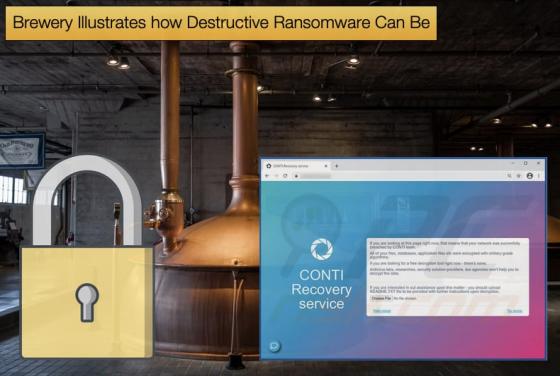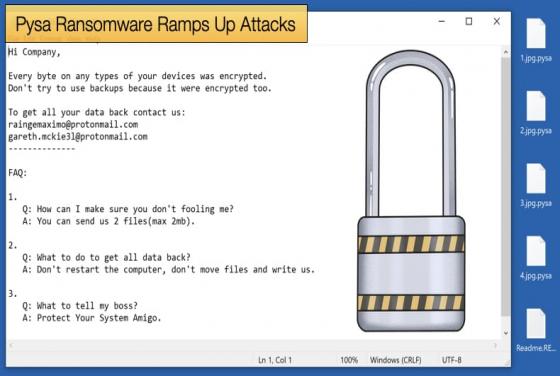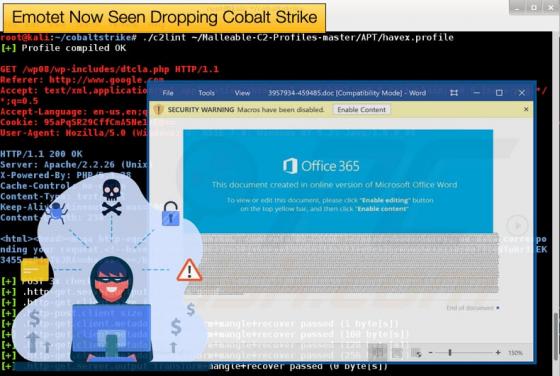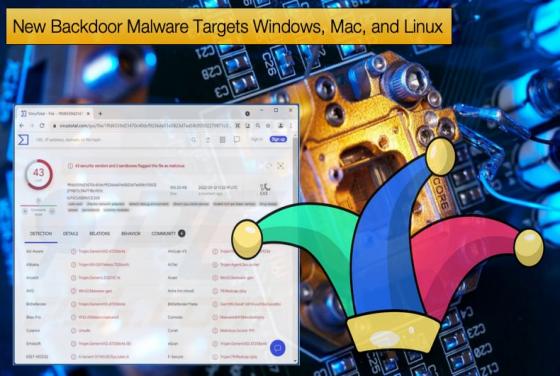

New Backdoor Malware Targets Windows, Mac, and Linux
A group of cybersecurity researchers at Intezer have discovered a new malware strain that is capable of creating backdoors on Windows, Mac, and Linux machines. The malware was discovered in December 2021 and hints at a trend of new malware being developed that is capable of targeting multiple operat