Bitcoin Scam Leads to Ransomware Infections
According to security researcher going by the pseudonym Frost, a bunch of websites is pushing a download which promises users the ability to earn up to 30 USD in Bitcoin daily. The program, called Bitcoin Collector, is nowhere near what it is advertised to be, rather it is a scam which will infect systems with ransomware and an information harvesting trojan. This is most certainly not what the user, now victim, had in mind when downloading the program they hoped would earn them a nice daily sum. Bitcoin is currently enjoying a surge in value with at the time of writing 1 BTC is 8,730 USD. This surge in recent value has been attributed to a variety of factors including accumulation of the cryptocurrency and unspent coin been at record highs. Regardless of the reasons, it will still mean that Bitcoin and other cryptocurrencies including Ethereum and Monero are still worth stealing and been exploited to lure unsuspecting victims.
Part of the scam incorporates a referral program which allows users to earn Ethereum for referring a set number of new users. The FAQ on one of the websites states that by referring 1,000 visits using your referral link you will earn 3 Ethereum. That is approximately worth 750 USD currently. This, however, is not the crux of the scam. Rather it is the download provided on the website which promises daily earnings of Bitcoins. These earnings are supposedly given free and are automatically paid out. If a potential victim clicks on the offer they are redirected to another website controlled by those behind Bitcoin Collector. Here the potential victim is offered a download which will download and install the money-making application. To further sell the legitimacy of the scam the scammers have even gone so far as to link a Virus Total detection page in an attempt to prove that it is not malicious.
Beware, even though there are no malicious detections this should not be taken at face value. It has been confirmed that the file downloaded is indeed a trojan. If a user downloads the file they might discover that numerous files are downloaded with one being BotColletor.exe. Once that file is executed it will launch a program called "Freebitco.in - Bot" that does not appear to do much. In reality, though, this is a Trojan that pretends to be a bitcoin generator but simply launches a malware payload. Now the user looking to make extra money for what they perceive as the easiest money they’ve probably made has compromised their computer.
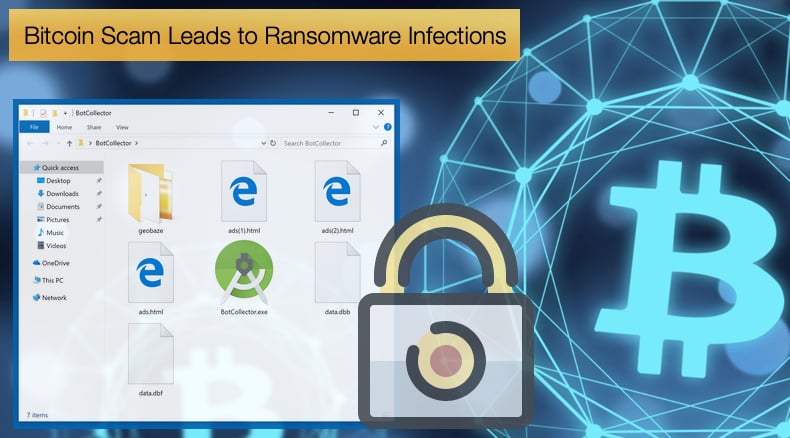
According to Bleeping Computer, when they analyzed the scam when the start button is clicked on what appears to the victim as the user interface, triggers the malware payload. There are two versions of the campaign been conducted by the scammers and depending on the campaign either ransomware is triggered or an information stealing trojan.
Hidden Tear Ransomware
The ransomware that is delivered is Hidden Tear, a ransomware variant that currently has a removal guide on PCrisk. The scam’s operators have labeled the ransomware “Marozka Tear Ransomware” which when run will encrypt your files and append the .Crypted extension and create ransom notes named HOW TO DECRYPT FILES.txt. The ransom note reads as follows,
“All your information (documents, databases, backups and other files) this computer was encrypted using the most cryptographic algorithms.
All encrypted files are formatted .Crypted.
This form files '.Crypted' is a joint development of American Hackers.
You can only recover files using a decryptor and password, which, in turn, only we know.
It is impossible to pick it up.
Reinstalling the OS will not change anything.
No system administrator in the world can solve this problem without knowing the password
In no case do not modify the files! But if you want, then make a backup.
Drop us an email at the address india2lock@gmail.com
You have 48 hours left. If they are not decrypted then after 48 hours they will be removed!!!”
Briefly, Hidden Tear started life as an open source ransomware project which was published on GitHub. It is free to download by anyone meant that hackers quickly took the source code and created numerous variants which include Qinynore, Nog4yH4n Project, IT.Books, OPdailyallowance, ScorpionLocker, Sorry, and Cyber Police. Upon the ransomware’s release, the malware uses an AES-256 encryption algorithm. If the campaign does not install the ransomware payload it installs the Baldr trojan. This piece of malware specializes in stealing passwords. Recent versions of the trojan are also capable of stealing login credentials, taking screenshots, retrieving browser histories, steal files and even steal cryptocurrency addresses.
Detecting scams can be difficult as scammers know which emotional buttons to push in order to lure the unwary. In an article published on Citizens Advice details what users should look out for when they suspect something is a scam. According to the article,
“Don’t click on anything and leave the website. You might want to keep the email as evidence in case you report the scam…If you’ve had an email that looks like it’s from your bank, contact your bank directly using the number on your card. You can also log into your account on their website - use Google to find the real one…You can also block the email sender or mark an email as ‘spam’ or ‘junk’ - this means you won’t see them in your inbox. Check your email provider’s help section for instructions on how to do this.”
As with a lot of internet scams they often sink the lure in by offering something that is too good to be true. Before clicking on any link or downloading a file do a simple Google search. If it is a scam and has been detected there will be articles and websites exposing the scam. There are also a number of online services designed to rate the legitimacy of websites and services.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion