Sodinokibi Smashes all the Records
Just as some were, rather hopefully, predicting that ransomware had peaked given the increased response by the US and other governments to both the Colonial Pipeline and JBS incidents. Ransomware operators behind Sodinokibi, who have also been blamed for the JBS incident, seem not to have received that memo and carried possibly the largest ransomware incident to date.
It is believed that an affiliate of the Sodinokibi ransomware gang carried out an attack that possibly impacted thousands of organizations according to the Associated Press. The affiliate is believed to have also been behind the recent JBS attack where 11 million USD was demanded as a ransom.
The most recent attack was believed to have been conducted by first compromising a firm that remotely manages the IT infrastructure for clients. Further, the attack has impacted organizations in at least 17 different countries.
According to the same Associated Press report Sodinokibi was demanding ransoms as high as 5 million USD to be paid in cryptocurrency. However, late on Sunday via the gang's Dark Web leak site it was announced that they would release a universal decryption key for 70 million USD.
As to whether the exact scale of the attack warrants such a high demand is still being determined by security researchers and response teams who have been working feverishly since Sunday, July 4 when the impact of the attack began to emerge.
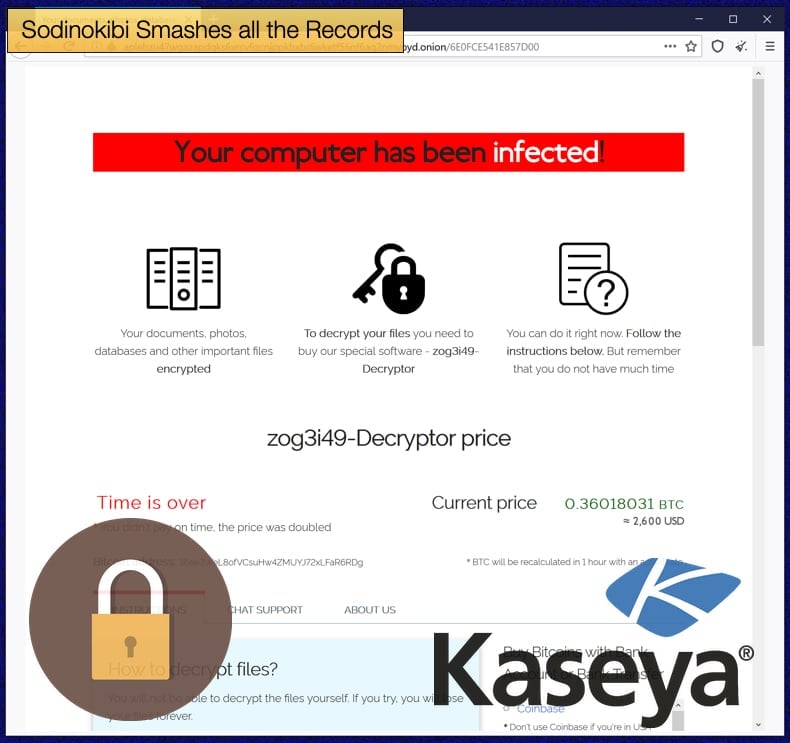
The attack impacted a wide array of businesses and organizations both in public and private spheres. Currently, a good picture of the scale of the attack has emerged from victims in Sweden and Germany. The Associated Press wrote,
“The Swedish grocery chain Coop said most of its 800 stores would be closed for a second day Sunday because their cash register software supplier was crippled. A Swedish pharmacy chain, gas station chain, the state railway, and public broadcaster SVT were also hit.
In Germany, an unnamed IT services company told authorities several thousand of its customers were compromised, the news agency DPA reported. Also among reported victims were two big Dutch IT services companies — VelzArt and Hoppenbrouwer Techniek. Most ransomware victims don’t publicly report attacks or disclose if they’ve paid ransoms.”
The IT managed service provider that was compromised was Kaseya, based in Miami, Florida, with the CEO of the company Fred Voccola estimating the number of impacted customers to be in the low thousands. The IT provider further noted that they believed that the attack only impacted 50 to 60 of the company’s direct customers.
The reason why thousands of potential victims exist is that other managed service providers use Kaseya's VSA software tool.
The software tool automates the installation of software and security updates and manages backups and other vital tasks. In response to the attack, Kaseya has released a software detection tool to help impacted parties mitigate the threat.
The timing of the attack is important to consider. As with the JBS incident, the Kaseya attack occurred over a holiday weekend in the US. The attacker did this because over such periods companies will be staffed by the bare minimum needed as other employees enjoy the holiday, the Fourth of July, or American Independence Day for the Kaseya attack, and Memorial Day for the JBS attack.
Given that many offices in the US were closed on Monday, July 5, more reports from victims, especially in the US, may only begin to emerge following their reopening. In response to the attack, US President Biden stated that the U.S. would respond if it was determined that the Kremlin is at all involved.
In a statement issued by the White House, President Biden said shortly after being made aware of the attack to a reporter,
“And the fact is that I directed the intelligence community to give me a — a deep dive on what’s happened, and I’ll know better tomorrow. And if it is, either with the knowledge of and/or a consequence of Russia, then I told Putin we will respond.”
Attack Details
Just as the exact scale of the attack is yet to be determined, details of how the attack was carried out are also not one hundred percent certain. However, according to Bleeping Computer and the Dutch Institute for Vulnerability Disclosure (DIVD), initial access to Kaseya’s software was granted via a zero-day exploit.
In a blog post written by Victor Gevers for the DIVD, it was written that the vulnerability that was discovered by Dutch researchers and Kaseya was validating the patch before they rolled it out to customers. Further, it was stated,
“After this crisis, there will be the question of who is to blame. From our side, we would like to mention Kaseya has been very cooperative. Once Kaseya was aware of our reported vulnerabilities, we have been in constant contact and cooperation with them. When items in our report were unclear, they asked the right questions…Also, partial patches were shared with us to validate their effectiveness. During the entire process, Kaseya has shown that they were willing to put in the maximum effort and initiative into this case both to get this issue fixed and their customers patched…They showed a genuine commitment to do the right thing. Unfortunately, we were beaten by REvil [Sodinokibi] in the final sprint, as they could exploit the vulnerabilities before customers could even patch.”
As to the exact nature of the zero-day, the infosec community will have to wait until the proof-of-concept code is released and more information has been released to the public in general. The vulnerability has been assigned the identifier CVE-2021-30116 but at the time of writing little else has been disclosed.
Other than DIVD, security firm Mandiant has been tasked by Kaseya with discovering exactly how the attack unfolded. In the meantime customers using Kaseya’s VSA servers have been asked to shut them down and leave them offline until comprehensive remediation steps have been conducted.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion