How to eliminate the AID malware from the compromised device
TrojanAlso Known As: AID loader/clipper malware
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What kind of malware is AID?
AID is malware that functions as a loader and a clipper. It is written in C++ programming language. AID is promoted on a hacker forum. It is sold for $75 (at the moment, its developer uses a sales promotion and sells AID for $50).
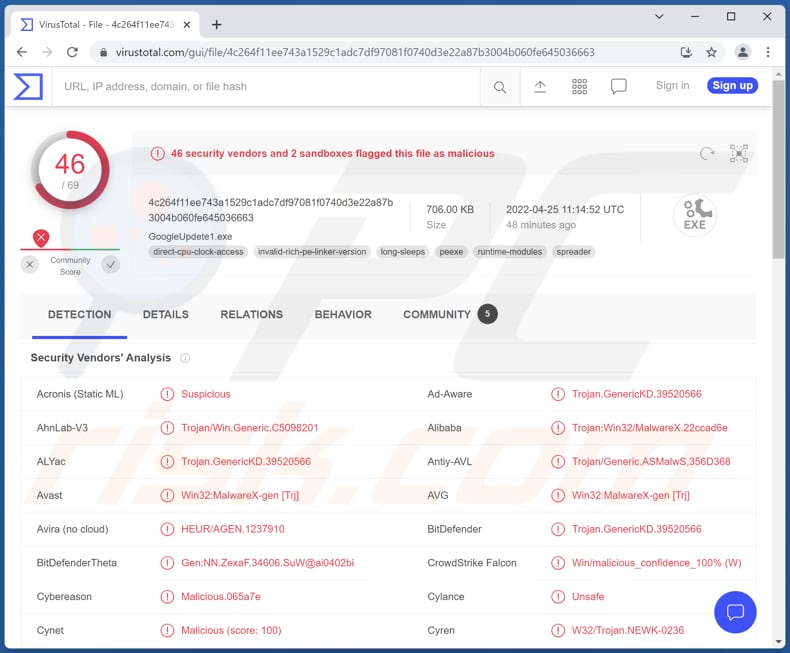
More about AID malware
AID can execute EXE (executable) files downloaded via a specified direct link. Operators can download and execute additional malware (or other software) on the infected computer. Also, AID has clipper functionality - it can replace a wallet address saved in the system clipboard with one owned by the threat actor. This feature allows cybercriminals to steal cryptocurrency.
AID can swap Bitcoin, Bitcoin Cash, Dash, Doge, Ethereum, Litecoin, Payeer, Qiwi, WMK, WMR, WMZ, XMR, Yandex, and Zcash crypto wallets. It is controlled through a web panel. Also, AID is a self-updating malware (it automatically updates itself when updates are available).
| Name | AID loader/clipper malware |
| Threat Type | Loader/Clipper |
| Detection Names | Avast (Win32:MalwareX-gen [Trj]), Combo Cleaner (Trojan.GenericKD.39520566), ESET-NOD32 (A Variant Of Win32/Agent.VAZ), Kaspersky (Trojan.Win32.CMY3U.eun), Microsoft (Trojan:Win32/Mamson.A!ac), Full List (VirusTotal) |
| Symptoms | This malware is designed to stealthily infiltrate the victim's computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software 'cracks'. |
| Damage | Monetary loss, additional computer infections. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
AID malware in general
The two AID's functionalities include replacing cryptocurrency wallets saved in the clipboard loading executable files. The first one only works when victims do not notice that they have pasted a different crypto wallet address while making crypto transactions. It is worth mentioning that AID is injected into the Task Scheduler to launch itself at pre-defined times/after specified time intervals.
How did malware infiltrate my computer?
Most cybercriminals use emails, cracked software download pages (and other unreliable sources for downloading software/files), Trojans, and fake updaters/installers to distribute malware. When they use emails to deliver malware, they pretend to be legitimate companies or other entities. Their goal is to trick users into opening malicious links or attachments.
Cybercriminals use various unofficial pages, third-party downloaders, P2P networks, and similar sources to trick users into downloading malicious files/malware. Examples of most commonly used files to distribute malware are MS Office, PDF documents, JavaScript files, archive files, and executables.
How to avoid installation of malware?
Do not open email attachments or links presented in irrelevant emails sent from suspicious/unknown addresses. Always use official pages and direct links as sources for downloading files and programs. Also, use implemented functions or tools provided by the official developers to update or activate the operating system and other software.
Use reputable antivirus software for computer protection. If you believe that your computer is already infected, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
AID malware promoted on a hacker forum:
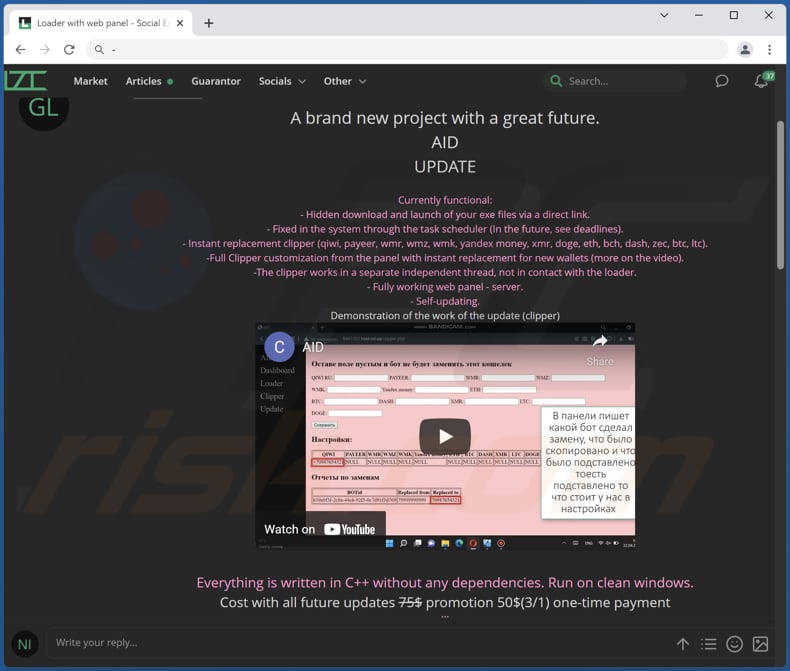
AID's administration panel:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
How to remove malware manually?
Manual malware removal is a complicated task - usually it is best to allow antivirus or anti-malware programs to do this automatically. To remove this malware we recommend using Combo Cleaner Antivirus for Windows.
If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here is an example of a suspicious program running on a user's computer:
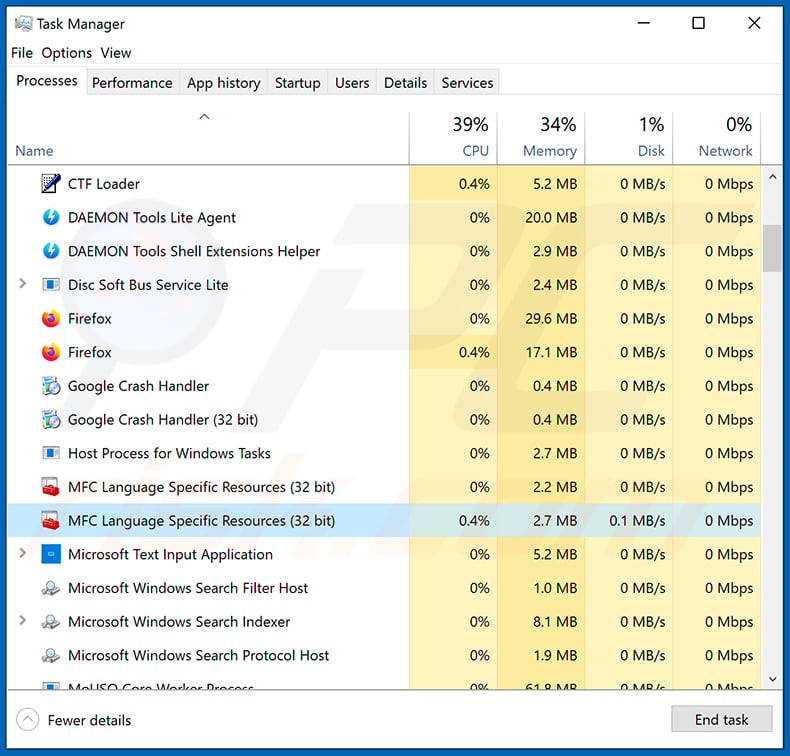
If you checked the list of programs running on your computer, for example, using task manager, and identified a program that looks suspicious, you should continue with these steps:
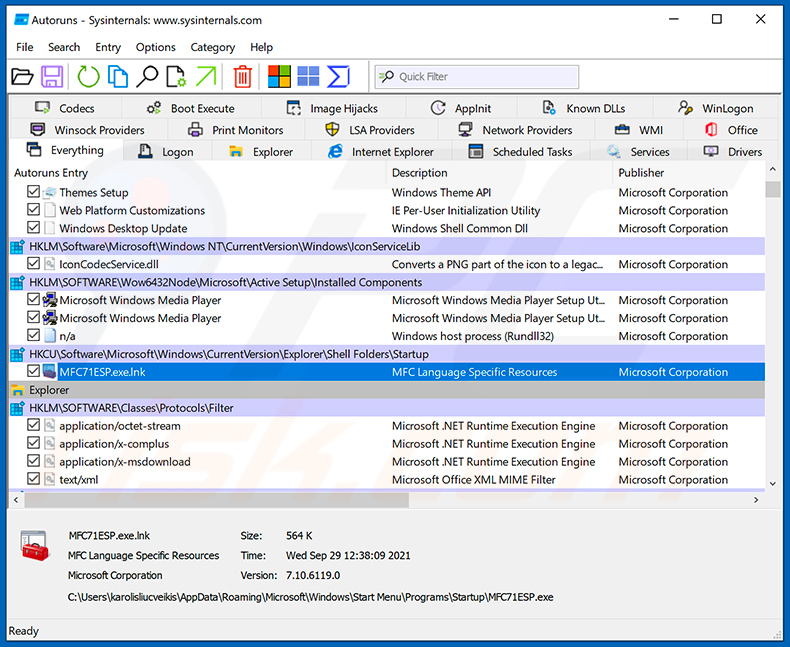
 Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
 Restart your computer into Safe Mode:
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
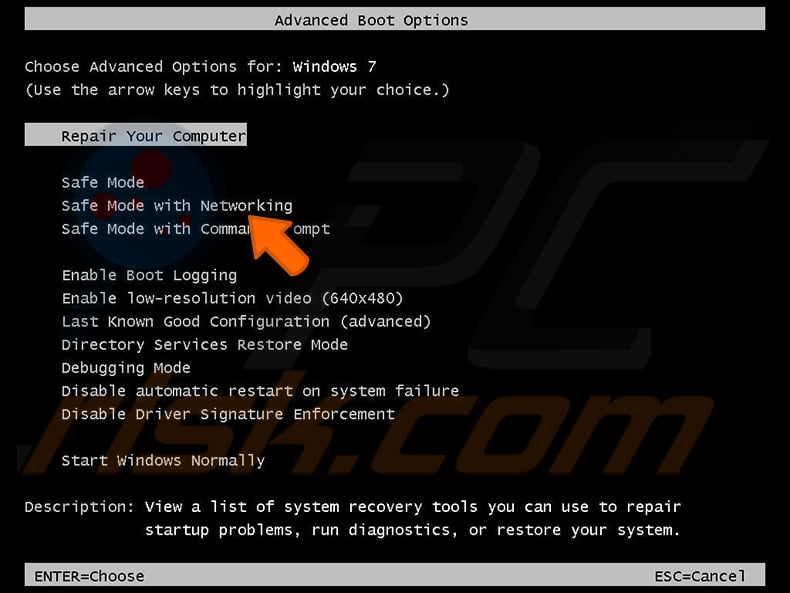
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users: Start Windows 8 is Safe Mode with Networking - Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened "General PC Settings" window, select Advanced startup.
Click the "Restart now" button. Your computer will now restart into the "Advanced Startup options menu". Click the "Troubleshoot" button, and then click the "Advanced options" button. In the advanced option screen, click "Startup settings".
Click the "Restart" button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
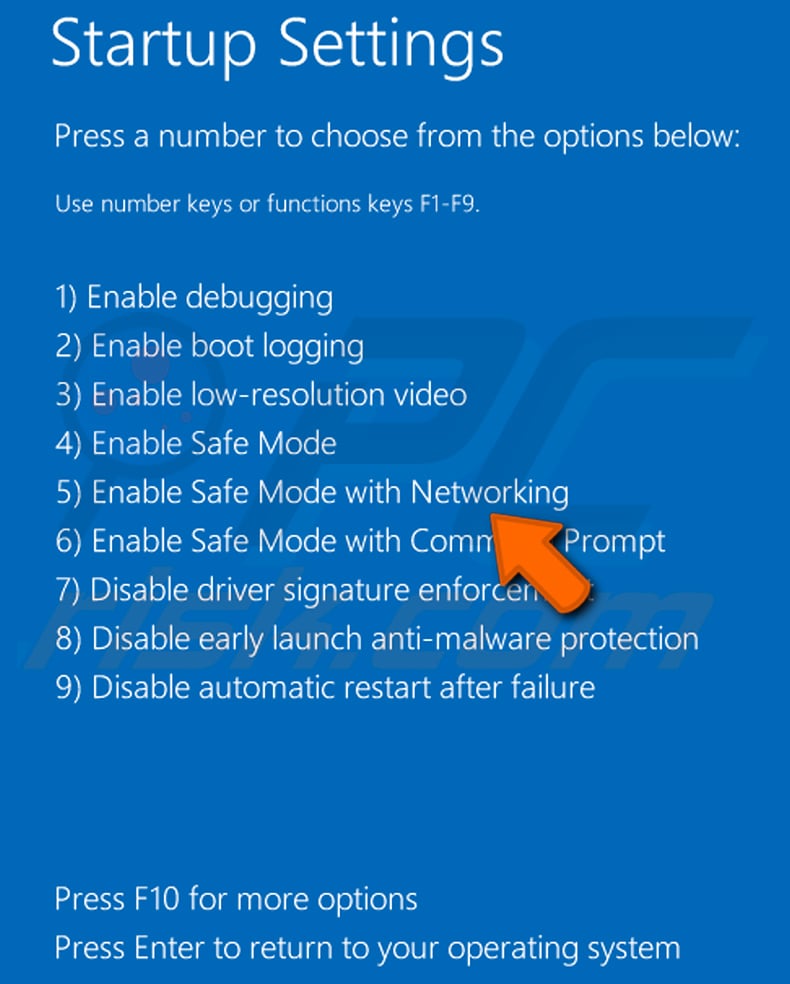
Video showing how to start Windows 8 in "Safe Mode with Networking":
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click "Restart" while holding "Shift" button on your keyboard. In the "choose an option" window click on the "Troubleshoot", next select "Advanced options".
In the advanced options menu select "Startup Settings" and click on the "Restart" button. In the following window you should click the "F5" button on your keyboard. This will restart your operating system in safe mode with networking.
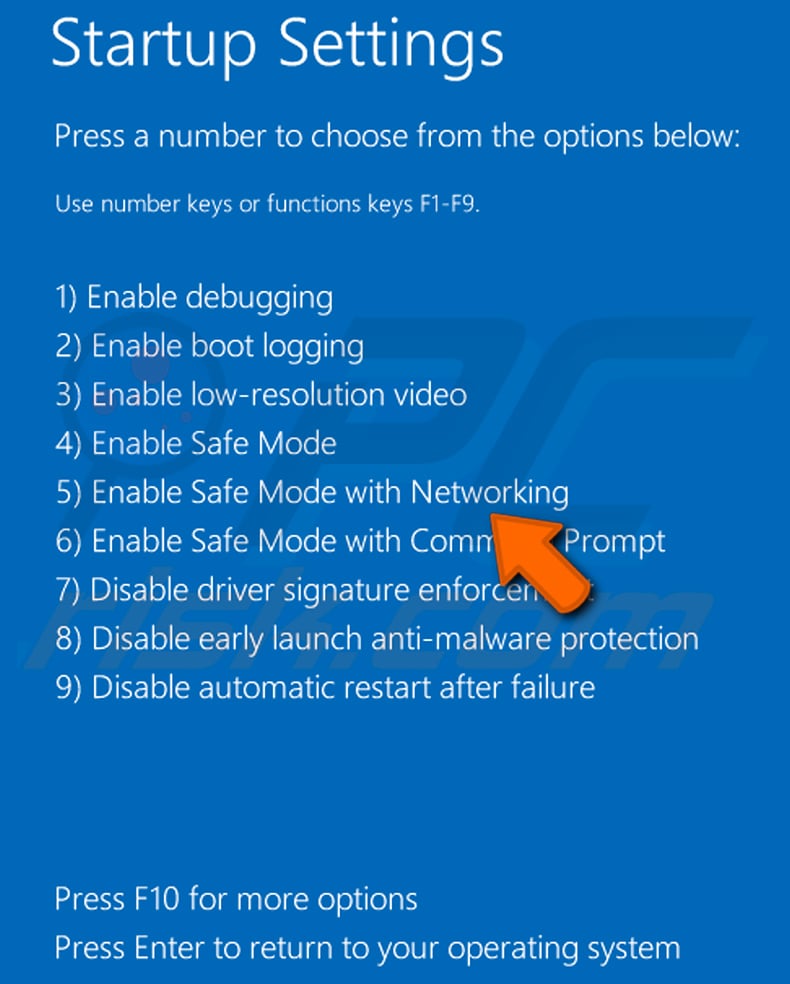
Video showing how to start Windows 10 in "Safe Mode with Networking":
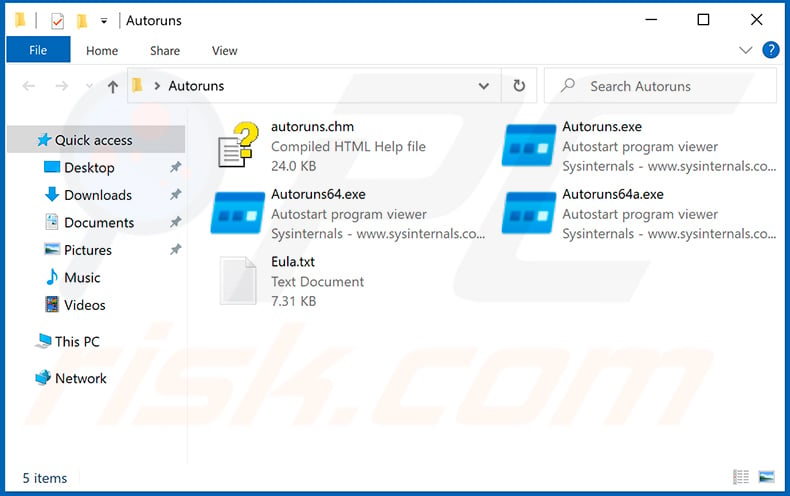
 Extract the downloaded archive and run the Autoruns.exe file.
Extract the downloaded archive and run the Autoruns.exe file.
 In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
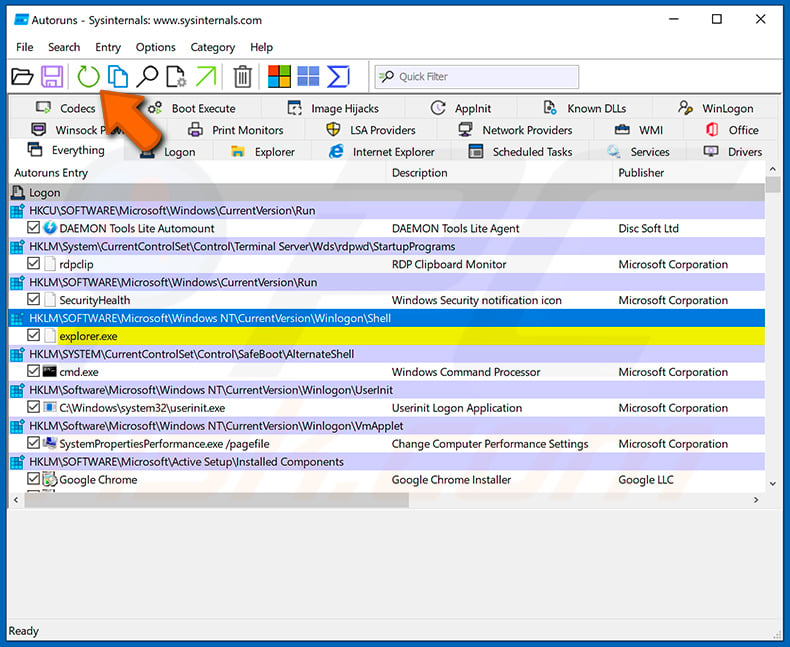
 Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
You should write down its full path and name. Note that some malware hides process names under legitimate Windows process names. At this stage, it is very important to avoid removing system files. After you locate the suspicious program you wish to remove, right click your mouse over its name and choose "Delete".
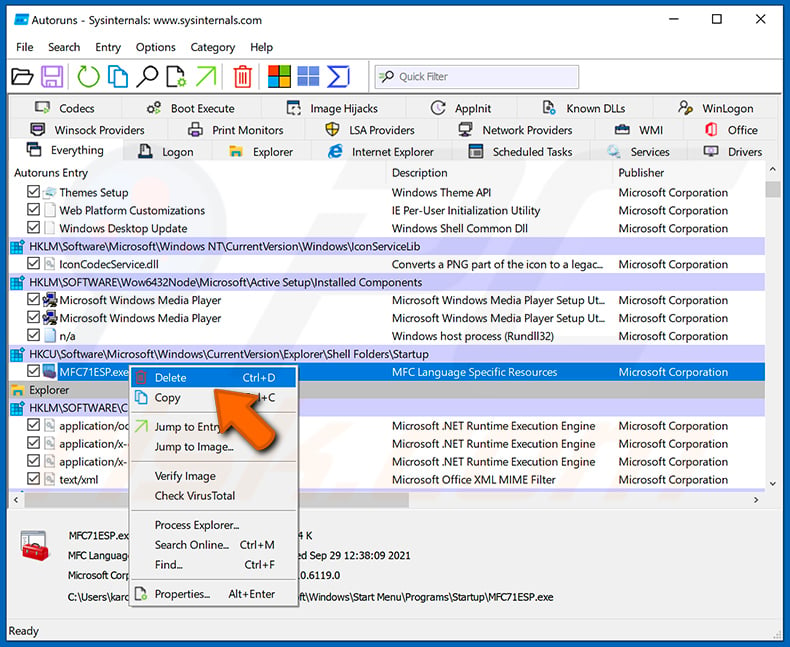
After removing the malware through the Autoruns application (this ensures that the malware will not run automatically on the next system startup), you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the filename of the malware, be sure to remove it.
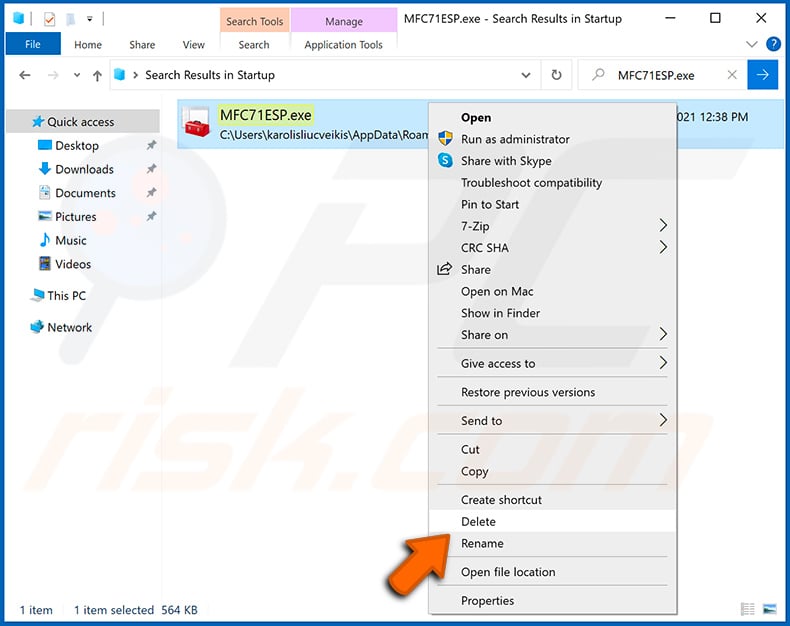
Reboot your computer in normal mode. Following these steps should remove any malware from your computer. Note that manual threat removal requires advanced computer skills. If you do not have these skills, leave malware removal to antivirus and anti-malware programs.
These steps might not work with advanced malware infections. As always it is best to prevent infection than try to remove malware later. To keep your computer safe, install the latest operating system updates and use antivirus software. To be sure your computer is free of malware infections, we recommend scanning it with Combo Cleaner Antivirus for Windows.
Frequently Asked Questions (FAQ)
My computer is infected with AID malware, should I format my storage device to get rid of it?
It is not necessary to format the storage device. AID malware can be removed by following the steps provided above.
What are the biggest issues that malware can cause?
Identity theft, monetary loss, hijacked personal accounts, data loss, and similar issues.
What is the purpose of the AID malware?
AID includes loader and clipper functions. It can execute files downloaded via direct links (infect computers with malware or other unwanted software) and replace crypto wallet addresses saved in the clipboard with those owned by the attackers.
How did a malware infiltrate my computer?
Cybercriminals distribute malware using phishing and other social engineering techniques (e.g., malicious emails, fake system warning messages). Also, they attempt to trick users into opening malicious drive-by downloads, files downloaded via Peer-to-Peer (P2P) networks, unofficial software download websites, and similar sources. Their goal is to trick users into executing malware by themselves.
Will Combo Cleaner protect me from malware?
Yes, Combo Cleaner can detect and remove malware from the operating system. If a computer is infected with high-end malware, it must be scanned using a full scan. Otherwise, antivirus software will not detect malware that hides deep in the operating system.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate


▼ Show Discussion