Aluminum Giant Hit by Ransomware
On March 19, 2019, Norwegian aluminum production giant Hydro announced that it had suffered a cyber-attack. Further, the company announced that it was a ransomware infection that affected the entire company. This can be seen as a major cybersecurity event as, since the start of 2019, there have not been major ransomware incidents that targeted companies which led to the company having to shut down operations to any degree. This attack also further illustrates how hackers using ransomware have changed tactics targeting government organizations and large companies. Earlier in March Jackson County in the US has hit by a ransomware attack which shut down local government websites, however, the potential cost of the Hydro incident will pale in comparison when loss of earnings and other factors are considered.
According to Hydro’s security team, an odd occurrence occurred on the company’s server at approximately midnight. It was soon determined that what appeared at first odd was a malware infection, which the security team looked to contain. Unfortunately, they only managed to partially contain the infection preventing it from infecting the plants. By that time the infection had spread across the company’s global network. No comment was made as to how many computers were infected, it can safely be assumed lots as the company employs approximately 35,000 people. Currently the full extent of the infection is unknown, however, the company’s power plants were not affected as these are deemed to be critical infrastructure and completely separate from the main network. Unfortunately for the company, the smelting plants were not separate from the main network due to becoming increasingly automated. The security team managed to prevent any lasting damage to the smelting plants it would seem and even managed to make some of them fully operational, although in a slower, semimanual mode. In a press statement, Hydro said, “lack of ability to connect to the production systems caused production challenges and temporary stoppage at several plants.”
The attack could have been far worse but thanks to the quick reactions from the security team the attack did not cause a complete stop to all operations. Although Windows machines were encrypted and rendered useless, the phones and tablets not based on Windows continued to work, which gave employees the ability to communicate and respond to business needs. The expensive critical infrastructure such as baths for aluminum production, which cost about 10 million EUR each, do not seem to have been affected by the attack. The security incident caused no safety problems and the company hopes to be able to restore all data from its backups. The exact ransomware used by the attackers is not yet known. It is believed by some that the ransomware used may have been LockerGoga, a relatively new piece of ransomware.
LockerGoga
One of the first instances where LockerGoga was seen in the wild occurred when Altran Technologies reported that they had suffered a ransomware attack. The French engineering consultancy released a public statement informing the public of the incident but it was light on details saying that third-party technical experts and digital forensics specialists are on the case. It was believed at the time by security researchers that the malware used was LockerGoga with researchers believing it to be similar to a malware sample uploaded to Virus Total from Romania on January 24. Initially, MalwareHunterTeam named the ransomware after the path used for compiling the source code into an executable upon its discovery by the researchers. When researchers analyzed the malware was found to be very slow due to how it spawned another process each time it encrypted a file. It was also concluded that the code itself was sloppy and made no effort to evade detection.
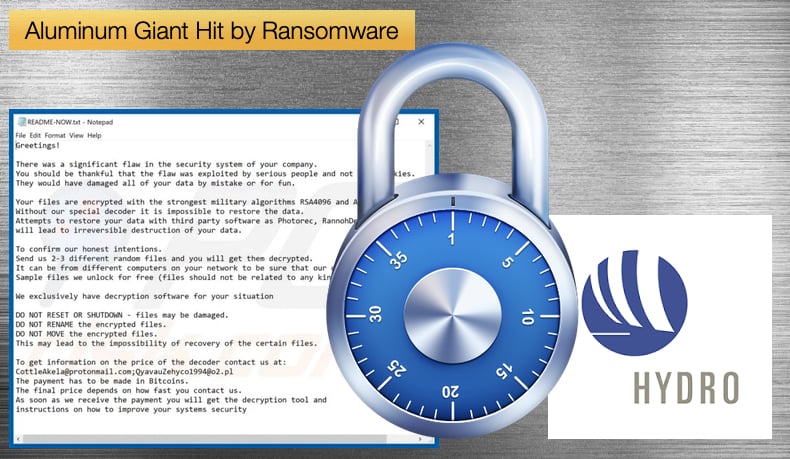
The ransomware once executed will encrypt DOC, DOT, WBK, DOCX, DOTX, DOCB, XLM, XLSX, XLTX, XLSB, XLW, PPT, POT, PPS, PPTX, POTX, PPSX, SLDX, and PDF files. When security researchers analyzed the malware they found that when encrypting files, the ransomware will append the .locked extension to encrypted file's names. They also found that the encryption process was slow due to the fact that the ransomware spawned a new process every time it encrypted a file. When done encrypting data on the computer, it will drop a ransom note named README-NOW.txt on the desktop, which includes instructions to contact the CottleAkela@protonmail.com or QyavauZehyco1994@o2.pl email addresses for payment instructions.
Security researchers believe that LockerGoga was used in the Hydro incident despite the company been unwilling to share those details with either the public or the media. An alert was issued by NorCERT, Norway's cybersecurity body, via the Norwegian news outlet NRK. The alert stated,
“NorCERT warns that Hydro is exposed to a LockerGoga attack. The attack was combined with an attack on Active Directory (AD),”
However, Håkon Bergsjø, head of NorCERT, would not confirm for NRK that the attack targeted Active Directory servers in the case of Norsk Hydro.
Both attacks illustrate ransomware’s shift from targeting the individual to targeting business and other organizations. Admins of IT departments or those in charge of an organizations security must see these developments as a threat and ensure the organization as a whole is making use of a good backup policy. In an article published by Kaspersky, the realities of recovering encrypted data are not confidence inducing. In summary, the article states,
“…there are companies that are constantly looking for ways to restore encrypted data — including us. However, deciphering information is possible only if the attackers were not professional enough to implement a normal algorithm (or if they simply made a mistake somewhere). When we manage to make a decryption tool, we share it free at https://noransom.kaspersky.com/. But such cases are exceptions, not the rule.”
Pointing out that odds of being able to decrypt data are stacked against the victim. The article concluded that prevention is the only viable protection against such infections.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion