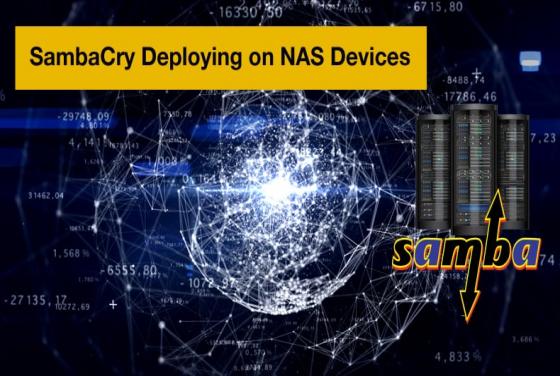
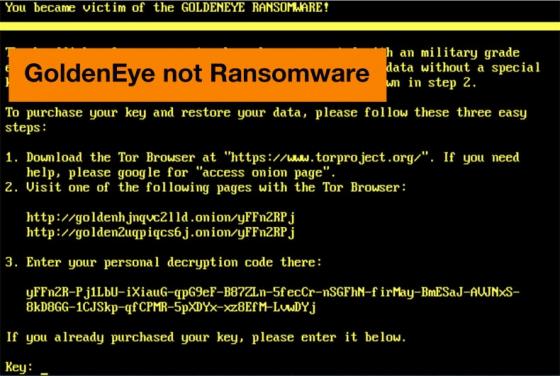
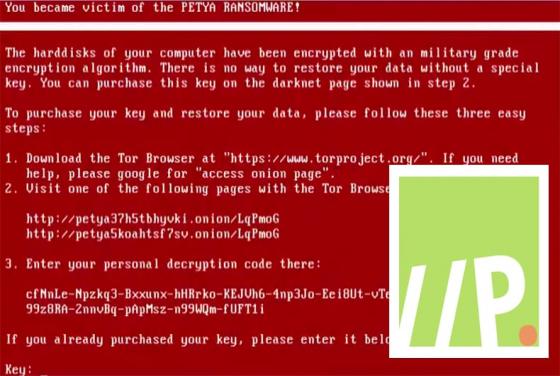
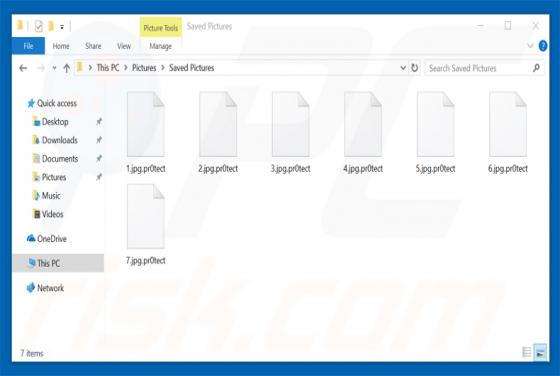
Lippizan Spyware Discovered
Google’s Android security team have discovered and new and immensely powerful spyware termed Lippizan. Google claims the spyware was created by Equus Group, an Israeli based company who by their own account specializes in the development of “…of tailor made innovative solutions for law enforcement,