Jackson County Forks Out $400,00 for Ransomware Payment
It was a commonly held belief that hackers using ransomware would only go after private individuals. When WannaCry struck this belief was well and truly shattered. Increasingly hacker groups are seeing the value of attacking government organizations, hospitals, and companies. One of the reasons for this is that, particularly in the case of government departments and organizations, the systems are large, sometimes complex, and often using software that is no longer supported by the manufacturers. Jackson County, a rural area in Georgia, USA, has experienced this the hard way after suffering a ransomware attack, of which, they paid the hackers 400,00 USD for the decryption key just to have access to critical infrastructure.
On March 1 news reports began surfacing that Jackson County had suffered a ransomware attack which affected the county’s internal networks. According to Jackson County’s website, a civic alert notified the public that most of their systems were offline. Fortunately for emergency operators the systems assisting the 911, emergency services were unaffected by the attack. In an interview with StatesScoop Sheriff, Janis Mangum stated,
“Everything we have is down. We are doing our bookings the way we used to do it before computers. We're operating by paper in terms of reports and arrest bookings. We've continued to function. It's just more difficult.”
In an effort to recover from the attack county officials followed best practices by informing the Federal Bureau of Investigation (FBI) and hired a cybersecurity consultant.
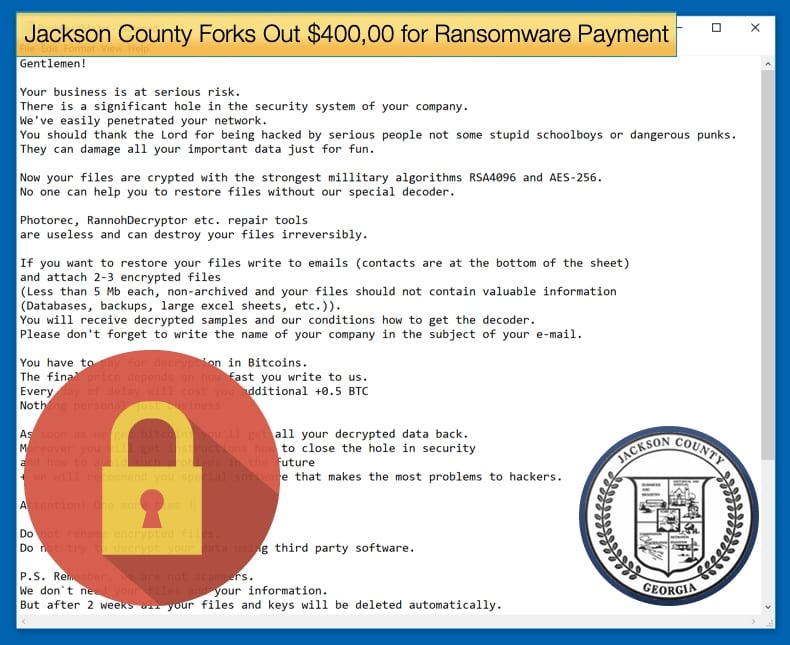
The consultant negotiated with the ransomware operators, and earlier this week the county paid 400,000 USD to hackers to get a decryption key and re-gain access to their ransomed files. Since then county officials have been busy decrypting affected computers and servers. Jackson County Manager Kevin Poe told Online Athens in an interview,
“We had to make a determination on whether to pay. We could have literally been down months and months and spent as much or more money trying to get our system rebuilt.”
This is generally the difficult question all victims have to answer when infected with ransomware. In the case of the City of Atlanta attack, the ransom was not paid but the costs resulting from the attack were estimated to be roughly 2.6 million USD. Recently legal opinion has surfaced that suggests paying of a ransomware ransom may violate US sanctions. It is unknown to the writer if the security consultant hired by the county was aware of this or not. If this legal opinion if verified in a court of law and ransom payments are indeed in violation of sanctions the county could be in a spot of bother. Courts traditionally do not see expediency and the saving of money as a valid excuse or legal defense for funding criminal enterprises.
Ryuk Gang may be Responsible
Very little is known about the details of the attack, however, in the interview answered by Kevin Poe, he identified the ransomware as Ryunk. As to specific ransomware named Ryunk, the writer could neither think of one nor find one. However, the similarities between Ryunk and the infamous Ryuk are fairly obvious. If indeed it is Ryuk this would add to the argument to pay the ransomware as it is currently undecryptable. The gang is believed to operate out of Eastern Europe and has developed a reputation for going after departments and organizations in an attempt to secure bigger payouts as the costs associated with data recovery are far higher than an individual personals computer.
Since the start of the year, those behind Ryuk have looked to partner with other malware developers to improve their arsenal and ensure more high-value infections. To this extent, the gang partnered with the creators of TrickBot which is a trojan which is under constant development in order to defeat antivirus packages and other anti-malware software packages. Since then Ryuk deployment tactics involve the downloading of the ransomware only once TrickBot has gained a foothold onto the targeted network. In the Jackson County attack it is unsure how exactly the hackers gained access to the networks, perhaps in time published audits and reports will reveal that it was indeed Ryuk.
The Jackson County attack will reignite the debate as to whether one should pay the ransom or not. If it was merely a matter of saving time and costs then answering in the affirmative is an easier decision to make. However, life is never easy and such choices are never black and white. The Ryuk gang is known for running a professional if illegal services, meaning that if you’ve been infected with Ryuk the odds of them decrypting the files after are good. They are also willing to negotiate as to the price to help ensure the “sale” of their service. However, many hackers using numerous strains of ransomware do not have the capabilities to decrypt already encrypted files. Paying the ransom then will not solve the problem. Paying the ransom even when sure you will gain access to your system once more is funding criminal organizations and opens the further legal debate. Depending on the laws of a country or state this in itself may be illegal and could possibly result in the victim been labeled criminal.
These are all things that victims need to consider when deciding whether to pay or not. This is a decision that could have many unforeseen consequences. To that effect, it is often advised by authorities and security researchers alike not to pay the ransom. Rather it is safer to ensure all software is up to date, regular backups are made, and users use a reputable antivirus package. These have proved effective measures in combatting ransomware and preventing infections. If the infection is prevented then there is no need to attempt to answer the difficult question, “should we pay, or not?”
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion