Sodinokibi Websites and Infrastructure are Mysteriously Offline
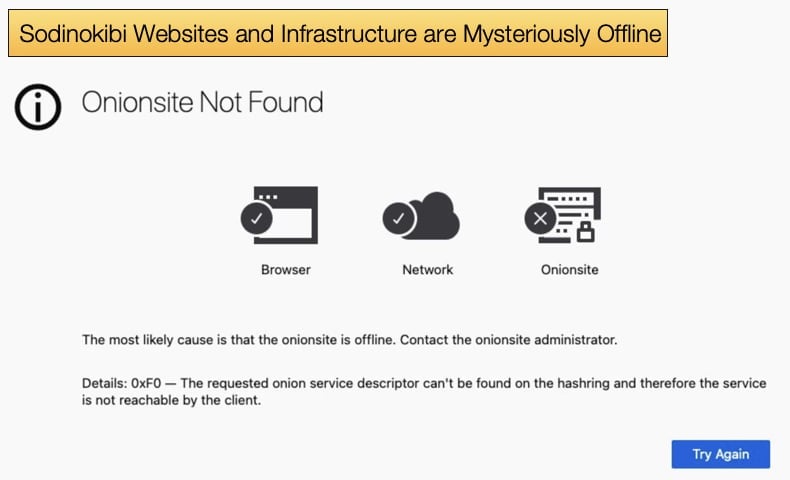
On the evening of Monday, July 13, 2021, various news outlets began reporting that websites and infrastructure were used by ransomware operators behind the Sodinokibi strain had been taken offline. This resulted in several theories being proposed as to why. Was it a result of legal action? Was it increased pressure by governments following both the JBS and Kaseya incidents?
The latter has been estimated to have resulted in an estimated 1,500 small to medium enterprises becoming victims. Or has the gang decided to call it quits, restructure its infrastructure, or has the gang split based on internal differences and squabbles?
The answer to any of those questions is purely speculation at this point. There are some clues as to why websites were taken offline but it is prudent to review the facts so far. According to ZDNet’s coverage of events, security researchers began noticing that the payment site, the group's public site, the “helpdesk” chat, and their negotiation portal had all been taken offline. Bleeping Computer reported the same.
Both publications asked several cybersecurity experts and researchers as to their opinions. Allan Liska, a ransomware expert, and CSIRT at Recorded Future speaking to ZDNet noted,
“We all want to believe it is law enforcement, but this is a pretty extensive takedown across multiple providers…This early on the more likely scenario is that it is a self-directed takedown. But I wouldn't rule out 'self-directed after a conversation with the Kremlin.' We've been speculating about this since the Kaseya attack: Biden gets a win because a major ransomware gang is gone, Putin gets a win because he 'helped' and REvil gets to keep all of their money (and their heads). The timing, the day before the next ransomware summit tomorrow, also lines up. But, that is all speculation.”
Allan Liska’s opinion is supported by current events surrounding both US president Joe Biden and Russia’s President Vladimir Putin, which have been neatly summarised by President Biden in an interview. President Biden said,
“I made it very clear to him that the United States expects when a ransomware operation is coming from his soil, even though it's not sponsored by the state, we expect them to act if we give them enough information to act on who that is…And secondly, we've set up a means of communication now on a regular basis to be able to communicate with one another when each of us thinks something is happening in another country that affects the home country. And so it went well. I'm optimistic.”
Jake Williams, CTO at BreachQuest, believes that ransomware gangs operating with near impunity from Russia, as long as it did not impact Russian interests, were on borrowed time. Williams noted,
“That has clearly changed – the Russian government can clearly see they are being impacted by the actions of these actors. Whether REvil was taken out of commission by the Russian government, saw the writing on the wall and took infrastructure down, is simply rebranding like so many groups have (likely including REvil itself), or something else is unknown at this point,”
Lessons from the Past
There are several questions demanding answers, with the likelihood of only some being answered. However, this is not the first time ransomware operators have made their infrastructure disappear. In very recent history the operators of the DarkSide ransomware seemed to have done a very similar thing following the Colonial Pipeline they were responsible for. The result of the attack harmed petroleum supplies across the eastern seafront of the US due to the pipelines operators being forced to shut down operations.
Reports of fuel shortages soon followed prompting a response from the White House, including new measures designed to combat ransomware operations by allowing for greater information sharing between public and private enterprises including law enforcement.
Law enforcement agencies in the US also received a mandate to treat ransomware attacks in a similar vein to terrorist attacks, this gave officials greater search and seizure powers which helped in the retrieval of a large portion of the ransom that was paid by Colonial Pipeline to return to operational capacity.
Likewise, those behind the Babuk Locker ransomware announced their exit from the ransomware circuit. This was done so that the operators could focus more on the data-stealing for the extortion side of the business. This was short-lived as not long after the announcement it appeared the gang had returned to the ransomware scene, even boasting a new leak site used to announce who they had compromised and turned into victims.
The early and brief retirement may have been caused by the malware’s source code being leaked to the public. Their return to the ransomware scene was heralded by a new version of the ransomware.
Even Sodinokibi’s birth was a result of another ransomware gang calling it quits. In 2019 GandCrab was the ransomware strain stealing all the headlines while it extorted potentially millions. The ransomware became the bane of many security researchers as new versions of the ransomware would be released constantly to stay a few steps ahead of attempts to stop operations.
Then in the middle of 2019, the gang announced it was retiring. It seems that not all the gang were on board with the split and went on to develop Sodinokibi.
Sea Change
Even before ransomware began the scourge of the cyber threat landscape it has now become, security researchers were pleading with governments and law enforcement to do something more in the fight against cybercrime. This is not to say that nothing was done by public and private enterprises.
Partnerships like No More Ransom were formed to help victims decrypt files so that there was no need to pay the ransom. It was clear that this was not enough, as almost daily the public could read about a new victim severely impacted by a ransomware strain compromising and encrypting data.
There are several reasons why this was happening, but one reason was the geopolitics at play between Russia and the West. As alluded to above as long as hackers operating from or using Russia as a base of operations targeted nothing seen as Russian interests or Russian civilians, both the government and law enforcement would do little to stop such activity.
Some have even argued that constant malware attacks on the West were in the current Russian government’s interests as they helped show apparent weaknesses in the West propped up by propaganda within the country.
The current change in US policy driven by President Biden’s administration seems to have prompted a change in the status quo. It is still early when judging the effectiveness of the policy change, but it appears that allowing hackers to operate with impunity is no longer in Russia’s best interests.
By equating cyber-attacks, namely a ransomware attack, to terrorism especially in cases where critical infrastructure is impacted it does Russia very little good to appear to be harboring criminals equated with terrorism.
Reports have emerged in the past showing Russian hackers living lavish lifestyles resulting from their ill-gotten gains. Sports cars driving irresponsibly with a hacker at the wheel in a busy Russian city or social media posts flexing the latest in luxury goods may soon become something of an oddity. The public might finally be witnessing the sea change in attitude security experts have asked for.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion