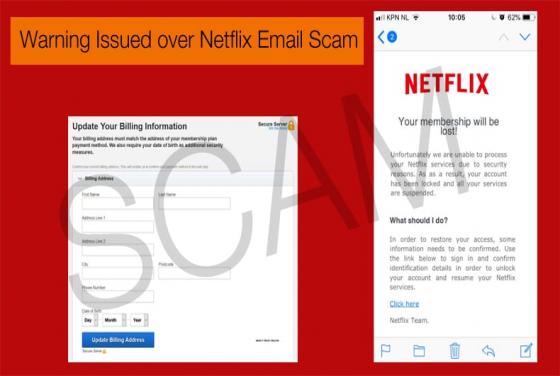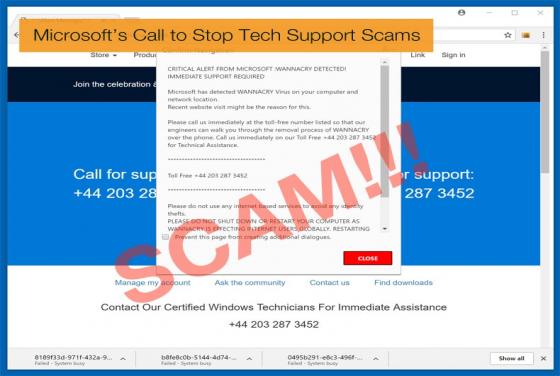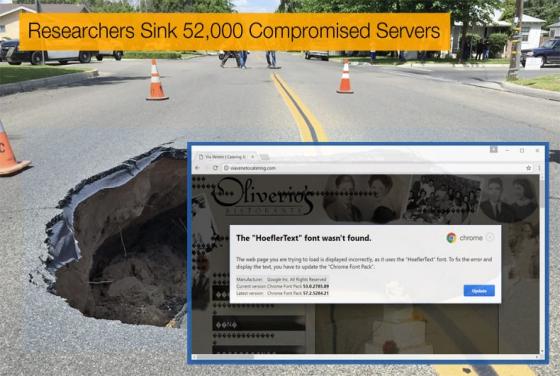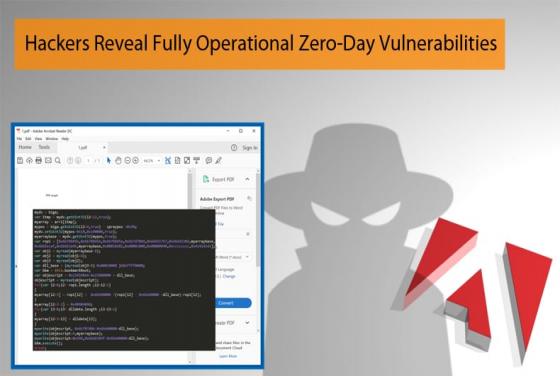

Hackers Reveal Fully Operational Zero-Day Vulnerabilities
There is very little that can be considered more frustrating than realizing all your hard work has been made useless because of a silly mistake. This is probably what a group of hackers must be feeling at the moment. In this instance, the hackers appeared to have accidentally exposed two fully-worki