New Malware Granting Threat Actors Hidden VNC Access
According to a new report published by Elastic Security Labs, their security researchers discovered a new malware strain dubbed LOBSHOT.
The discovery was made when researchers notices a spike a malvertising campaigns at the start of 2023, where threat actors distributed malware strains using an elaborate scheme of fake websites through Google Ads.
Users download what they believe to be legitimate installers for legitimate software applications. Once the installer is initiated the now compromised system is backdoored and malware is installed without the victim’s knowledge.
Elastic Security Labs has determined that the infrastructure used in distributing LOBSHOT belongs to TA505, also known as Graceful Spider.
The infrastructure has been used to distribute the Clop ransomware in the past. It should be noted that the domain used by TA505 may have changed hands in the past and it is unclear if TA505 still controls it or not. Researchers noted that,
Throughout our analysis, we observed infrastructure known to belong to TA505. TA505 is a well-known cybercrime group associated with Dridex, Locky, and Necurs campaigns. A loader documented by Proofpoint, known as Get2, has also been tied to the same domains in the past that we observed with LOBSHOT. We assess with moderate confidence that LOBSHOT is a new malware capability leveraged by TA505 starting in 2022.
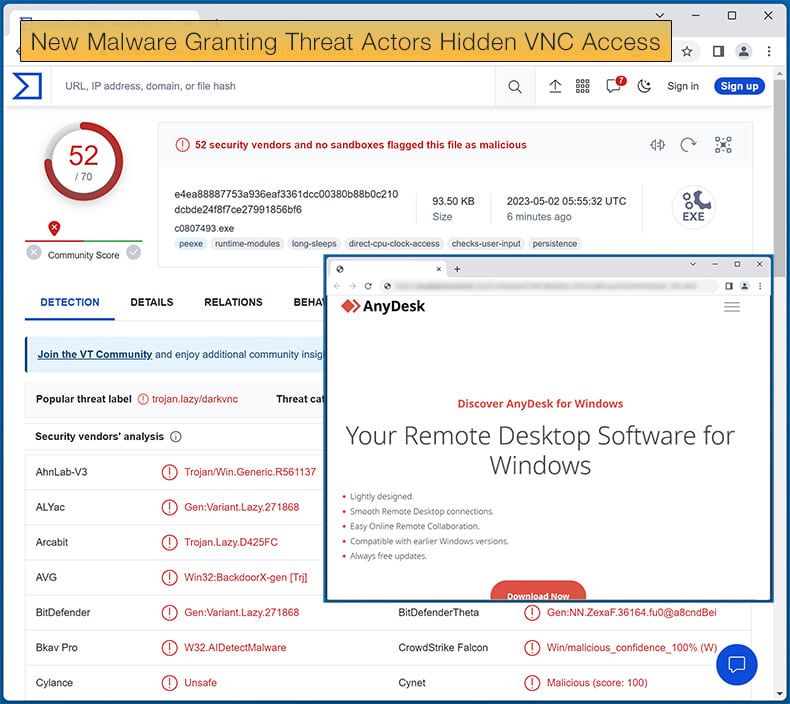
In the campaign pushing LOBSHOT, threat actors were leveraging the popularity of AnyDesk, a popular remote desktop application, by redirecting users to a domain controlled by the threat actors.
This is done by placing a Google Ad near the top of search results for Anydesk. When clicked the user is redirected to amydecke[.]website instead of the legitimate AnyDesk URL, anydesk.com.
Perhaps LOBSHOT's most notable capability is how it can remain hidden on the compromised system, while still being capable of stealing sensitive information from the victim. LOBSHOT does this by using a Hidden Virtual Network Computing (hVNC).
IBM defines an hVNC as follows,
Unlike traditional VNC (Virtual Network Computing) where the software provides remote access to a machine with the user’s consent and the visibility of the actions taken on the machine can be clearly observed. hVNC acts in the opposite way designed to stay stealthy where all actions by an attacker are taking place on the same machine, but can’t be visibly observed by the victim. hVNC became a popular solution within the banking trojan space to bypass device and fraud detection solutions.
LOBSHOT deploys an hVNC by first generating a hidden desktop using the CreateDesktopW Windows API and then assigning the desktop to the malware using the SetThreadDesktop API. A new Windows explorer.exe process is then created under the context of the new hidden desktop.
By this stage of the attack the compromised machine will begin sending screen captures to the hVNC which in turn is sent to a listening client in preparation for exfiltration.
Further, the threat actor can interact with the compromised machine in various ways including controlling the keyboard, clicking buttons, and moving the mouse, these capabilities effectively provide the threat actor full remote control of the device.
LOBSHOT includes several other useful features like switching the command-and-control server information on the fly, helping guarantee successful data exfiltration.
LOBSHOT also comes with a full graphic user interface (GUI) to make the threat actor's job a lot easier. The GUI allows the threat actor to run the following commands with relative ease:
- Start new explorer.exe process
- Start Windows Run command
- Start new Windows process with provided command
- Start Browsers (Internet Explorer, Edge, Firefox)
- Terminate existing explorer.exe processes and start new explorer.exe process
- Tamper with Windows sound settings
- Set/retrieve Clipboard text
- Activate Start Menu
- Modify DPI Awareness settings
Currently, LOBSHOT is being leveraged to steal banking and financial information, in a way reminiscent of banking trojans. Elastic Security Labs concluded,
Threat groups are continuing to leverage malvertising techniques to masquerade legitimate software with backdoors like LOBSHOT. These kinds of malware seem small, but end up packing significant functionality which helps threat actors move quickly during the initial access stages with fully interactive remote control capabilities. We are continuing to see new samples related to this family each week, and expect it to be around for some time.
Be Careful of Promoted Ads
The use of Google Ads to spread malware is by no means a new problem, however, security researchers have noticed a ramp-up in threat actors using this distribution technique to infect unsuspecting victims.
Some researchers believe that the increase in this technique may be down to a threat actor selling malvertising-as-a-service, but this remains to be proved without a doubt.
Various calls have gone out to Alphabet, Google’s holding company, to apply stricter regulations as to what ads are approved or not. That being said it is advised that end users always check the domain they are on versus the legitimate domain distributing legitimate software.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion