WordPress Sites Seen Spreading Malware via Fake DDoS Pages
Distributed denial of service (DDoS) attacks is a common frustration for internet users when looking to access their favorite online resources. Upon visiting such a resource the visitor may see a page stating that the page they want to visit is currently unavailable due to DDoS attempts flooding the web server with garbage traffic. For example, such a page is generated by DDoS protection services like Cloudflare. Now, hackers have weaponized these pages to spread malware.
Normally, such a page will ask the user to perform a check or skill test to ascertain if the user is a bot or not.
However, according to a recent blog post by security firm Sucuri, a recent surge in JavaScript injections targeting WordPress sites has resulted in fake DDoS prevent prompts which lead victims to download remote access trojan malware.
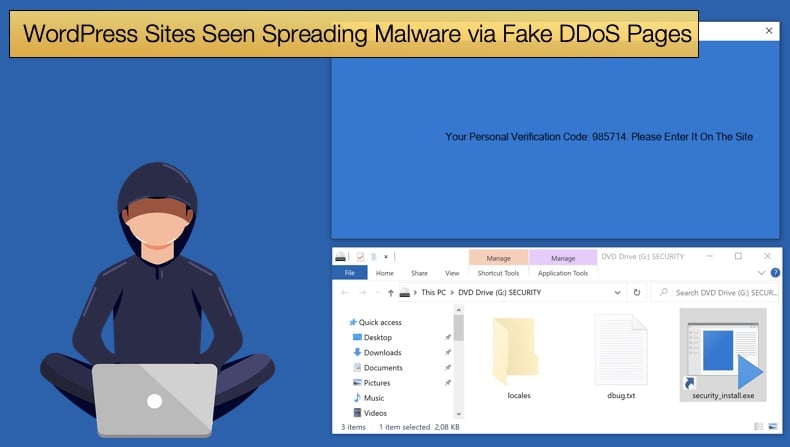
These JavaScript injections generate a fake Cloudflare DDoS protection popup. It is hoped, by the attacker, that the user will not think twice about interacting with the page as such protection is now commonplace.
The prompt, rather than proving the user is human, downloads a .iso file. This file type also referred to as a .iso image, was developed to make an exact copy of a DVD or Blue Ray disk and is often used as a handy method to distribute operating systems.
Being able to store large amounts of data, hackers soon twigged that a .iso file can make for a great malware delivery tool.
Once the .iso file is downloaded, the webpage will then prompt the visitor to open the downloaded file to get a verification code to access the webpage.
This is all a charade as opening the downloaded file begins the attack chain in earnest. It is this file that contains the malware payloads, which include RacoonStealer and NetSupport RAT.
Before looking at the malware in terms of defending against this threat, Sucuri advises that website owners take the following mitigation steps:
- Keep all software on your website up to date
- Use strong passwords
- Use 2FA on your administrative panel
- Place your website behind a firewall service
- Employ file integrity monitoring
As for those visiting websites, the following mitigation strategies are suggested:
- Make sure your computer is running a robust antivirus program
- Place 2FA on all important logins (such as your bank, social media)
- Practice good browsing habits; don’t open strange files!
- Keep your browser and all software on your computer updated/patched
- Use a script blocker in your browser if you are willing to loose functionality when viewing websites
The Malware Payloads
For a period Racoon Stealer activity seemed to drop off the map but in June 2022 version 2 of the malware made waves. In summary the malware is capable of stealing of data such as passwords, cookies, and autofill data from browsers.
Raccoon stealers also supports the ability to steal from all cryptocurrency wallets. ZScaler summarised the new version as follows,
“Raccoon v2 is an information stealing malware that was first seen on 2022-07-03. The malware is written in C and assembly.
Though we noticed a few new features in the newer variant as mentioned below, the data stealing mechanism is still the same as is seen in its predecessor:
- Base64 + RC4 encryption scheme for all string literals
- Dynamic Loading Of WinAPI Functions
- Discarded the dependence on Telegram API
We have noticed a significant change in the way list of command and control servers is obtained. The Raccoon Malware v1 was seen abusing the Telegram network to fetch the list of command and control servers, whereas the newer variant has abandoned the use of Telegram. Instead, they use a hardcoded IP address of a threat-actor-controlled server to fetch the list of command and control servers from where the next stage payload (mostly DLLs) is downloaded.”
With regards to NetSupport RAT, the program is a legitimate software tool which can be used by IT admin and support staff to grant access to other machines remotely.
Such a tool is a godsend when looking to troubleshoot IT issues across vast distances without the need for professional to be in front of the troublesome machine.
That being said, hackers have turned the legitimate tool into a piece of malware which allows the attacker remote access to the victims machine.
In the past, malicious versions of NetSupport were seen being distributed via bogus NortonLifeLock documents via a malicious Word document.
It is clear that the attackers in this latest campaign have crafted a dangerous delivery method for the malware strains covered above. Attacks on legitimate websites to spread malware pose reputational damage to the website owners and real damage to visitors to those websites.
If you administer or own a Wordpress website implementing the mitigation strategies listed by Sucuri is highly advised.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion