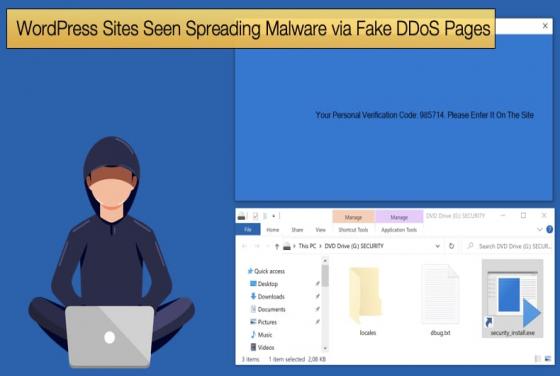
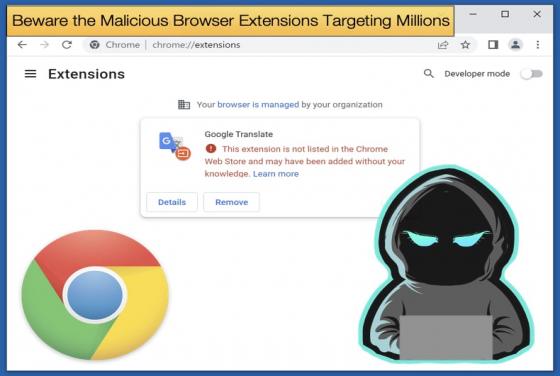
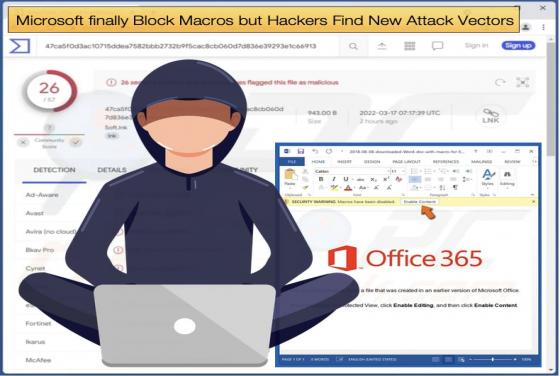
Beware of Bumblebee’s New Features
Initially discovered in April 2022, Bumblebee activity rose as BazarLoader activity dropped off. This hinted at the Conti ransomware gang, and TrickBot had switched malware to grant backdoor access for the ransomware on targeted networks. Since Bumble Bee’s discovery, the developers behind the malwa