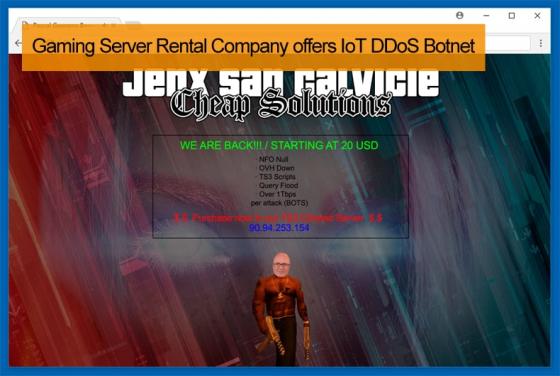
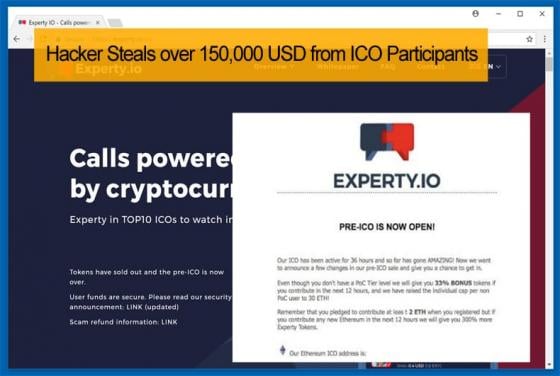
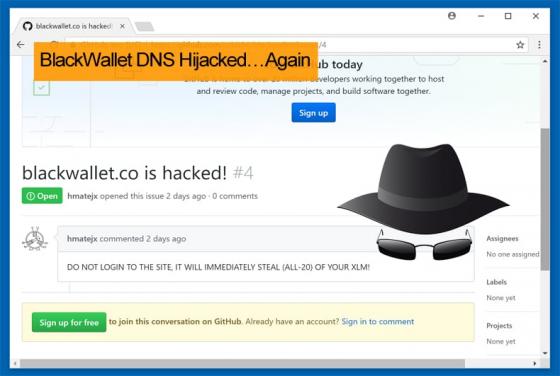
Faraday Cage Protected Equipment Hacked
A group of scientists based at the Cyber Security Research Center at the Ben-Gurion University of the Negev in Israel have just released papers detailing how they managed to hack devices protected by a Faraday Cage. The team has developed a reputation for some extraordinary and generally spectacular