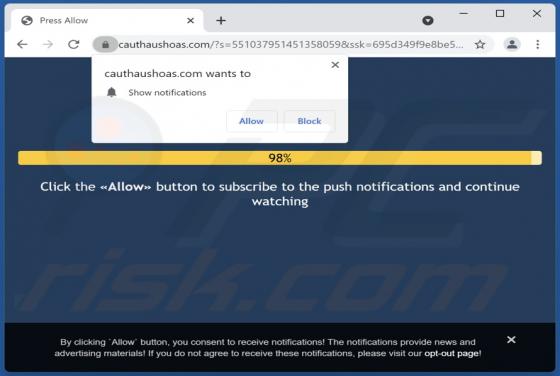
Cauthaushoas.com Ads
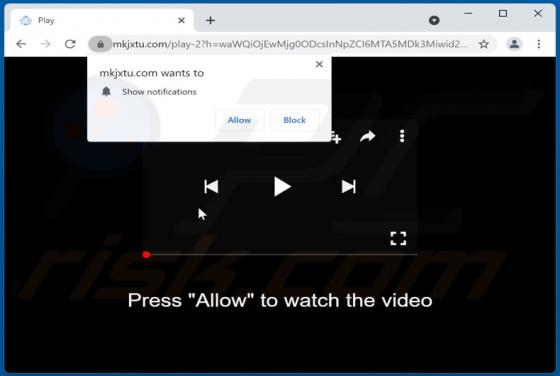
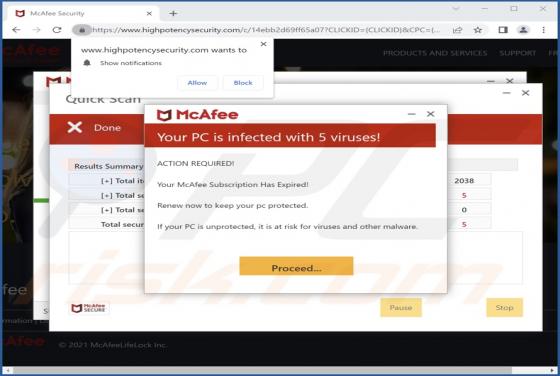
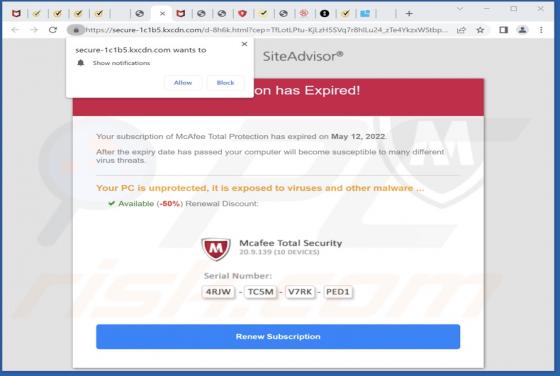
While inspecting questionable websites, our research team discovered the cauthaushoas[.]com rogue webpage. It is designed to host dubious content, promote browser notification spam, and redirect visitors to other (likely unreliable/malicious) sites. Most users enter websites like cauthaushoas[.]c