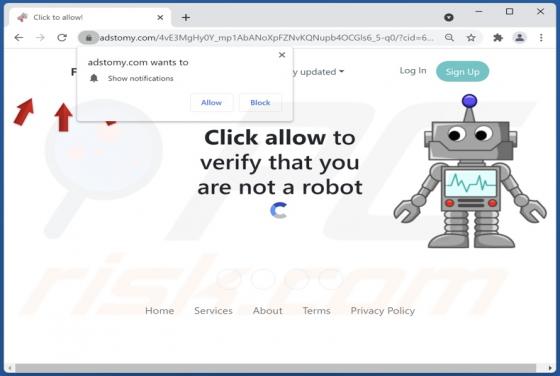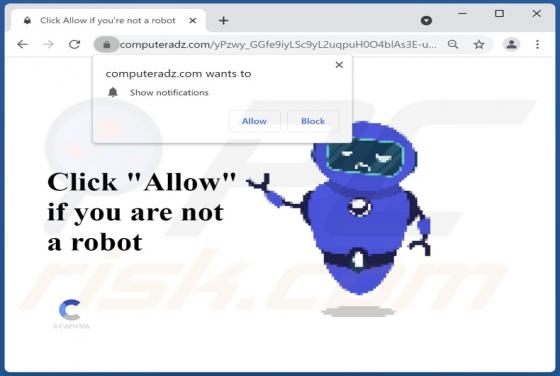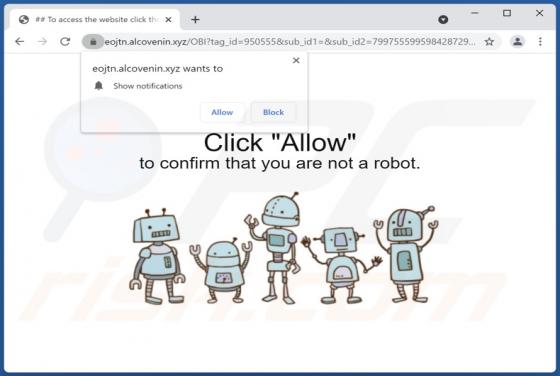
Captchamode.top Ads
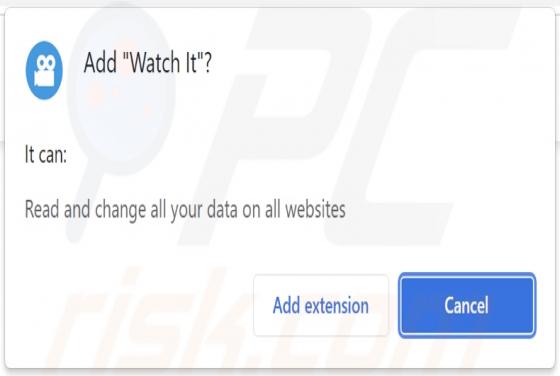
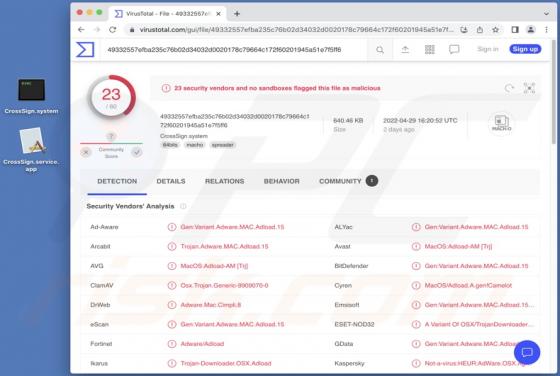
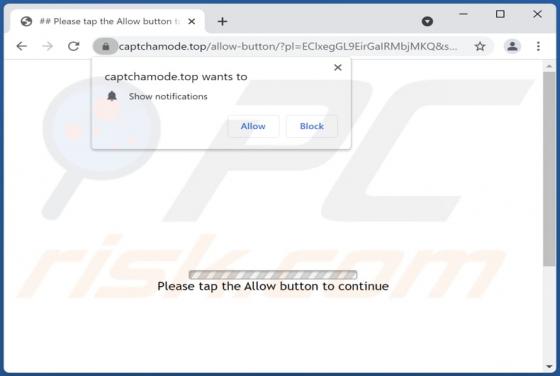
Captchamode[.]top is designed to display deceptive content to trick visitors into allowing it to deliver untrustworthy notifications. Additionally, it can redirect to various shady websites. In most cases, pages like captchamode[.]top are visited inadvertently. We have discovered this site while a