Malsmoke and ZLoader Targeting Adult Websites
Since the start of 2020 researchers have seen an almost continuous run of ZLoader campaigns. Initially distributed via exploit kits, malicious programs that look to exploit several known flaws, typically found in Internet Explorer. In the most recent campaigns discovered by researchers based at Malwarebytes, the attackers have changed tactics to use social engineering tactics to target those visiting popular adult content websites. Details of this change in tactics have been published by Malwarebytes on their blog.
Social engineering to distribute malware is not new but is still highly effective. These tricks are currently being used to distribute ZLoader, classified as a banking trojan, which is a piece of malware designed specifically to steal banking credentials or information attackers may use to commit fraud. ZLoader was inactive for two years till the end of 2019 when it saw a resurgence in activity. Now, the once banking trojan can be better described as an info stealer. Rather than targeting banking information exclusively, the malware now harvests a wide range of data, not just that related to banks and other financial institutions. The latest campaign, codenamed Malsmoke by researchers, looks to target adult sites that have incredibly high traffic turnovers. Sites like XHamster and Bravo Porn Tube rake in hundreds of millions to millions of visitors a month, respectively.
Researchers noted that previous campaigns relied on delivering SmokeLoader a piece of malware used to drop other malware strains onto an infected machine. SmokeLoader was primarily distributed by the Fallout kit which made a name for itself by being used to distribute the GandCrab ransomware. However, campaigns using this tactic seemed to end on October 18. Now, rather than an exploit kit, the attackers have deployed dummy web pages pretending to provide adult content and videos. By using a fake video, the attacker hopes to get a victim to click on it.
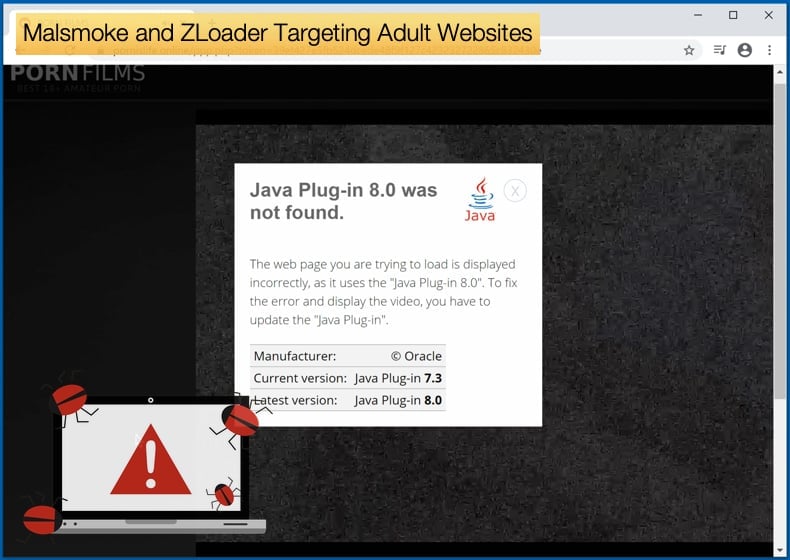
Once clicked the victim will be redirected to a new window which would play a few pixelated images, in the hope that a potential victim would still be interested. Then an alert will pop up warning the viewer that they would need to install a Java plugin to play the video. Clicking on the relevant button would then begin the installation process of the malware.
This trick was popular in a time when browsers needed several codecs, the software responsible for the compression and decompression of data, to play video content. Modern browsers have standardized what media formats can be used in the browser making many of the codecs of the past irrelevant. Flash was a popular application abused to distribute malware and adware. Those behind the Malsmoke campaign looked to take advantage of this by using the grainy images to make it appear a codec is missing. Researchers noted that the choice of a Java plugin is odd, stating,
“The threat actors could have designed this fake plugin update in any shape or form. The choice of Java is a bit odd, though, considering it is not typically associated with video streaming. However, those who click and download the so-called update may not be aware of that, and that’s really all that matters”
ZLoader Payload
Researchers could link the current campaigns to the threat actors behind the previous ones by discovering that the same fake webpage templates were used in both the old and new campaigns. Further, the cybercriminals used an email address to register a new domain for the new campaign that was already associated with other domains used in previous operations. When analyzing the fake Java plugin, researchers discovered that it contained legitimate libraries and executable files, a common tactic to try and avoid detection by security software. However, one of the components installed by the fake plugin would act as a downloader for ZLoader as the final payload of the campaign.
ZLoader, also called Terdot, was one of the many pieces of malware that emerged after the code for the Zeus banking trojan was leaked. The malware burst onto the scene, been sold on an underground hacker forum. Activity regarding the malware drastically increased up until early 2018 when the malware went silent. The malware only resurfaced in late 2019 been rapidly deployed in over a 100 campaigns with researchers detecting over 25 different versions been used in said campaigns. The current variant has been distributed differs greatly from the variant seen in the past but does more closely resemble the variants seen being used towards the end of 2019.
In the past, ZLoader was distributed via spam email campaigns, often with COVID-19 lures. Then for a period in 2020, exploit kits, namely, Fallout was used as the primary distribution method. Given that Fallout targets the now-defunct Internet Explorer, the potential for creating victims was much reduced. For this reason, the change in tactics to targeting visitors to adult websites might have been the rationale. As mentioned above, adult websites can see millions of visitors a month, even the less popular platforms can bring in millions of visitors a month. This drastically increases the number of potential victims the attackers could snare. Researchers further noted that,
“While we thought the threat actor had gone silent, they simply changed tactics to further grow their operations. Instead of targeting a small fraction of visitors to adult sites that were still running Internet Explorer, they’ve now extended their reach to all browsers…In the absence of high value software vulnerabilities and exploits, social engineering is an excellent option as it is cost effective and reliable. As far as web threats go, such schemes are here to stay for the foreseeable future.”
Malvertising and Adult Websites
In September 2020, Malwarebytes again discovered adult websites being targeted by threat actors this time for the purpose of malvertising. This time exploit kits were used to distribute Racoon Stealer. Again, the favored exploit kit was Fallout, meaning that Internet Explorer was again the favored attack vector. At the start of the campaign, the attackers looked to abuse the popular ad network ExoClick by redirecting to pages under the attacker’s control. These attempts were soon discovered and effectively shut down. This failure caused the attackers to use another domain and the RIG exploit kit to deliver Racoon Stealer. The attackers in this instance seemed to target smaller adult websites.
It was not until Malsmoke emerged that it was proved possible to target the most popular adult websites like XHamster. One of the main differences between the attackers was the use of more sophisticated redirection tactics on the part of Malsmoke. The latest campaign reported above be a further evolution in their tactics and improving on the redirection tactics developed previously. Further, those behind Malsmoke have been quick to improve already existing tactics or adopt new tactics like the Java plugin that drastically increases how many individuals can be fooled as it is not dependent on having a vulnerable browser like Internet Explorer.
While Internet Explorer is being replaced by other browsers, it is clear it still has a user base that hackers and malvertisers will continue to exploit. If you are still using Internet Explorer, it may be time to download another. Researchers noted,
“Threat actors still leveraging exploit kits to deliver malware is one thing, but end users browsing with Internet Explorer is another. Despite recommendations from Microsoft and security professionals, we can only witness that there are still a number of users (consumer and enterprise) worldwide that have yet to migrate to a modern and fully supported browser. As a result, exploit kit authors are squeezing the last bit of juice from vulnerabilities in Internet Explorer and Flash Player (due to retire for good next year).”
It is often users’ insistence on using software that is no longer supported by their developers that leave the gates wide open for attackers. Not only should software be updated but there is a real need for users to be aware of when software packages are no longer supported. Flash and Internet Explorer are just some of the software packages no longer receiving any kind of support.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion