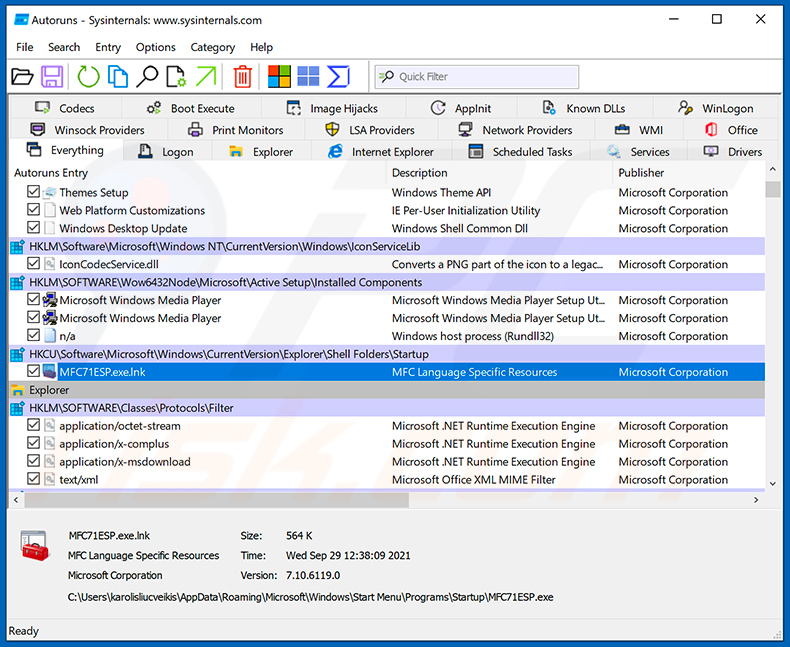
 Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
 Restart your computer into Safe Mode:
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users: Start Windows 8 is Safe Mode with Networking - Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened "General PC Settings" window, select Advanced startup.
Click the "Restart now" button. Your computer will now restart into the "Advanced Startup options menu". Click the "Troubleshoot" button, and then click the "Advanced options" button. In the advanced option screen, click "Startup settings".
Click the "Restart" button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
Video showing how to start Windows 8 in "Safe Mode with Networking":
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click "Restart" while holding "Shift" button on your keyboard. In the "choose an option" window click on the "Troubleshoot", next select "Advanced options".
In the advanced options menu select "Startup Settings" and click on the "Restart" button. In the following window you should click the "F5" button on your keyboard. This will restart your operating system in safe mode with networking.
Video showing how to start Windows 10 in "Safe Mode with Networking":
 Extract the downloaded archive and run the Autoruns.exe file.
Extract the downloaded archive and run the Autoruns.exe file.
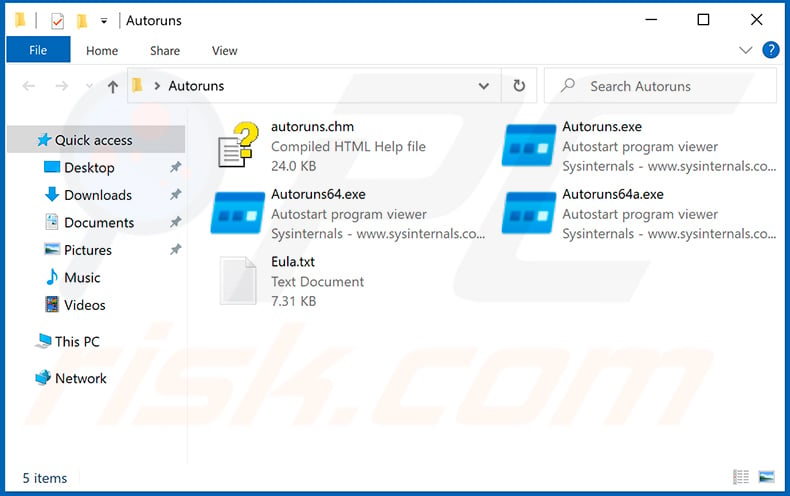
 In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
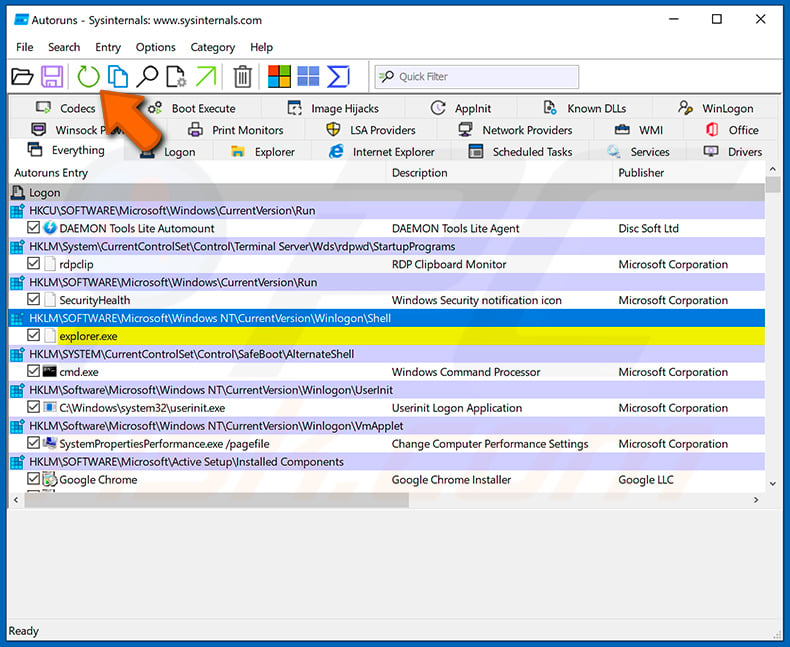
 Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
You should write down its full path and name. Note that some malware hides process names under legitimate Windows process names. At this stage, it is very important to avoid removing system files. After you locate the suspicious program you wish to remove, right click your mouse over its name and choose "Delete".
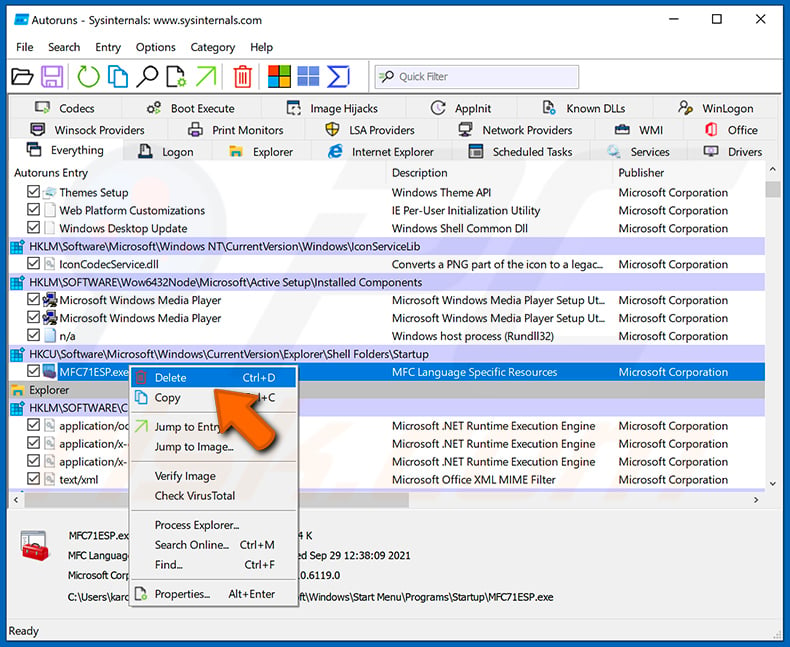
After removing the malware through the Autoruns application (this ensures that the malware will not run automatically on the next system startup), you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the filename of the malware, be sure to remove it.
Reboot your computer in normal mode. Following these steps should remove any malware from your computer. Note that manual threat removal requires advanced computer skills. If you do not have these skills, leave malware removal to antivirus and anti-malware programs.
These steps might not work with advanced malware infections. As always it is best to prevent infection than try to remove malware later. To keep your computer safe, install the latest operating system updates and use antivirus software. To be sure your computer is free of malware infections, we recommend scanning it with Combo Cleaner Antivirus for Windows.
Frequently Asked Questions (FAQ)
My computer is infected with Emotet malware, should I format my storage device to get rid of it?
No, Emotet can be removed without formatting.
What are the biggest issues that Emotet malware can cause?
Emotet has information-stealing abilities, and it can inject other malware into systems. The latter makes the threats posed by this trojan especially broad. In general, malware infections can lead to decreased system performance or failure, permanent data loss, hardware damage, severe privacy issues, financial losses, and identity theft.
What is the purpose of Emotet malware?
Most malware attacks are designed to generate revenue for the cyber criminals. However, malicious programs can also be released for the criminals' amusement, process disruption (e.g., website, service, company, organization, etc.), personal vendettas (i.e., targeting specific individuals), political/geopolitical motivations, and so on.
How did Emotet malware infiltrate my computer?
Emotet has been observed being proliferated using various techniques. The most common methods used to distribute malware include: spam mail, drive-by (deceptive and stealthy) downloads, unofficial and freeware download websites, Peer-to-Peer sharing networks, online scams, illegal software activation tools ("cracks"), fake updates, and so forth. Some malicious programs are capable of self-spreading via local networks or removable storage devices (e.g., external hard drives, USB flash drives, etc.).
Will Combo Cleaner protect me from malware?
Yes, Combo Cleaner can detect and eliminate most of the known malware infections. It must be stressed that performing a full system scan is paramount - since high-end malicious software tends to hide deep within systems.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate

▼ Show Discussion