How to identify scam sites like the "Fake Meteora Website"
Phishing/ScamAlso Known As: Fraudulent Meteora web page
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is the fake Meteora website?
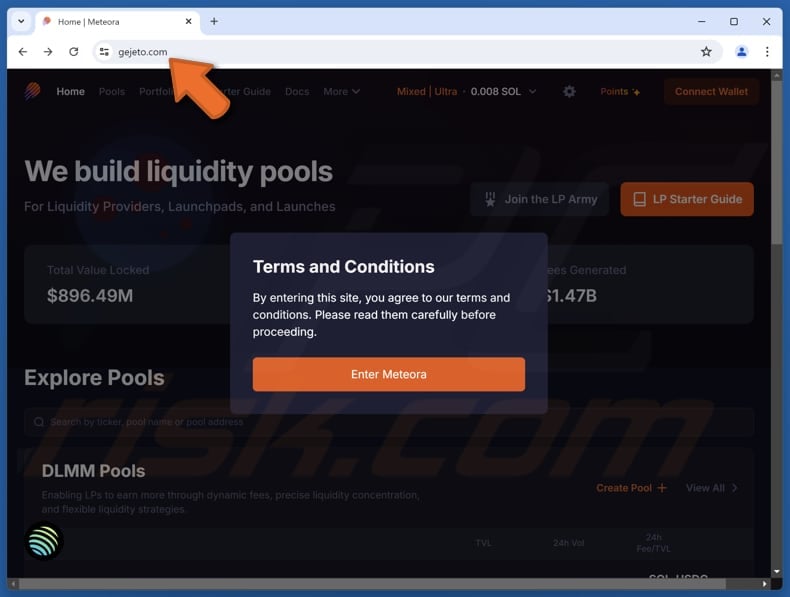
Our team has analysed gejeto[.]com and concluded that it is a deceptive site mimicking the original Meteora website (meteora.ag). Scammers behind the fake page aim to trick visitors into performing certain steps, allowing them to commit cryptocurrency theft. This page should be avoided.
IMPORTANT NOTE: We do not review crypto projects, please do your own research when investing money.
Federal Trade Commission (FTC) states that since the start of 2021, more than 46,000 people have reported losing over $1 billion in crypto to scams – that's about one out of every four dollars reported lost, more than any other payment method.
Fake Meteora website in detail
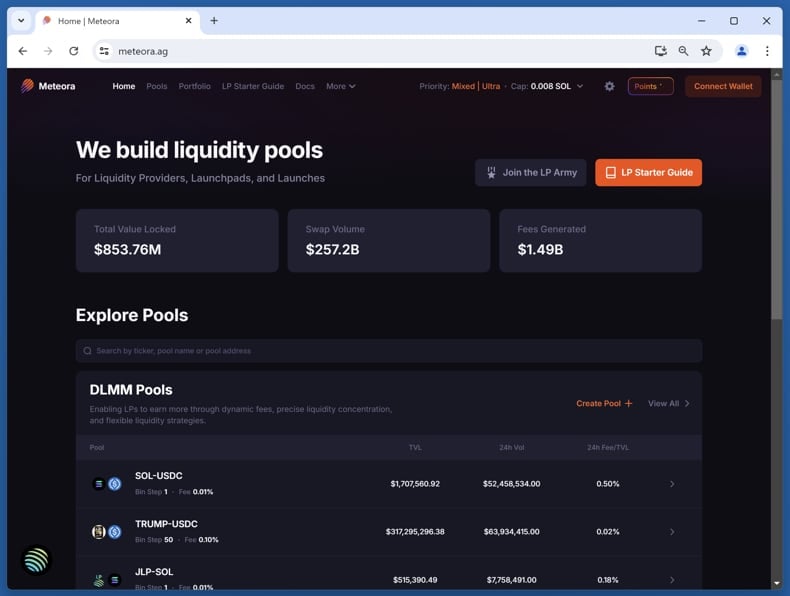
Meteora (meteora.ag) is a platform dedicated to building dynamic liquidity pools for the cryptocurrency ecosystem. For liquidity providers, Meteora offers innovative solutions that allow participants to earn competitive fees and yield on their capital. The platform also provides comprehensive infrastructure and tools for launchpads.
Additionally, users can discover and participate in new token launches directly through Meteora. On the fake site (gejeto[.]com), users are encourages to enter Meteora by connecting their wallets. When visitors connect their wallets, they unknowingly activate a cryptocurrency drainer that transfers their funds to the scammer's wallet.
Since cryptocurrency transactions are irreversible, stolen funds are usually impossible to recover. Therefore, it is crucial to be cautious when interacting with unofficial or suspicious platforms to avoid becoming a victim of scams, losing money, or encountering other issues.
| Name | Fraudulent Meteora web page |
| Threat Type | Scam, Social Engineering, Fraud |
| Fake Claim | Visitors can use the site enter Meteora community |
| Disguise | Legitimate Meteora site |
| Related Domain | gejeto[.]com |
| Detection Names | N/A (VirusTotal) |
| Symptoms | Unofficial domain, lack of official verification, unrealistic claims, too good-to-be-true promises |
| Distribution methods | Fake social media accounts, deceptive websites, rogue online advertisements |
| Damage | Cryptocurrency theft |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Similar scams in general
These types of scams usually pose as legitimate platforms (e.g., crypto exchanges) to deceive users into granting access to their cryptocurrency. Interacting with such sites can result in funds being stolen, and recovery is generally not possible. Users should always examine crypto platforms before interacting with them to avoid the associated risks.
More examples of crypto scams are "Mitosis Airdrop", "Claim $STREAMER", and "OpenxAI Staking".
How did I open a scam website?
Fraudsters trick users into visiting websites that use cryptocurrency drainers mostly through hacked or fake social media accounts (usually on Twitter/X and Facebook) as well as compromised WordPress sites. Users may also encounter scams via deceptive emails and notifications from untrustworthy websites.
In addition, malicious advertising networks, commonly appearing on torrent platforms, adult sites, and illegal streaming services, ads generated by adware, or misleading buttons and links on suspicious sites can be used to promote scams.
How to avoid visiting scam pages?
Avoid clicking links in unsolicited emails, social media messages, or pop-ups. Do not allow notifications from untrusted sites. Get software, apps, and files exclusively from official websites or authorized app stores. Regularly update your operating system and applications.
Use reputable security software and perform frequent scans. If your computer is already infected with unwanted apps, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate them.
The appearance of the fake Meteora website scam (GIF):
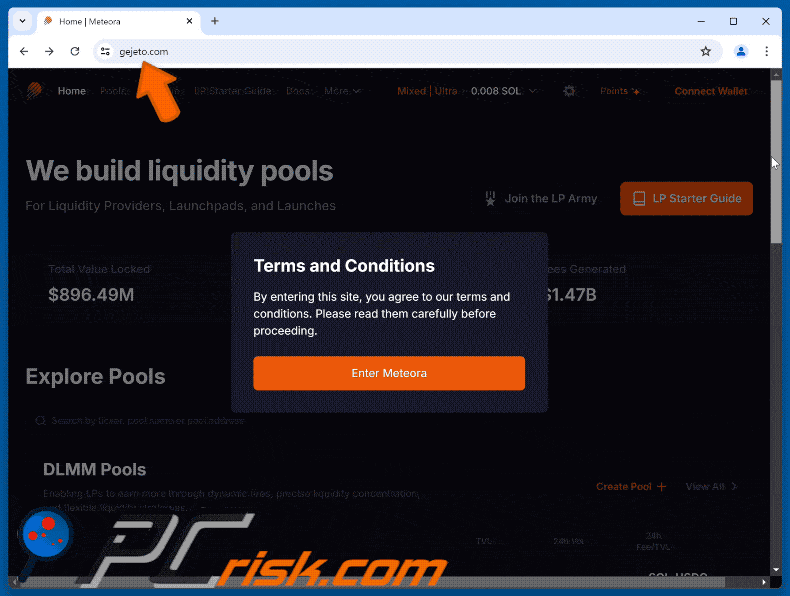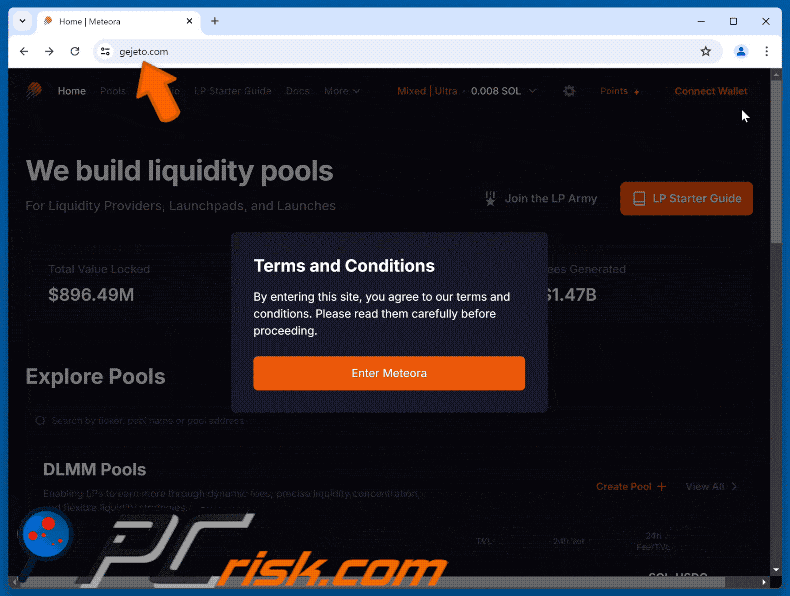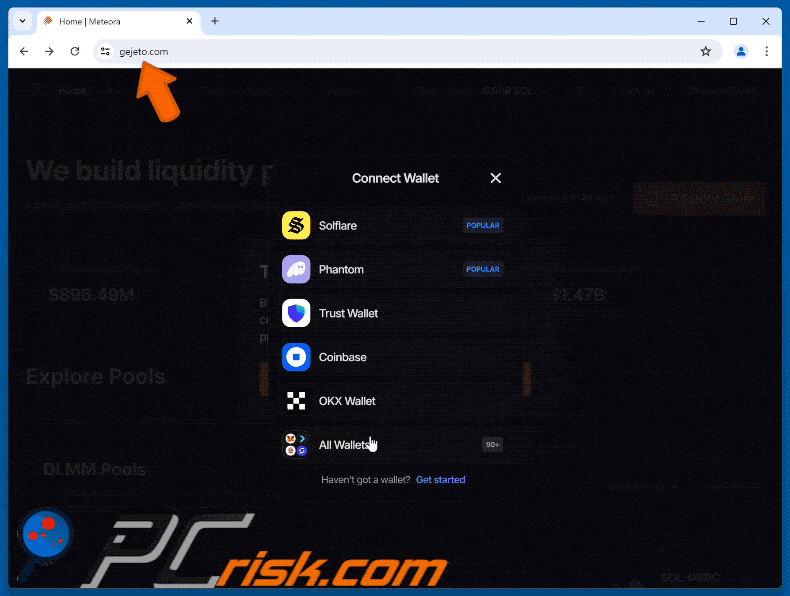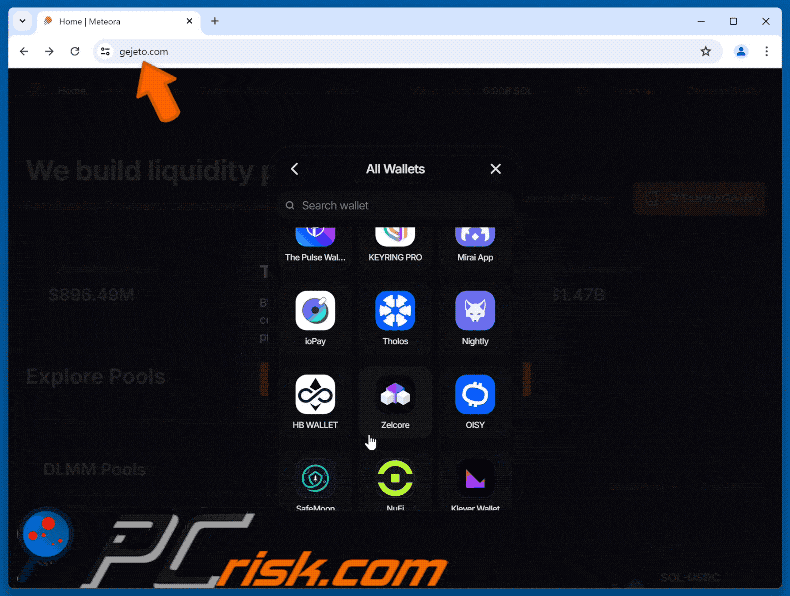
The original Meteora site (meteora.ag):
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Fraudulent Meteora web page?
- How to identify a pop-up scam?
- How do pop-up scams work?
- How to remove fake pop-ups?
- How to prevent fake pop-ups?
- What to do if you fell for a pop-up scam?
How to identify a pop-up scam?
Pop-up windows with various fake messages are a common type of lures cybercriminals use. They collect sensitive personal data, trick Internet users into calling fake tech support numbers, subscribe to useless online services, invest in shady cryptocurrency schemes, etc.
While in the majority of cases these pop-ups don't infect users' devices with malware, they can cause direct monetary loss or could result in identity theft.
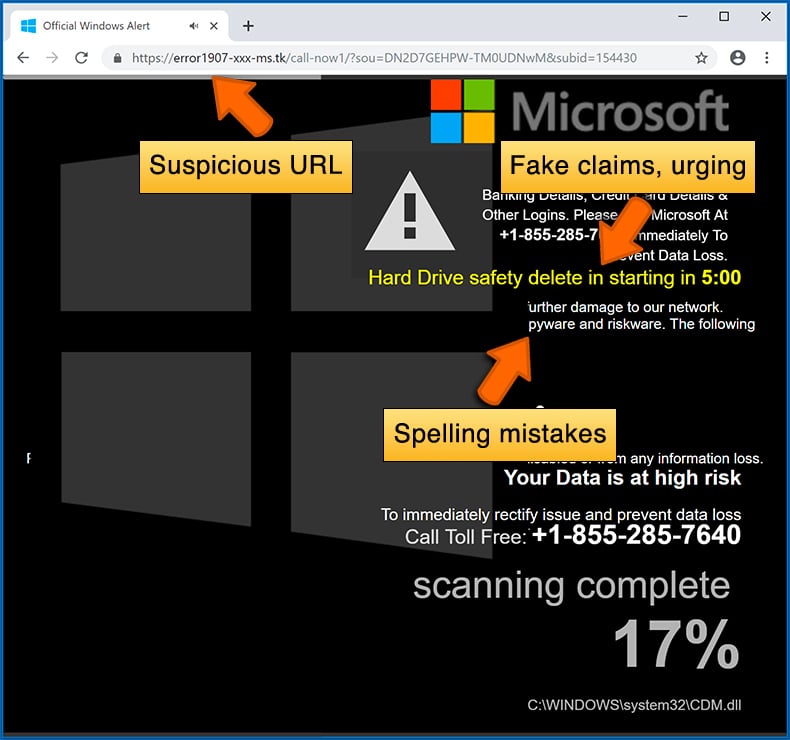
Cybercriminals strive to create their rogue pop-up windows to look trustworthy, however, scams typically have the following characteristics:
- Spelling mistakes and non-professional images - Closely inspect the information displayed in a pop-up. Spelling mistakes and unprofessional images could be a sign of a scam.
- Sense of urgency - Countdown timer with a couple of minutes on it, asking you to enter your personal information or subscribe to some online service.
- Statements that you won something - If you haven't participated in a lottery, online competition, etc., and you see a pop-up window stating that you won.
- Computer or mobile device scan - A pop-up window that scans your device and informs of detected issues - is undoubtedly a scam; webpages cannot perform such actions.
- Exclusivity - Pop-up windows stating that only you are given secret access to a financial scheme that can quickly make you rich.
Example of a pop-up scam:
How do pop-up scams work?
Cybercriminals and deceptive marketers usually use various advertising networks, search engine poisoning techniques, and shady websites to generate traffic to their pop-ups. Users land on their online lures after clicking on fake download buttons, using a torrent website, or simply clicking on an Internet search engine result.
Based on users' location and device information, they are presented with a scam pop-up. Lures presented in such pop-ups range from get-rich-quick schemes to fake virus scans.
How to remove fake pop-ups?
In most cases, pop-up scams do not infect users' devices with malware. If you encountered a scam pop-up, simply closing it should be enough. In some cases scam, pop-ups may be hard to close; in such cases - close your Internet browser and restart it.
In extremely rare cases, you might need to reset your Internet browser. For this, use our instructions explaining how to reset Internet browser settings.
How to prevent fake pop-ups?
To prevent seeing pop-up scams, you should visit only reputable websites. Torrent, Crack, free online movie streaming, YouTube video download, and other websites of similar reputation commonly redirect Internet users to pop-up scams.
To minimize the risk of encountering pop-up scams, you should keep your Internet browsers up-to-date and use reputable anti-malware application. For this purpose, we recommend Combo Cleaner Antivirus for Windows.
What to do if you fell for a pop-up scam?
This depends on the type of scam that you fell for. Most commonly, pop-up scams try to trick users into sending money, giving away personal information, or giving access to one's device.
- If you sent money to scammers: You should contact your financial institution and explain that you were scammed. If informed promptly, there's a chance to get your money back.
- If you gave away your personal information: You should change your passwords and enable two-factor authentication in all online services that you use. Visit Federal Trade Commission to report identity theft and get personalized recovery steps.
- If you let scammers connect to your device: You should scan your computer with reputable anti-malware (we recommend Combo Cleaner Antivirus for Windows) - cyber criminals could have planted trojans, keyloggers, and other malware, don't use your computer until removing possible threats.
- Help other Internet users: report Internet scams to Federal Trade Commission.
Frequently Asked Questions (FAQ)
What is a fake crypto website?
A fake crypto website is a fraudulent online platform created to deceive users into thinking it is a legitimate cryptocurrency exchange, wallet service, project, or investment opportunity.
What is the purpose of a fake crypto page?
Fake crypto websites trick users into connecting their wallets, sharing login details or private keys, or sending cryptocurrency under the false promise of rewards, giveaways, or investments. These actions typically result in stolen funds or compromised accounts.
Why do I encounter scam websites?
Scammers drive users to harmful websites using hacked or fraudulent social media profiles, compromised websites, and malicious advertising networks. Users may also end up on these pages through deceptive emails, intrusive pop-ups (or other content on shady sites), fake notifications, and ads presented by installed adware.
Will Combo Cleaner protect me from scams?
Combo Cleaner checks visited websites and detects potentially malicious or fraudulent ones. If a threat is found, it notifies the user and prevents access to the malicious page.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion