Defenceprogramm.com Ads
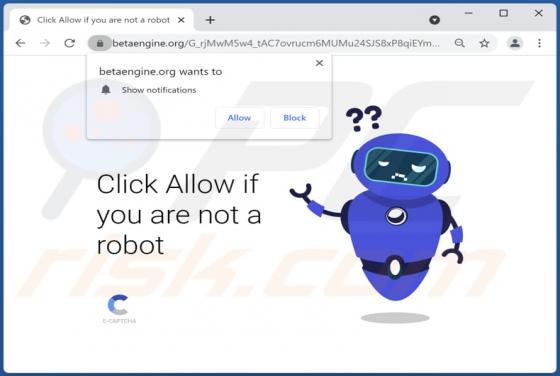
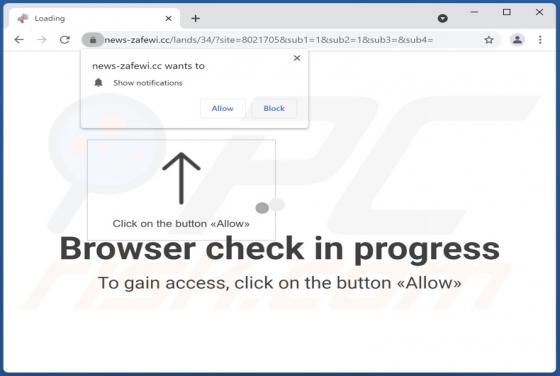
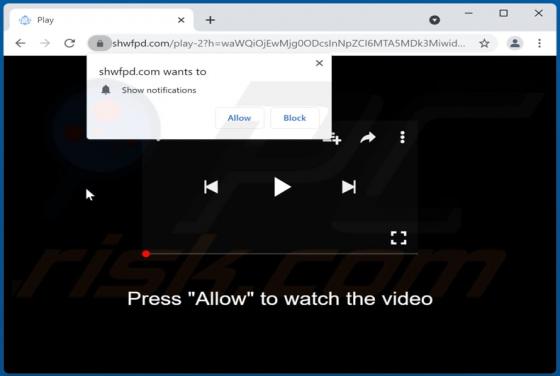
Defenceprogramm[.]com is a rogue site that our research team found while inspecting deceptive webpages. This page operates by promoting scams, pushing browser notification spam, and redirecting visitors to other (likely untrustworthy/malicious) websites. Users typically enter webpages like defenc