Ransomware Attack on Israeli Websites Fails Horribly
Over the past weekend, hackers launched a ransomware campaign in an attempt to infect millions of Israelis. Based on current evidence it is believed that the hackers are operating out of Palestine and may be affiliated with the #OpIsreal campaigns. OpIsreal forms part of nearly yearly cyber-attacks against the Government of Israel as well as private websites operated from Israel. The main goal of the annual campaign is “erasing Israel from the Internet”. Popularity and public support behind the campaigns have been decreasing steadily over the years. According to SenseCy participants in the campaigns have decreased steadily from over 6000 in 2014 to just 600 in 2017.
While popularity for OpIsrael is on the decline, the group has experienced some successful campaigns, mainly the denial of service attacks on Israeli websites in 2013, in protest to Israel’s policies regarding Palestine. If the latest ransomware campaign is indeed part of OpIsrael, it might signify a switch in tactics from hacktivism to merely cybercrime devoid of a moral imperative. On March 2, 2019, hackers successfully poisoned DNS records for Nagich, a web service that provides an accessibility widget that is embedded on thousands of Israeli websites to provide access for persons with reading disabilities. Hackers then used the widget to automatically embed malicious code on thousands of Israeli websites. The code would first publish the message “#OpJerusalem, Jerusalem is the capital of Palestine,” then proceed to initiate an automatic download for a Windows file named “flashplayer_install.exe” a file tainted with ransomware.
The first phase of the attack, mainly the publishing of the message, was successful. The message was published on thousands of web pages including some of the biggest news sites in Israel. However, the distribution of the JCry ransomware was far less successful, in fact for the hackers it can be regarded as a dismal failure. When security researchers analyzed the code they found that due to a coding error the auto-download of the ransomware. According to an article published by CyberArk, the download would not happen due to a simple print message bug within the code.
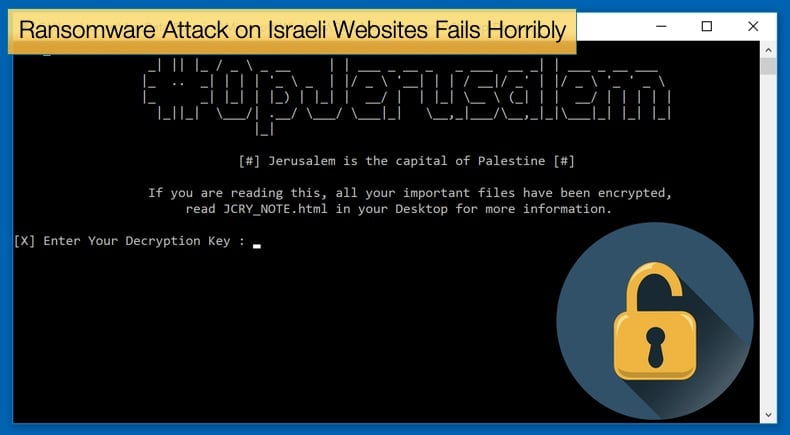 This mistake resulted in the malicious code would not stop after the defacement, and thus not trigger the ransomware download if the OS version would be a string different from “Windows.” This is an issue because there is no user-agent string of “Windows” alone, as browser user-agent strings also include the Windows version number, such as “Windows XP” or “Windows 10.” In more technical terms this meant that the code would always return that the statement is true. This means that regardless of the operating system, the malicious code performed the defacement and then stopped, aborting the download on purpose.
This mistake resulted in the malicious code would not stop after the defacement, and thus not trigger the ransomware download if the OS version would be a string different from “Windows.” This is an issue because there is no user-agent string of “Windows” alone, as browser user-agent strings also include the Windows version number, such as “Windows XP” or “Windows 10.” In more technical terms this meant that the code would always return that the statement is true. This means that regardless of the operating system, the malicious code performed the defacement and then stopped, aborting the download on purpose.
Software developers might have a chuckle at this as it is a bug they have probably come across numerous times and solved rather simply. As to the ransomware used according to CyberArk the malware was of a nondescript nature that would have encrypted files if users ever ran it. The Nagich attack lasted only a few hours on Saturday and the service regained access to its DNS records and stopped delivering the malicious code by the end of the day.
Where does hacktivism end and cybercrime begin?
While the attack was fundamentally a failure, the politically orientated message can certainly be regarded as a form of hacktivism. The act of hacking systems as a form of protest, known as hacktivism, is often associated with groups fighting for freedom of speech, freedom of movement, and the promotion of human rights. The term was coined in 1994 by a Cult of the Dead Cow (CDC) member known as "Omega" in an e-mail to the group. Due to the variety of meanings of its root words, hacktivism is sometimes ambiguous and there exists significant disagreement over the kinds of activities and purposes it encompasses. Some definitions include acts of cyberterrorism while others simply reaffirm the use of technological hacking to effect social change. Due to the ambiguous nature of the term and it means different things to different people it becomes increasingly hard to argue about the morality of such activities.
In recent years there have been attempts to compare hacktivists to cyber terrorists. This may be an extreme reaction to something that is fundamentally an irritant rather than life-threatening. In an article published via Stanford’s online resource platform places strict boundaries on hacktivism and defines it as,
“Hacktivism, according to information security researcher Dorothy Denning, is "the marriage of hacking and activism." More precisely, it is the use of computer technology to achieve a political agenda through legally ambiguous means. Acts of hacktivism generally obstruct normal computer activity in some way, and does not cause injury or significant monetary loss.”
The question remains then if “hacktivists” then use malware typically used by cybercriminals to turn a profit, in this case, ransomware, can there act still be regarded as a legitimate form of activism.
Going by the definition provided above despite the message supporting Palestinian interests the above falls outside the limits of hacktivism. It is not sure yet if the ransomware issued a ransom note that demanded a fee for decryption if successfully downloaded. If this was the intention of the hackers their actions should not be considered hacktivism. Even if no ransom was demanded as whether this is hacktivism or not can be answered in the negative as the act of restoring data can be a significant expense, thus resulting in a monetary loss. Rather the message displayed on websites, the successful part of the hack, can be seen as an attempt to add moral authority to an immoral act.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion