Free Akira Ransomware Decryptor Released To The Public
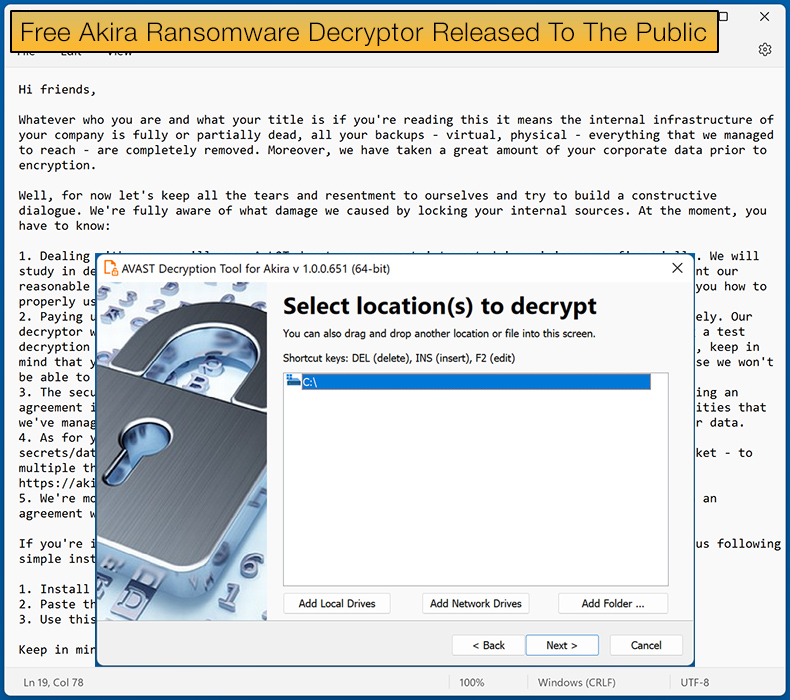
Security firm Avast has released a free decryptor for those impacted by the Akira ransomware. The decryptor can help victims recover their data without paying the ransom, and Avast has released decryptors for both 64-bit and 32-bit Windows operating systems.
Akira is relatively new to the ransomware scene, launched in March 2023. The ransomware quickly began stealing headlines following several high-profile victims being announced shortly after being launched.
In 2017, a ransomware strain, also known as Akira, began circulating, but there is currently no evidence to suggest the two are linked.
Soon after launch, a sample was discovered by MalwareHunterTeam and shared with Bleeping Computer for analysis.
The subsequent article published by Bleeping Computer noted Akira would delete Windows Shadow Volume Copies on the device by running a PowerShell command and that the ransomware module will look to encrypt the following extensions,
.accdb, .accde, .accdc, .accdt, .accdr, .adb, .accft, .adf, .ade, .arc, .adp, .alf, .ora, .btr, .ask, .cat, .bdf, .ckp, .cdb, .cpd, .cma, .dad, .dacpac, .daschema, .dadiagrams, .db-shm, .db-wal, .dbf, .dbc, .dbt, .dbs, .dbx, .dbv, .dct, .dcb, .ddl, .dcx, .dlis, .dsk, .dqy, .dtsx, .dsn, .eco, .dxl, .edb, .ecx, .exb, .epim, .fdb, .fcd, .fmp, .fic, .fmpsl, .fmp12, .fol, .fpt, .gdb, .frm, .gwi, .grdb, .his, .hdb, .idb, .itdb, .ihx, .jet, .itw, .kdb, .jtx, .kexic, .kexi, .lgc, .kexis, .maf, .lwx, .mar, .maq, .mav, .mas, .mdf, .mdb, .mrg, .mpd, .mwb, .mud, .ndf, .myd, .nrmlib, .nnt, .nsf, .nyf, .nwdb, .oqy, .odb, .owc, .orx, .pdb, .pan, .pnz, .pdm, .qvd, .qry, .rctd, .rbf, .rodx, .rod, .rsd, .rpd, .sbf, .sas7bdat, .sdb, .scx, .sdf, .sdc, .spq, .sis, .sqlite, .sql, .sqlitedb, .sqlite3, .temx, .tps, .tmd, .trm, .trc, .udl, .udb, .usr, .vpd, .vis, .wdb, .vvv, .wrk, .wmdb, .xld, .xdb, .abcddb, .xmlff, .abx, .abs, .adn, .accdw, .icg, .hjt, .kdb, .icr, .maw, .lut, .mdt, .mdn, .vhd, .vdi, .pvm, .vmdk, .vmsn, .vmem, .nvram, .vmsd, .raw, .vmx, .subvol, .qcow2, .vsv, .bin, .vmrs, .avhd, .avdx, .vhdx, .iso, .vmcx
Just a quick glance at the targeted extensions shows that the ransomware's developers are going after every useful thing that could be found on a storage device in an attempt to cripple the victim's ability to conduct business.
Bleeping Computer discovered that the ransomware would skip files located in the Recycle Bin, System Volume Information, Boot, ProgramData, and Windows folders, and Windows system files with .exe, .lnk, .dll, .msi, and .sys file extensions would be avoided entirely. Files encrypted have ".akira" appended to them.
As with other ransomware strains, its developers follow the double-extortion method of encrypting data and stealing data to leverage in negotiations or sell to the highest bidder.
To do this, Akira uses the tried and tested technique of breaching a corporate network and spreading laterally to other devices. The ransomware is deployed throughout the network once the threat actors gain Windows domain admin credentials.
Akira's Achilles Heel
Avast's analysis confirmed that the ransomware uses a symmetric key generated by CryptGenRandom, which is then encrypted by a bundled RSA-4096 public key and appended to the end of an encrypted file.
The encryption method would typically mean that the threat actor alone possesses the private RSA decryption key, preventing anybody from decrypting the data unless the ransom is paid.
For security firms to develop a free decryptor, the encryption routine must be cracked. Avast did not mention how this was done, as if mentioned in their report, it would make it a lot easier for the malware's developer to shore up the flaw and make it far more complicated in the future for security researchers moving forward.
In Bleeping Computer's article about the release of the decryptor, it was noted,
Avast does not explain how it cracked Akira's encryption, but the security firm may have exploited the ransomware's partial file encryption approach…Akira on Windows encrypts files only partially for a speedier process, following a different encryption system depending on the file size…For files smaller than 2,000,000 bytes, Akira will only encrypt the first half of the file contents…For files larger than 2,000,000 bytes, the malware will encrypt four blocks based on a pre-calculated block size determined by the file's total size.
As mentioned above, Avast released a decryptor for both 64-bit and 32-bit Windows architectures, with the security firm recommending that victims use the 64-bit when possible, as cracking the password requires a lot of system memory.
Avast confirmed that they are working on a decrypter for Linux machines, as last week, it was reported that Akira samples were capable of targeting VMware ESXi servers.
Avast, commenting on the Linux version, noted that the Linux version of the Akira ransomware works identically to its Windows counterpart. Encrypted files have the same extension and the same encryption schema.
As Windows CryptoAPI, used in Windows versions of the ransomware, are not available on Linux, the ransomware authors used the Crypto++ library to cover the parts handled by CryptoAPI in Windows.
For those using Avasts decryptor, it is crucial to follow their instructions to the letter when decrypting your data. As an example of why this is important when decrypting, it was stated, "Due to Akira's block size calculation, there may be a dramatic difference in the size limit even for files that differ by a size of 1 byte."
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion