Phishing Campaign Spotted Summoning Users to Court
The tried and tested method of distributing malware via phishing campaigns have always used a variety of tactics to trick users into downloading malware. Whether they entice clicks by tricky the user into believing they have won something or emails sent to business appearing like invoices, there is no end to hackers attempts and imagination. A new campaign has been spotted targeting employees in the insurance and retail industries, sending emails that appear to be from the UK Ministry of Justice but in reality contain a piece of information stealing malware.
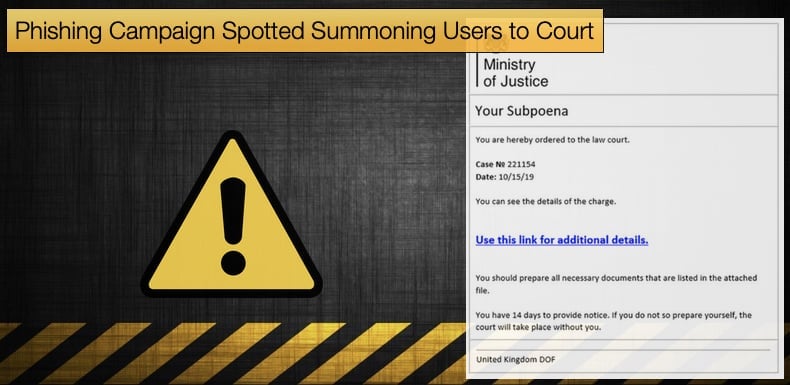
The campaign was discovered by security firm Cofense who published their findings via their blog. Researchers discovered emails that contained the Ministry of Justice logos and had the subject name court. The content of the email claims to have information relating to a court case, in this specific instance the email states it contains information relating to “Your Subpoena”. The shock tactics continue in that the email instructs the user to click the provided link as they are provided to attend a court of law and must comply within 14 days. Other than that there is no information pertaining to the legal matter or which court they are required to attend. It is easy to see why such tactics could scare someone into clicking the link. Finding out you’ve been summoned to court for whatever reason is a stressful affair.
Those behind the campaign have gone to some length to hide the malicious intention of the emails. The link in the emails links to a Google Doc which in turn automatically redirects the user to a Microsoft OneDrive if clicked. The OneDrive delivers a Microsoft Word document to the user. Like with numerous other malware distribution campaigns the Word document will ask the user to enable macros. If enabled the information stealer will be downloaded to the now victims machine via the PowerShell. It is a reminder that macros should not be enabled under any circumstance, by simply saying no users prevent a great number of malware infections distributed via Word documents.
If the user does indeed enable macros, once the malware is downloaded it will connect to a command and control server which will facilitate the stealthy stealing of data. The malware in question has been encountered before by numerous other researchers and is called Predator the Thief, more on this to follow.
Researchers pointed out that whoever is behind the campaign lacks any kind of current legal knowledge. The UK legal systems stopped using the term subpoena on legal documents in 1999, rather since the change the courts refer to the same term as “witness summons”. Errors like this are often a clear indicator that the email in question may be fraudulent. The above example is a technicality but if users are alerted to the fact they may not be so easily shocked into clicking the link. The safest way to defend against such attacks that do not require taking a magnifying glass is to never enable macros when prompted, especially if the email is not sent via a trusted source or appears in any way fraudulent.
Predator the Thief
According to Fortinet’s analysis of the malware, it first surfaced in July 2018 and was not very different from other information stealers sold on underground forums. To be sold the developers realized that ease of use would be important and included and command and control panel as well as an executable builder. In terms of features, it again does not boast anything that novel or new but what it does do meets the requirements of what beginner hackers would want. Features include the ability to steal information from an infected host, steal passwords from browsers, replace cryptocurrency wallets in the buffer, and take photos from the web-camera as well as allowing for separate configuration of any of the above-mentioned features.
The malware was initially developed by a hacker going by the alias “Alexuiop1337” and has since changed their alias to “Kongress_nlt”. Since its creation, it has not changed much according to researchers and was written entirely in C/C++ which is rather unique as the majority of information stealers are written in C#. Even up to April 2019, promotion of Predator the Thief was quite active and is often marketed via a Telegram channel when newer versions are released. Given the constant stream of upgrades, it can be concluded that the malware is still very popular and is frequently purchased by those looking to evade on others' privacy. In later campaigns seen spreading the malware researchers concluded,
“Predator the Stealer in this campaign has not changed much from previous versions, but we have found several new tricks the actor uses for spreading this malware. He uses fake zips and documents. Sometimes very specifically targeted to a victim, and even uses the WinRAR exploit to spread the malware. The payload was packed using a third-party packing tool that utilizes the AutoIT scripting language. Checking the path hardcoded in the script revealed that this “nrjat” actor is experimenting with different malware and stealers.”
Based on the analysis provided by security researchers it is fairly safe to assume that campaigns, and in particular phishing campaigns, spreading the campaign will continue into the near future. Users are advised not to trust any email sent to them as this is still and continues, to be a successful infection vector not only for Predator the Thief but numerous other malware variants.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion