Mac Shlayer Malware seen Exploiting Zero-Day
For those still clinging to the myth that Macs are inherently secure, 2021 is proving a difficult year to back up that argument. The advent of Silver Sparrow which raced to infect over 30,000 Macs and malware that targets Macs hiding in NPM packages are just two of several instances where Macs have been found to susceptible to attack. Now the threat operators behind the Shlayer malware have been seen exploiting a previously unknown zero-day. The good news is Apple has now released a patch for it, so it is strongly advised that Mac users download the latest patch if they have not done so already.
In summary, the malware’s creators found a way to bypass Apple's File Quarantine, Gatekeeper, and Notarization security checks and download second-stage malicious payloads. This is not the first time Shlayer has tricked Apple. Previously the malware was seen subverting the notarization process instituted with MacOS Catalina. This time, Shlayer subverts Gatekeeper to run malicious applications and harvest sensitive information.
The zero-day flaw tracked as CVE-2021-30657, takes advantage of a logic flaw in the way Gatekeeper checked if app bundles were notarized to run on fully patched macOS systems. In a blog post published by Objective-See and written by Patrick Wardle, the security researcher further notes,
“...this flaw can result in the misclassification of certain applications, and thus would cause the policy engine to skip essential security logic such as alerting the user and blocking the untrusted application.”
The malware is distributed via poisoned search engine results, the same method that has been seen in previous Shlayer campaigns.
The poisoning of search engine results comes from the threat actors creating web pages that contain content specifically tailored to perform well in search results with common queries. Another method of distribution seen by security researchers is the threat actor will hijack legitimate websites without the knowledge of the owner.
As most search engines rely heavily on automation for serving users results, often they inadvertently serve users with malware-laden search results. If a user clicks on one of the malicious results, they are redirected to a website that will prompt them to download the malware. The malware is masqueraded as a legitimate software package and the user is instructed that their current software package is out of date and they will be unable to access the content of the website.
New Gatekeeper Subversion
In an article published by Jamf detailing the latest Shlayer campaign and how it exploits the zero-day, researchers commented on how old campaigns would trick the system into believing they were legitimate. It was stated that,
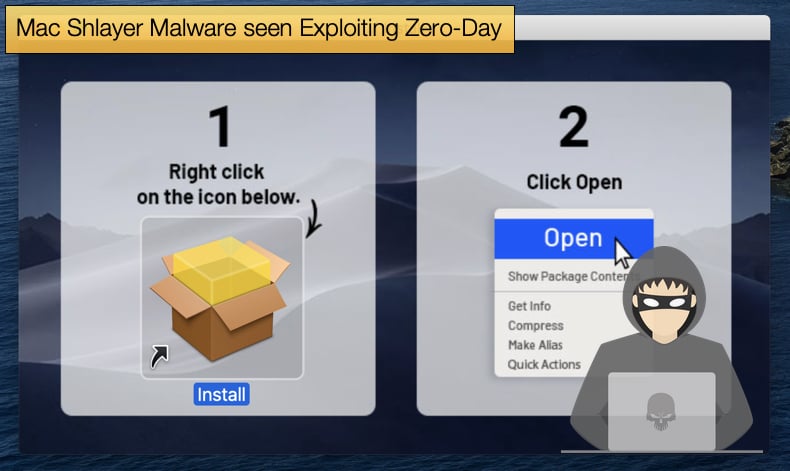
“An older variant of the Shlayer malware would deliver a dmg file that held a system link to a shell script. This shell script would have an installer logo attached to it, providing to the user the appearance of legitimacy. The mounted dmg also provided instructions to right-click the file and select “Open”, in an attempt to convince the user to install the malicious application. And while executing the file in this manner is allowed by Apple’s design, a consequence of this method allows applications - both trusted and malicious - to be opened while bypassing Gatekeeper’s checks altogether, leading in this instance to infecting the Mac.”
The new abuse of Gatekeeper is incredibly similar but differs in a few ways. First, the image displayed to convince the victim that the software package is legitimate has changed when compared to older campaigns. While trivial this fact can inform victims as to what they are dealing with. Researchers also noted that,
“The image displayed to the user after mounting the DMG appears to be the “Install” file…it is just a system link that points to the 1302.app application bundle, or the malicious application itself. By double-clicking the “Install” image in Figure C, the system actually executes the 1302.app, where 1302.app/Contents/MacOS/1302 is just a bash script…Due to the file path layout in which this script is set up, double-clicking the install icon executes the script held within 1302.app and bypasses the checks performed by Gatekeeper, described in further detail in CVE-2021-30657.”
The Shlayer malware once installed is capable of carrying out several malicious operations. The malware is capable of analyzing and modifying HTTPS traffic, allowing it to monitor the victims' browser traffic or inject ads and malicious scripts in visited sites. Most alarmingly, the malware can alter encrypted traffic, which is often used by online banking services and secure email providers when carrying out daily operations. Currently, Shlayer is used to drop adware, BundLore in particular, as a secondary payload but this can be changed in the future to drop far more damaging malware strains like ransomware and data wipers.
The Race to Patch
The end of 2020 and the beginning of 2021 so far has been a busy year for Apple patch releases. In November last year, the company patched three zero-day flaws that were found to affect iOS devices. The first was a remote code execution (RCE) bug tracked as CVE-2020-27930 and triggered by a memory corruption issue when processing a maliciously crafted font by the FontParser library.
The second iOS zero-day is a kernel memory leak tracked as CVE-2020-27950 and caused by a memory initialization issue that allows malicious applications to gain access to kernel memory. Lastly, CVE-2020-27932 is a kernel privilege escalation flaw caused by a type confusion issue that makes it possible for malicious applications to execute arbitrary code with kernel privileges. The flaws were found by Google’s Project Zero and patched promptly by Apple.
In January of this year, the company raced to fix bugs found in the iOS kernel, tracked as CVE-2021-1782, and two WebKit security flaws, tracked as CVE-2021-1870 and CVE-2021-1871. Security researchers have advised Mac and iOS users to patch fast and patch often, with researchers noting,
“This is once again a clarion call to keep your devices updated to the latest OS release. Even the most benign update may include fixes to a series of critical security flaws that an attacker could leverage against the device. Once an OS release is available, it is common for malicious attackers to analyze the updates to identify any patched vulnerabilities and then immediately create attacks against those. Attackers are well aware that not everyone updates their devices immediately; be that due to time, distractions, or the need for organizations to first ensure that the latest update works well with the rest of their software stack. This gives them a time window in which to leverage these now disclosed vulnerabilities until the updates are distributed.”
As early as 2017 and even before then, security researchers were busting the Mac security myth that led Mac users to believe that their computers were somehow invulnerable to malware and the intentions of hackers. Slowly this myth is becoming exactly that but what researchers are seeing is that Mac users are just as prone to not patch as their Windows counterparts.
No matter how quickly and effectively Apple can release patches it matters very little if they are downloaded and installed by the end-user. This certainly places responsibility on the head of the end-user, but it is not an unfair request to get the user to update and install patches regularly. Especially considering that this can be done automatically. The argument that patches can negatively impact system performance is true but finding your bank balance reduced due to a cyber attack is the greater headache.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion