Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is Invoice Email virus?
"Invoice Email Virus" (also known as "Outstanding Invoice Email Virus") is a malspam campaign used to proliferate a high-risk trojan called TrickBot. This campaign shares many similarities with a number of other spam campaigns, such as (for example), eFax, Important Documents IRS, and especially HM Revenue & Customs Outstanding Amount.
The text within these emails might differ, even though the delivered message is essentially identical: the user has supposedly received an invoice (via an MS Word attachment) and must pay. Be aware, however, that the attached file is malicious and designed to download and install TrickBot malware.
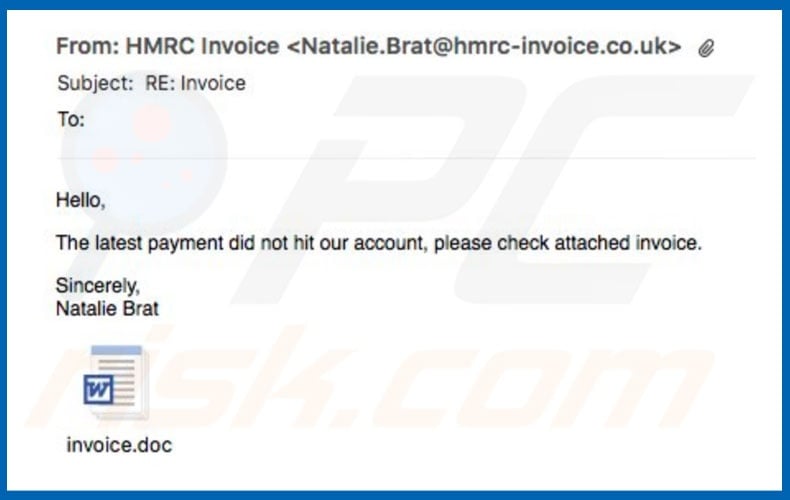
Invoice email virus in detail
As mentioned, the email messages state that payments have not been submitted and encourages users to open the MS Word attachment, which contains an invoice. This is a scam. Cyber criminals attempt to trick gullible users into opening a malicious file that infects the system.
The text in "Invoice Email Virus" campaign emails can vary, since cyber criminals register various web domains and email addresses with the names of legitimate companies and government departments. These URLs/email addresses are then used to send spam - it is easier to give the impression of legitimacy when the sender is familiar to the user.
Be aware that TrickBot is high-risk malware. It hijacks web browsers and collects various logins/passwords. Collected data is sent to a remote server controlled by cyber criminals. These people can receive sensitive information (e.g., criminals might gain access to users' social networks, bank accounts, and so on).
The presence of this malware can lead to significant financial loss or even identity theft. Therefore, data tracking might lead to serious privacy issues or even identity theft.
If you have opened emails/attachments that belong to an "Invoice Email Virus" spam campaign, you should immediately scan the system with a reputable anti-virus/anti-spyware suite and remove all detected threats.
| Name | Invoice spam |
| Threat Type | Trojan, Password stealing virus, Banking malware, Spyware |
| Symptoms | Trojans are designed to stealthily infiltrate victim's computer and remain silent thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software cracks. |
| Damage | Stolen banking information, passwords, identity theft, victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Simimlarities with other Trojans
TrickBot is virtually identical to dozens of other trojan-type viruses, such as Pony, Adwind, FormBook, and many others. As with TrickBot, these viruses are also distributed using spam campaigns. In addition, their behavior is also very similar - all collect data.
Some trojans are also designed to distribute other viruses (typically, ransomware). Therefore, these viruses pose a direct threat to your privacy and Internet browsing safety.
How did Invoice Email virus infect my computer?
"Invoice Email virus" comes together with malicious MS Word attachments presented as invoices. After opening these files, users are asked to enable macro commands, otherwise the content will not be displayed properly. In doing so, however, users grant permission for the attachments to run scripts that stealthily download/install malware.
Note that this will only work if the attachment is opened using the MS Word program. If the file is opened using other software capable of reading these formats, the scripts will not be executed. Furthermore, the malware only targets the Windows Operating System and, thus, users who run other platforms are safe.
How to avoid installation of malware?
The main reasons for computer infections are poor knowledge and careless behavior. Therefore, pay close attention when browsing the Internet. Think twice before opening email attachments. If the file seems irrelevant or has been received from a suspicious/unrecognizable email, it should never be opened - these emails should be deleted without reading.
Furthermore, some trojans are distributed using the "bundling" method (stealth installation of rogue apps together with regular software), and fake updaters. Therefore, be cautious when downloading/installing/updating software. Carefully analyze each window of the download/installation dialogs and opt-out of all additionally-included programs.
Your programs should be downloaded from official sources only, using direct download links. In addition, keep installed applications up-to-date. To achieve this, use implemented features or tools provided by the official developer only. We also strongly recommend that you have a legitimate anti-virus/anti-spyware suite installed and running.
More recent versions (2010 and above) of MS Office open newly-downloaded files in "Protected Mode", thereby preventing malicious attachments from downloading/installing malware. Therefore, you are strongly advised to avoid using old versions. The key to computer safety is caution.
If you have already opened the malicious attachment, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Examples of messages presented in different variants of this malicious email messages:
Subject: RE: Outstanding INVOICE BIA/066250/5423
The invoices came to us very late. Both are enclosed in attachement.
hxxp://www.perezdearceycia.cl/
alexa.ballantine@gmail.com
------------------------------------------------------
Subject: INCORRECT INVOICE
We are waiting for the confirmation from your side so that we can send you the Invoice & Credit card link to process the payment and start the services. If you have any queries, please feel free to contact us. We hope for a positive reply.
hxxp://cqfsbj.cn/
This message is confidential and/or contains legally privileged information. It is intended for the addressees only.
Jamacapq@sbcglobal.net
------------------------------------------------------
Subject: Outstanding INVOICE XOJR/7763411/6403
We have not received payment or an update on when the overdue invoices will be paid. Our payment terms are strictly 30 days. Please let me know when these invoices will be paid. Please see below the list of overdue invoices:
hxxp://minami.com.tw/
Regards
Priyanka Kapadia
------------------------------------------------------
Subject: Outstanding INVOICE FQOVN/2773110/730
Please see below the list of overdue invoices, of which 223.00 euro is due since last month. Can you please advise when payment will be made.
hxxp://www.legionofboomfireworks.com/
This message is confidential and/or contains legally privileged information. It is intended for the addressees only.
Thanks
Kira Holden
------------------------------------------------------
Subject: Invoice Number 55057
Last one year we started to charge for CRB check. They pay us first and we apply for CRB. =0DI do not have invoices.
hxxp://www.caglarturizm.com.tr/
Kind Regards,
andy
------------------------------------------------------
Subject: Final Account
Please find attached your confirmation documents. What you need to do Urgently Print off, sign and scan/send back the full proposal form within 7 days
hxxp://www.jxprint.ru/
Many Thanks
CYNTHIA HARRY
Malicious attachment distributed via "Invoice Email SPAM" campaign:

Example of yet another invoice-themed spam email delivered in Portuguese language:
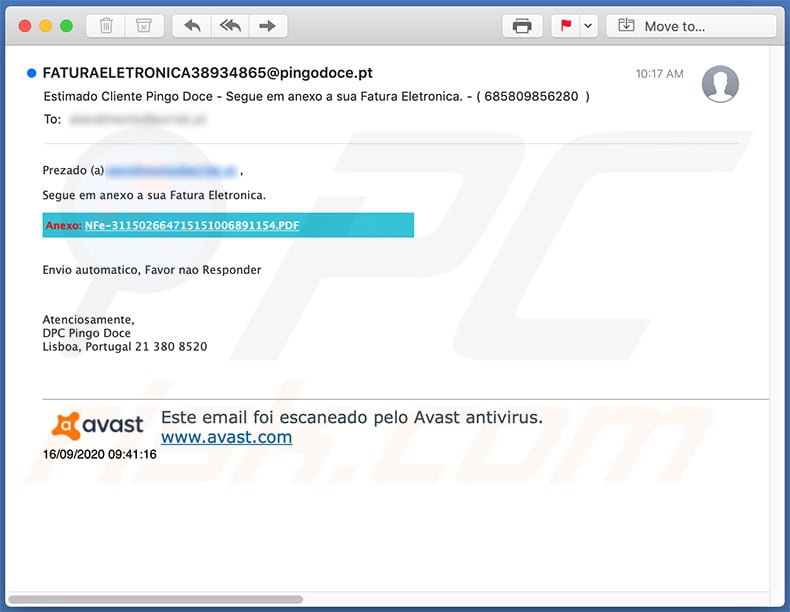
Text presented within:
Subject: Estimado Cliente Pingo Doce - Segue em anexo a sua Fatura Eletronica. - ( 685809856280 )
Prezado (a) atendimento@pcrisk.pt ,
Segue em anexo a sua Fatura Eletronica.
Anexo: NFe-311502664715151006891154.PDF
Envio automatico, Favor nao Responder
Atenciosamente,
DPC Pingo Doce
Lisboa, Portugal 21 380 8520
Este email foi escaneado pelo Avast antivirus.
www.avast.com16/09/2020 09:41:16
Another invoice-themed spam email used to spread a malicious MS Excel document:
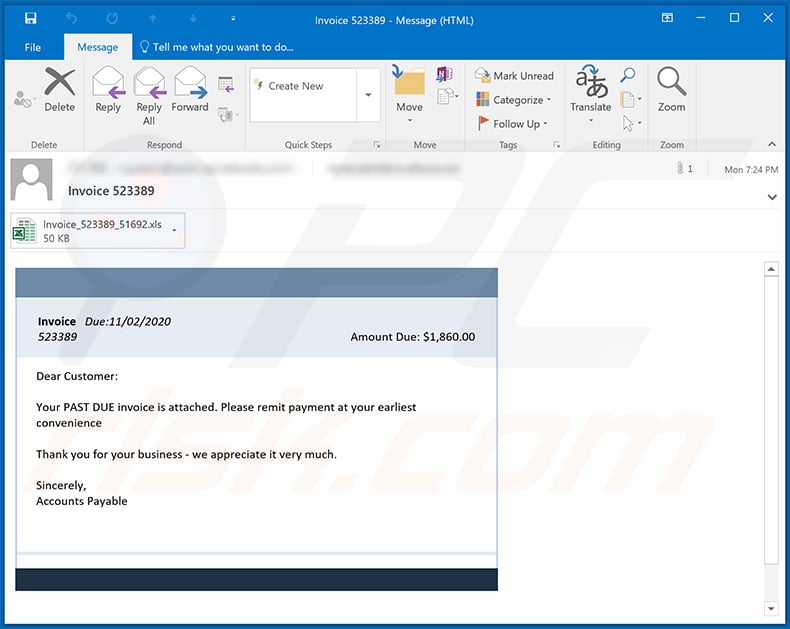
Text presented within:
Subject: Invoice 523389
Invoice Due:11/02/2020
523389 Amount Due: $1,860.00Dear Customer:
Your PAST DUE invoice is attached. Please remit payment at your earliest convenience
Thank you for your business - we appreciate it very much.
Sincerely,
Accounts Payable
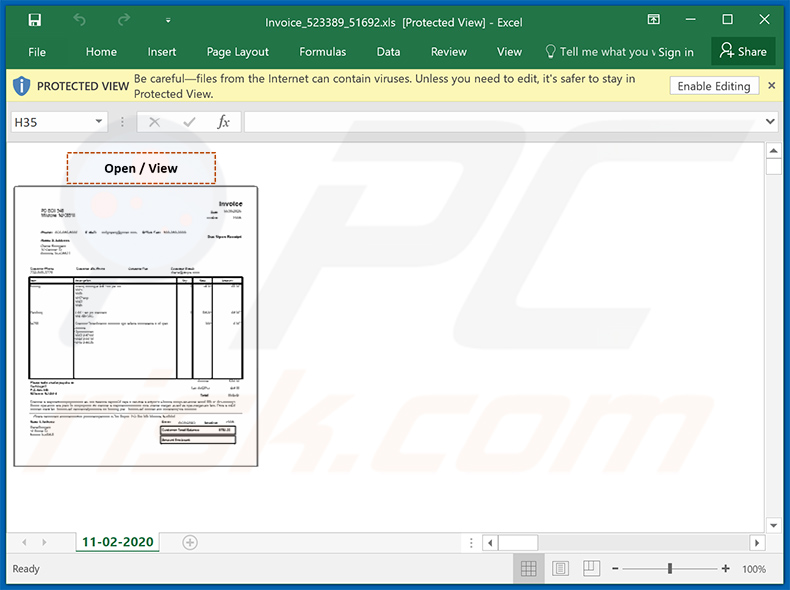
Screenshot of the attached malicious MS Excel document:
Example of yet another invoice-themed spam email used to spread a malicious MS Excel document which injects Dridex malware into the system:
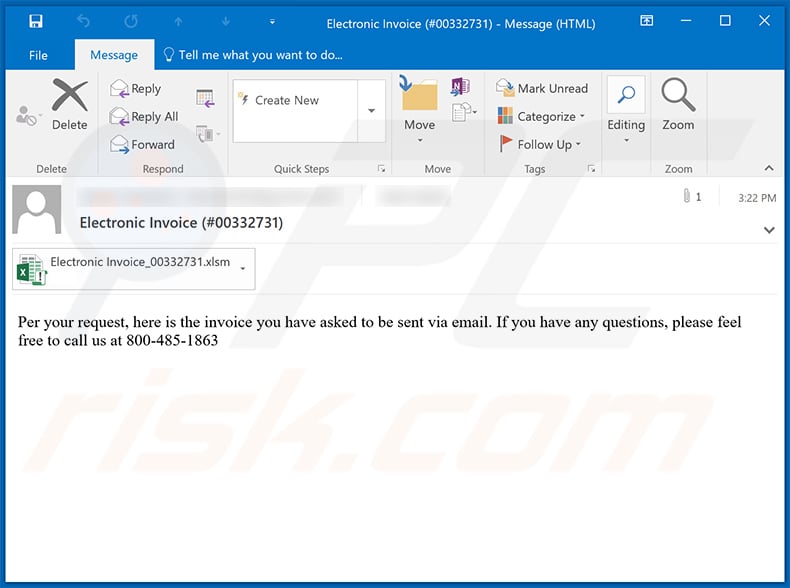
Text presented within:
Subject: Electronic Invoice (#00332731)
Per your request, here is the invoice you have asked to be sent via email. If you have any questions, please feel free to call us at 800-485-1863
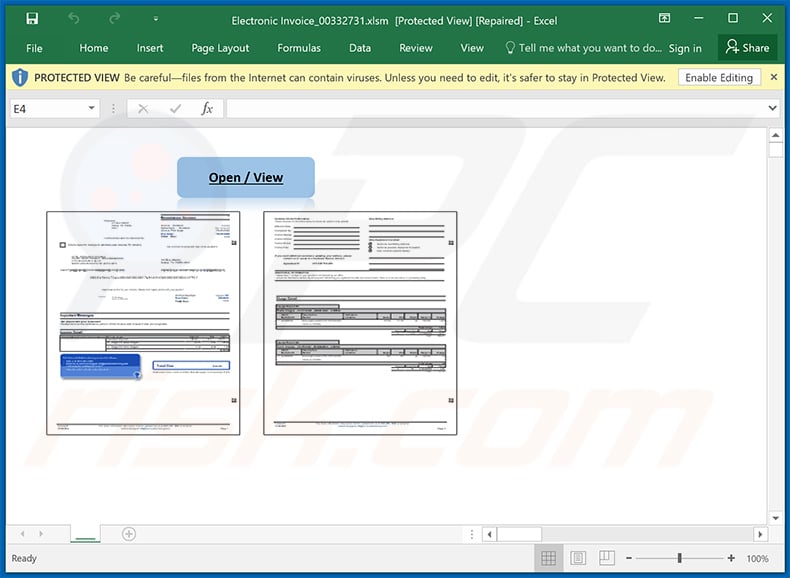
Screenshot of the attached MS Excel document:
Yet another invoice-themed spam email used to spread a malicious .IMG file (the links within lead to the download of said file):
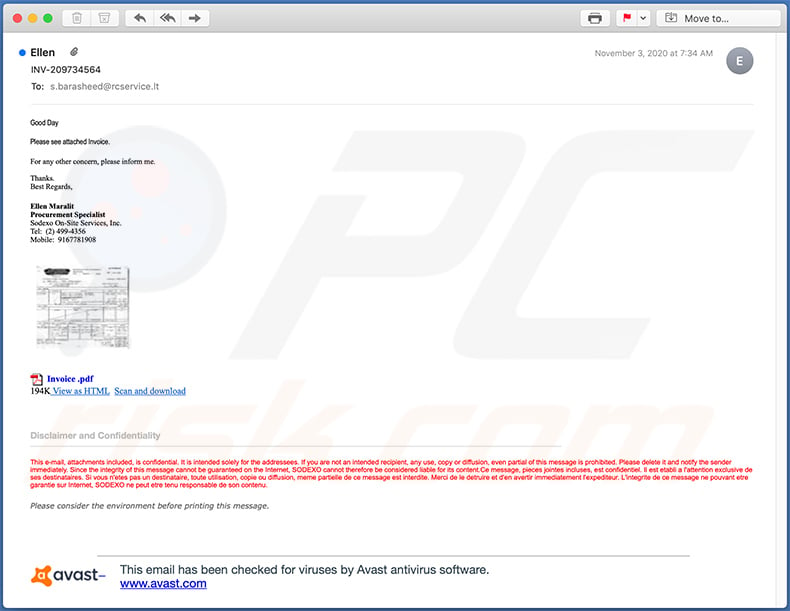
Text presented within:
Subject: INV-209734564
Good Day
Please see attached Invoice.
For any other concern, please inform me.
Thanks.
Best Regards,
Ellen Maralit
Procurement Specialist
Sodexo On-Site Services, Inc.
Tel: (2) 499-4356
Mobile: 9167781908
pdf.gif Invoice .pdf
194K View as HTML Scan and download
Disclaimer and Confidentiality
This e-mail, attachments included, is confidential. It is intended solely for the addressees. If you are not an intended recipient, any use, copy or diffusion, even partial of this message is prohibited. Please delete it and notify the sender immediately. Since the integrity of this message cannot be guaranteed on the Internet, SODEXO cannot therefore be considered liable for its content.Ce message, pieces jointes incluses, est confidentiel. Il est etabli a l'attention exclusive de ses destinataires. Si vous n'etes pas un destinataire, toute utilisation, copie ou diffusion, meme partielle de ce message est interdite. Merci de le detruire et d'en avertir immediatement l'expediteur. L'integrite de ce message ne pouvant etre garantie sur Internet, SODEXO ne peut etre tenu responsable de son contenu.
Please consider the environment before printing this message.
Avast logo
This email has been checked for viruses by Avast antivirus software.
www.avast.com
Yet another invoice-themed spam email used to spread a malicious MS Excel document which injects Dridex malware into the system:
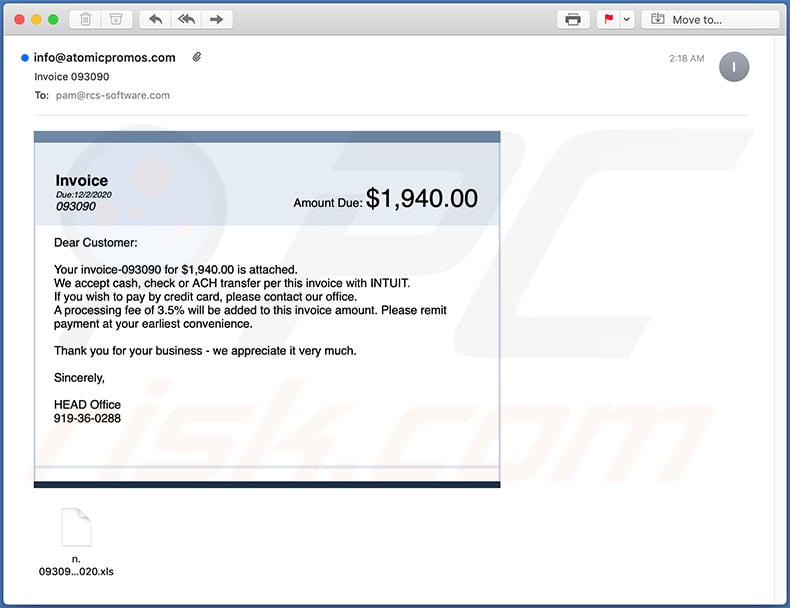
Text presented within:
Subject: Invoice 093090
Invoice
Due:12/2/2020
093090
Amount Due: $1,940.00
Dear Customer:Your invoice-093090 for $1,940.00 is attached.
We accept cash, check or ACH transfer per this invoice with INTUIT.
If you wish to pay by credit card, please contact our office.
A processing fee of 3.5% will be added to this invoice amount. Please remit payment at your earliest convenience.Thank you for your business - we appreciate it very much.
Sincerely,
HEAD Office
919-36-0288
Screenshot of the attached MS Excel document:
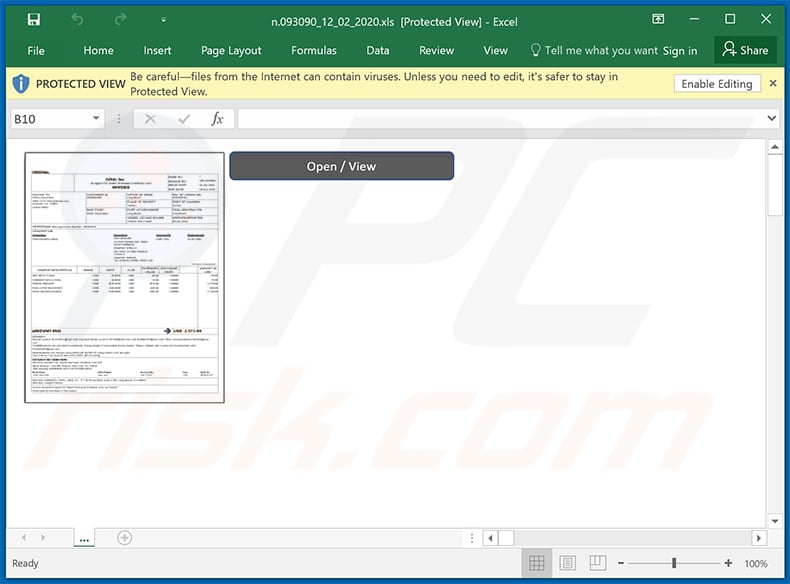
Yet another variant of invoice-themed spam email:
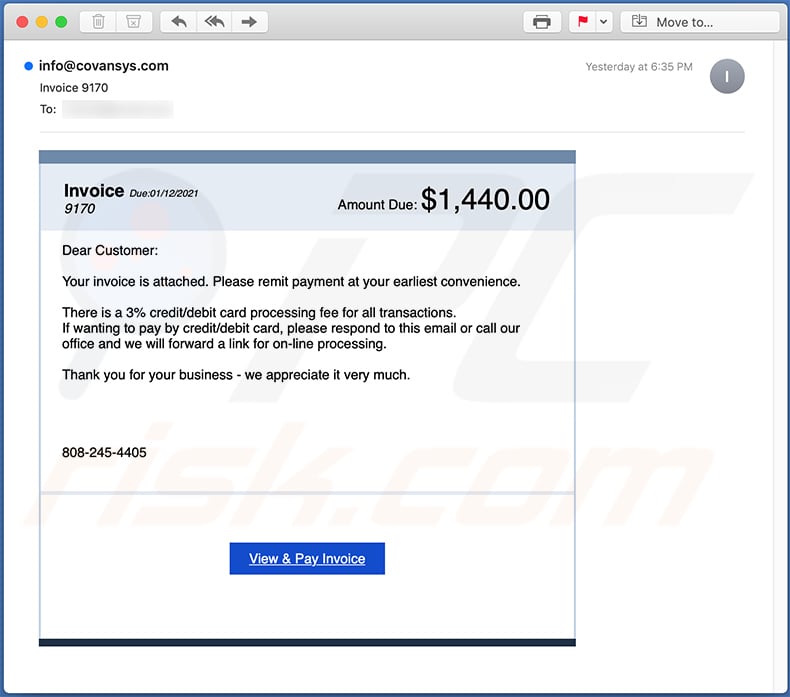
Text presented within:
Subject: Invoice 9170
Invoice Due:01/12/2021
9170
Amount Due: $1,440.00
Dear Customer:Your invoice is attached. Please remit payment at your earliest convenience.
There is a 3% credit/debit card processing fee for all transactions.
If wanting to pay by credit/debit card, please respond to this email or call our office and we will forward a link for on-line processing.Thank you for your business - we appreciate it very much.
808-245-4405
View & Pay Invoice
A Spanish variant of invoice-themed spam email promoting a phishing website:
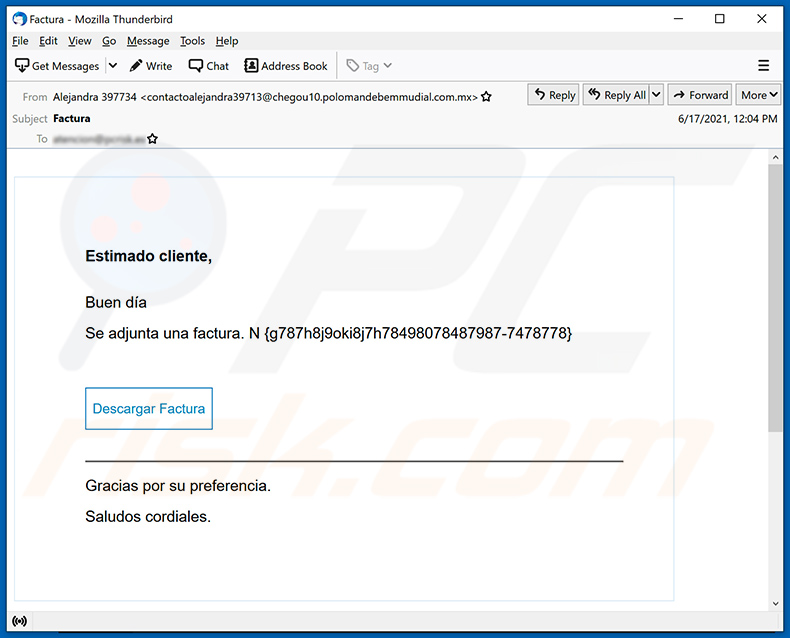
Text presented within:
Subject: Factura
Estimado cliente,
Buen día
Se adjunta una factura. N -Descargar Factura
Gracias por su preferencia.
Saludos cordiales.
Yet another example of invoice-themed spam email used to spread malware:
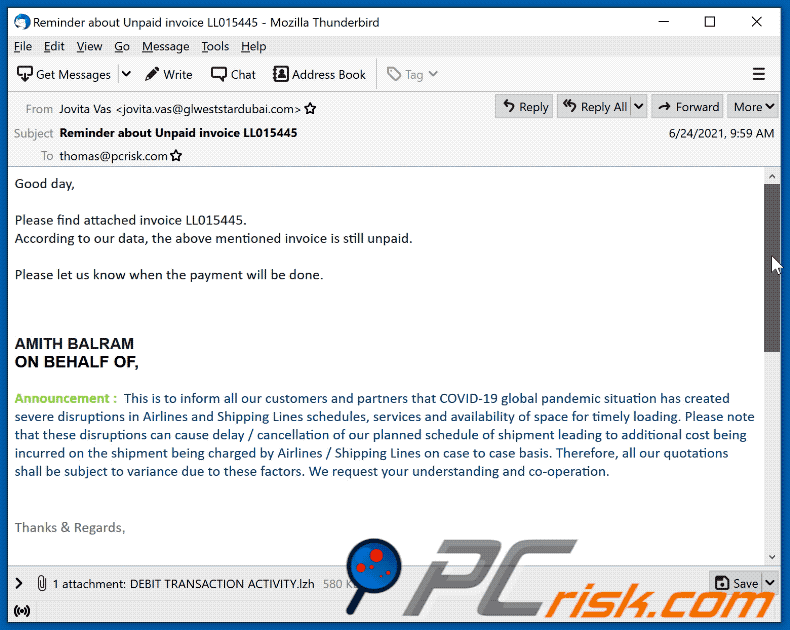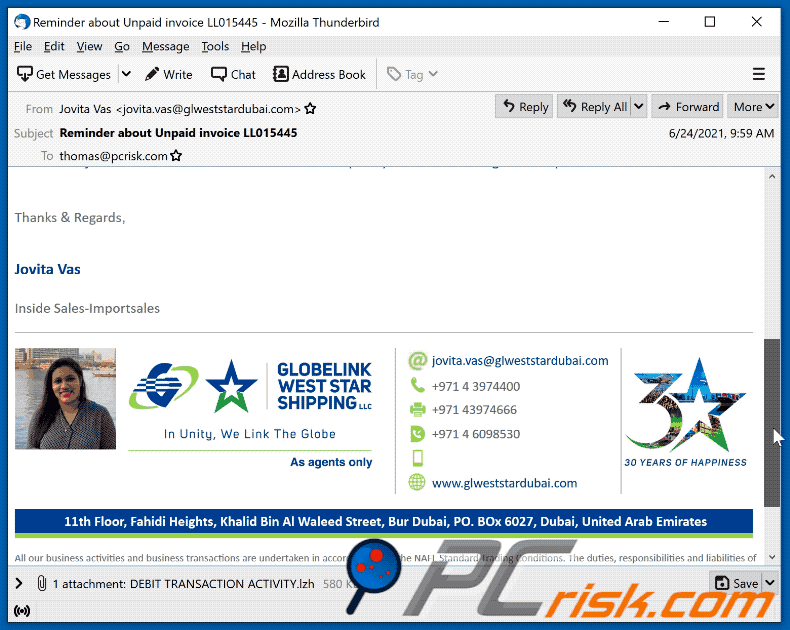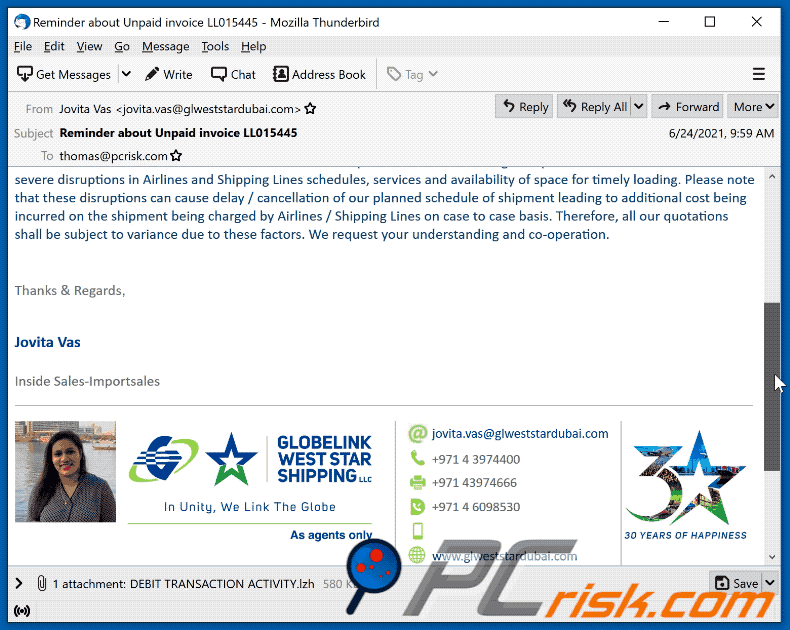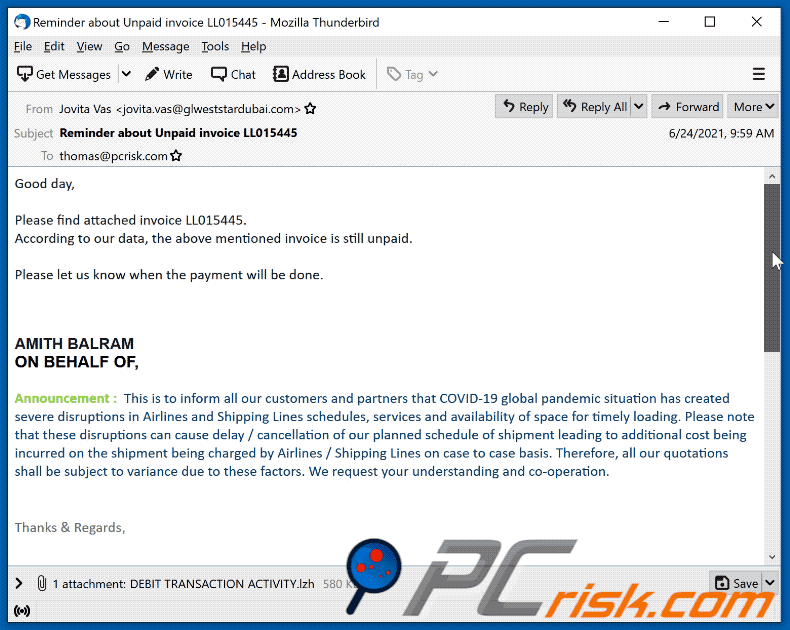
Text presented within:
Subject: Reminder about Unpaid invoice LL015445
Good day,
Please find attached invoice LL015445.
According to our data, the above mentioned invoice is still unpaid.
Please let us know when the payment will be done.
AMITH BALRAMON BEHALF OF,
Announcement : This is to inform all our customers and partners that COVID-19 global pandemic situation has created severe disruptions in Airlines and Shipping Lines schedules, services and availability of space for timely loading. Please note that these disruptions can cause delay / cancellation of our planned schedule of shipment leading to additional cost being incurred on the shipment being charged by Airlines / Shipping Lines on case to case basis. Therefore, all our quotations shall be subject to variance due to these factors. We request your understanding and co-operation.Thanks & Regards,
Jovita Vas
Inside Sales-Importsales
jovita.vas@glweststardubai.com
+971 4 3974400
+971 43974666
+971 4 6098530www.glweststardubai.com
11th Floor, Fahidi Heights, Khalid Bin Al Waleed Street, Bur Dubai, PO. BOx 6027, Dubai, United Arab Emirates
All our business activities and business transactions are undertaken in accordance with the NAFL Standard Trading Conditions. The duties, responsibilities and liabilities of the company are subject to the provisions of the NAFL Standard Trading Conditions. A copy of NAFL Standard Trading Conditions can be furnished upon request.
This message contains confidential and/or privileged information. If you are not the intended addressee or authorized to receive this for the intended addressee, you must not use, copy, disclose or take any action based on this message or any information herein. If you have received this message in error, please advise the sender immediately by reply e-mail and delete this message. Thank you for your cooperation.
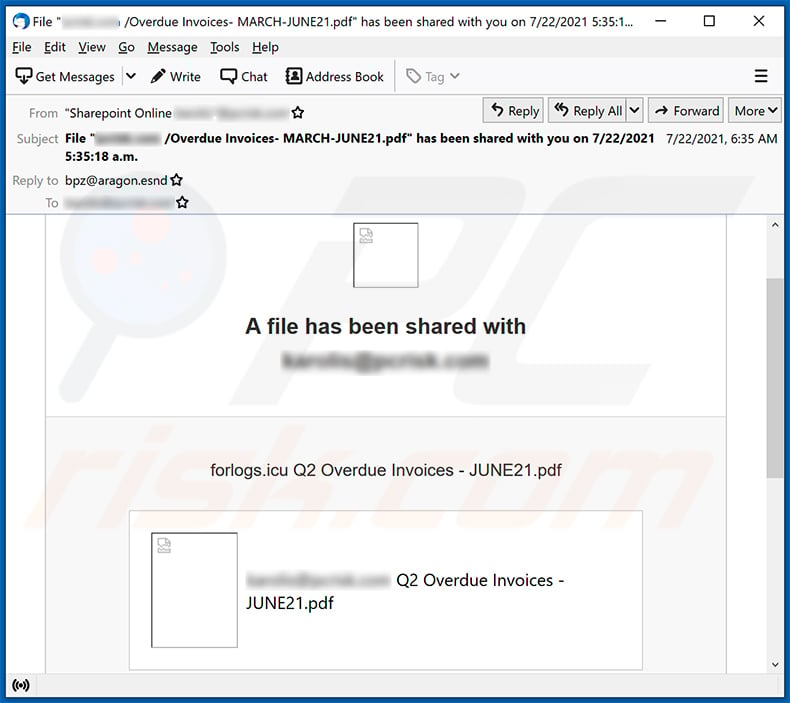
Yet another example of invoice-themed spam email promoting a phishing site:
Text presented within:
Subject: File "******** /Overdue Invoices- MARCH-JUNE21.pdf" has been shared with you on 7/22/2021 5:35:18 a.m.
A file has been shared with ********
forlogs.icu Q2 Overdue Invoices - JUNE21.pdf
******** Q2 Overdue Invoices - JUNE21.pdf
This link will work only for boss1
Open
Privacy Statement
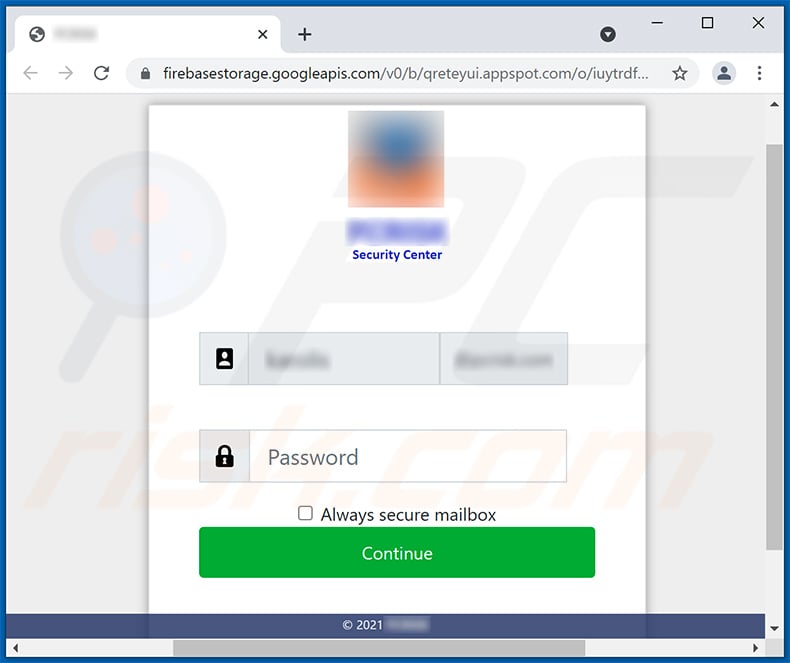
Screenshot of the promoted phishing site:
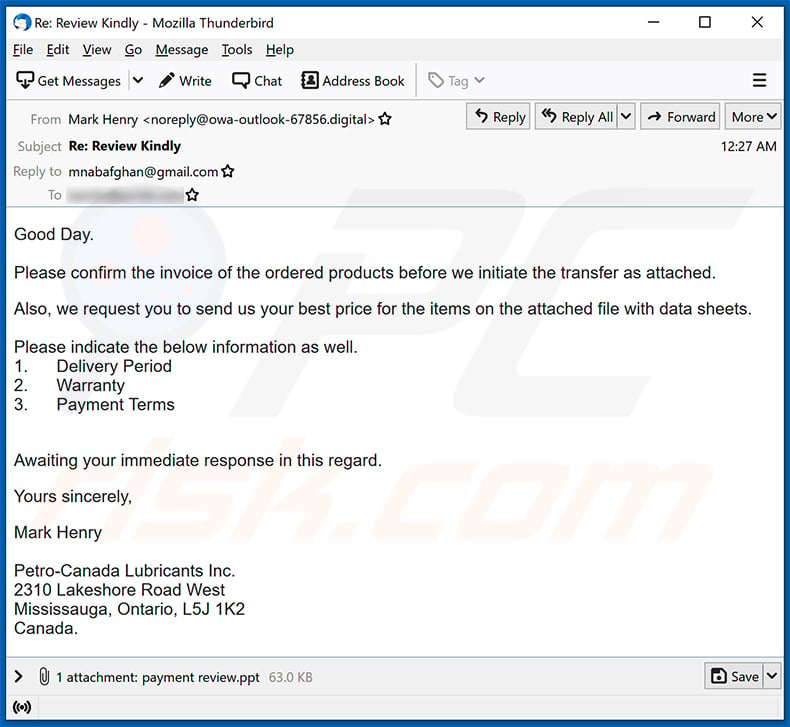
Yet another example of an invoice-themed spam email spreading a malicious MS PowerPoint document:
Text presented within:
Subject: Re: Review Kindly
Good Day.
Please confirm the invoice of the ordered products before we initiate the transfer as attached.Also, we request you to send us your best price for the items on the attached file with data sheets.
Please indicate the below information as well.
1. Delivery Period
2. Warranty
3. Payment TermsAwaiting your immediate response in this regard.
Yours sincerely,
Mark Henry
Petro-Canada Lubricants Inc.
2310 Lakeshore Road West
Mississauga, Ontario, L5J 1K2
Canada.
Yet another example of invoice-themed spam email spreading a malicious MS Excel document:
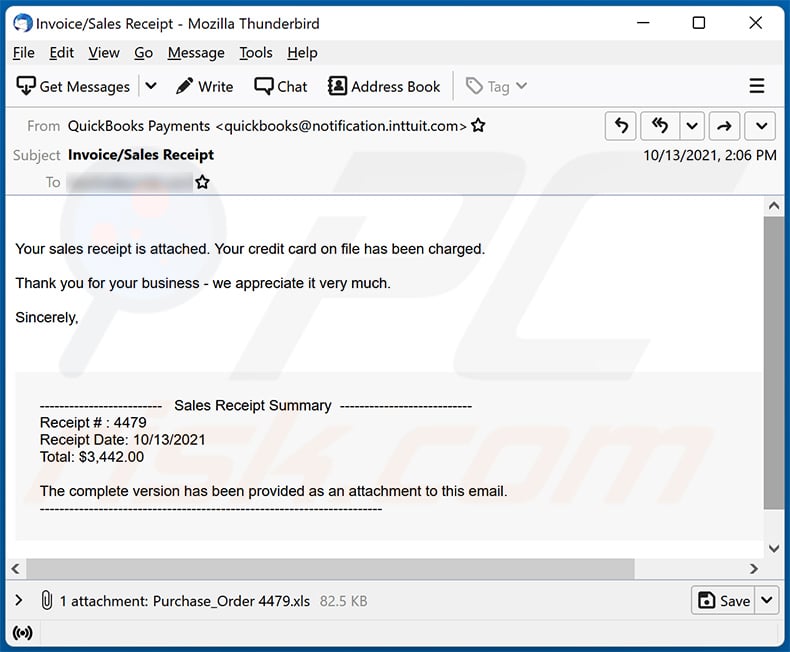
Text presented within:
Subject: Invoice/Sales Receipt
Your sales receipt is attached. Your credit card on file has been charged.Thank you for your business - we appreciate it very much.
Sincerely,
------------------------- Sales Receipt Summary ---------------------------
Receipt # : 4479
Receipt Date: 10/13/2021
Total: $3,442.00The complete version has been provided as an attachment to this email.
----------------------------------------------------------------------
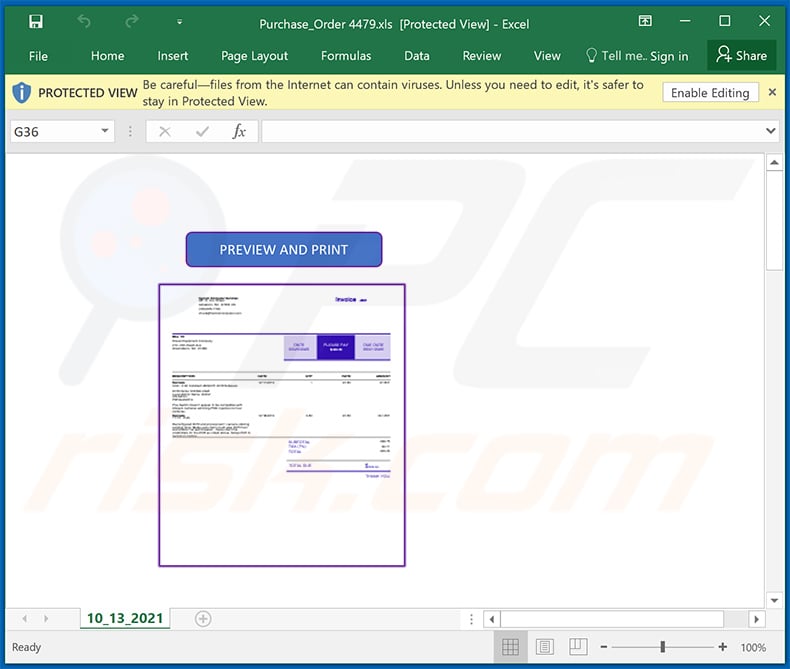
Screenshot of the distributed malicious MS Excel document:
Another example of invoice-themed spam email spreading FormBook malware:
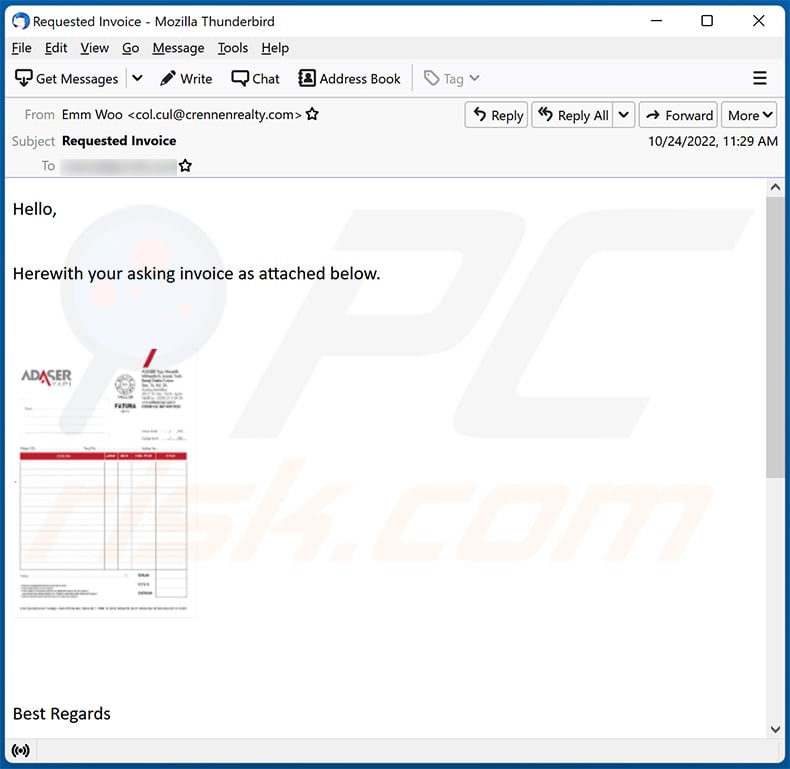
Text presented within:
Subject: Requested Invoice
Hello,
Herewith your asking invoice as attached below.
Best Regards
Emm Woo
Kang Chyau Industry Co., Ltd.
FEEL OUR PASSION
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Invoice spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
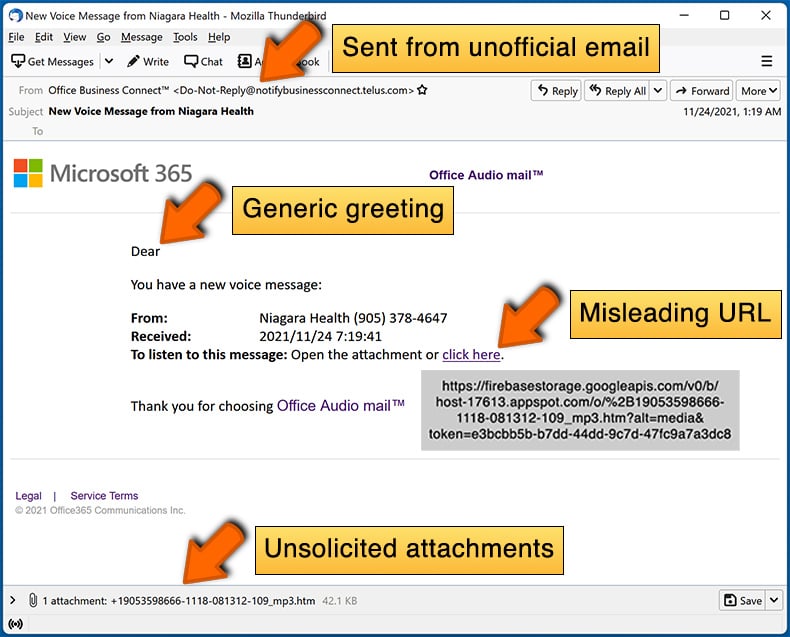
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Frequently Asked Questions (FAQ)
Why did I receive this email?
It is likely that cybercriminals have obtained your email address from some database of leaked emails. Emails used to deliver malware are not personal.
I have downloaded and opened a file attached to this email, is my computer infected?
The MS Office documents used in this malspam campaign do not infect computers unless they get permission to enable macros commands (editing or content). Although, malicious documents opened with MS Office versions released before 2010 infect computers without asking permission to enable macros commands.
I have read the email but didn't open the attachment, is my computer infected?
Opening a malicious email cannot cause any harm. Computers get infected only when recipients open/execute malicious files (attachments or files downloaded from received websites).
Will Combo Cleaner remove malware infections that were present in email attachment?
Yes, Combo Cleaner is capable of detecting and removing almost all known malicious programs. Certain malware can hide deep in the system. In such cases, the operating system must be scanned fully.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion