Porsche South Africa Hit by Possible Ransomware Attack
On February 21, 2023, South African publication MyBroadband published an article noting that Porshe South Africa’s headquarters in Johannesburg had possibly suffered a ransomware attack.
The publication stated,
“MyBroadband understands the attackers used a relatively new ransomware strain called Faust to encrypt the company’s files and lock it out of corporate systems…Security researchers have reported that Faust is derived from the Phobos ransomware family…This malware family is typically deployed via hacked Remote Desktop Protocol connections.”
At the time of writing Porsche South Africa was yet to publish a comment and responded to MyBroadband’s inquiries with the standard “no comment.”
However, car dealerships are favored targets for certain ransomware operators as they store customers' personally identifiable information, especially regarding deals structured around monthly repayments.
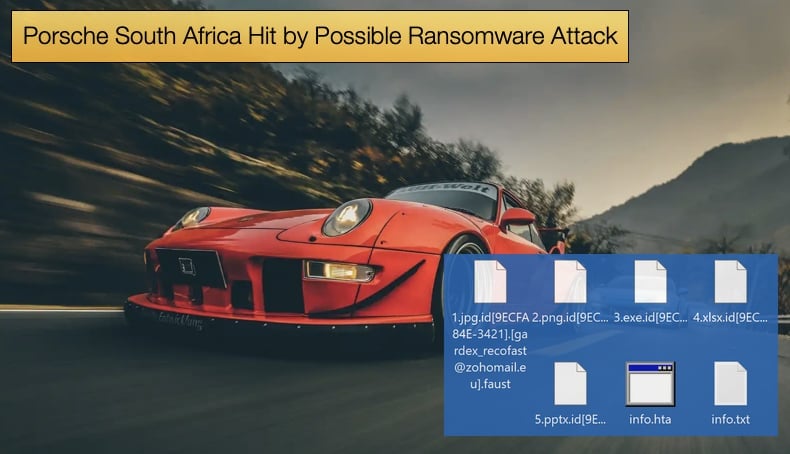
This publication discovered the Faust ransomware variant in November 2022. We discovered that Faust belongs to the Phobos family. Upon encryption, filenames are appended with a unique ID, the cyber criminals' email address, and a ".faust" extension. For example, a file titled "1.jpg" appeared as
"1.jpg.id[9ECFA84E-3421].[gardex_recofast@zohomail.eu].faust" following encryption. A ransom note is then created and then displayed in a pop-up window. The malware also creates a text file containing the ransom note with the filename info.txt.
Faust is distributed via several methods including infected email attachments (macros), torrent websites, and malicious ads. In our published report detailing information about Faust, we noted,
“The message in the pop-up provides more information. It clarifies that recovering the data will require paying a ransom in Bitcoin cryptocurrency. The payment size will supposedly depend on how quickly victims contact the cyber criminals…Additionally, before paying - victims can test decryption on five files (within certain specifications) free of charge. The note alerts that renaming the encrypted files and/or using third-party recovery tools may result in permanent data loss. Victims are also warned that third-party involvement can result in increased financial loss…Based on our considerable experience researching ransomware infections, we can conclude that decryption is usually impossible without the attackers' interference.”
Threat actors deploying both Phobos and its variants such as Faust are known for using the “double extortion” tactic. This is when sensitive data is stolen by threat actors before the encryption routine begins.
This data is then used to place more pressure on victims to pay as threat actors will threaten to release the data if the ransom is not received by a specific deadline.
This gives the tactic its name as victims are not only extorted to access encrypted data but also threatened sensitive data will be released to the public. Seeing that car dealerships have stored substantial amounts of sensitive data about customers there is the temptation for business leaders to submit to threat actor demands.
Increased Ransomware Activity in South Africa
Following increased pressure from the US and other Western Governments to crack down on ransomware operations by seizing assets and critical infrastructure like servers, ransomware operators have looked to diversify operations away from these targets.
In the past large English-speaking regions like North America, Australia, and parts of Europe were targeted for their large economies and the large companies that make up that economies. Ransomware operators figured they could easily target Fortune 500 companies and the like with little in the way of repercussions.
Now, the crackdown has even caused companies to question whether they should pay or not as some governments including the US might perceive such payment as funding terrorist organizations or organizations sanctioned by those governments.
This would possibly make paying the ransom a crime. Ransomware operators have turned to countries south of the equator to target developing economies, including South Africa.
Charl van der Walt, Head of Security Research at Orange Cyberdefense said that attacks in Africa increased 50% in 2022, with many researchers attributing the rise to increased pressure placed on operators by western governments.
In a separate report by James Gumede, SADC territory account manager at Kaspersky, Gumede stated that from January to April 2022, ransomware attacks in South Africa have doubled over the comparative period of 2021.
There is a clear upward trend in ransomware attacks for Africa’s most developed economy. The question to answer then is why is South Africa seen as a viable target. Part of the reason will be that ransomware operators believe there are more opportunities when compared to the rest of Africa because of the southern nation’s economy.
The country also has several major problems to deal with including not being able to meet the country’s electricity demands resulting in near-constant rolling blackouts. Policing cybercrime is then low on the leadership of the country’s agenda.
With both a perceived and real lack of cybercrime policing ransomware operators feel they can operate with little risk. Further, victims might feel that it is easier to pay the ransom due to the lack of a coordinated government effort to assist victims. These factors combined create a dangerous reality for South African government institutions, law enforcement, and enterprises.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion