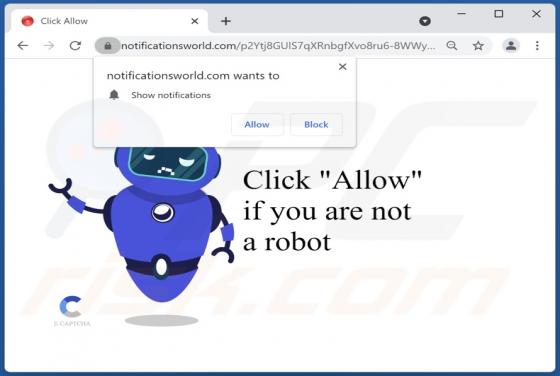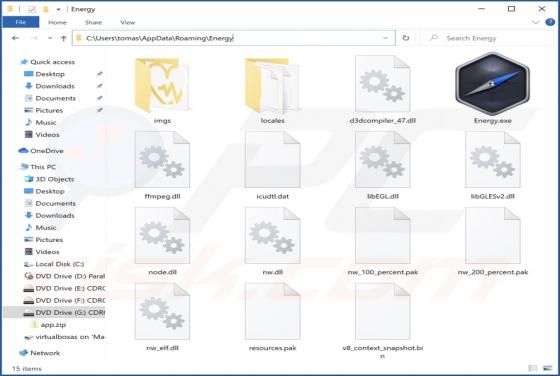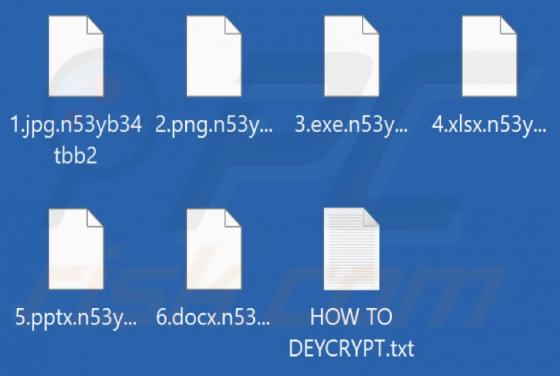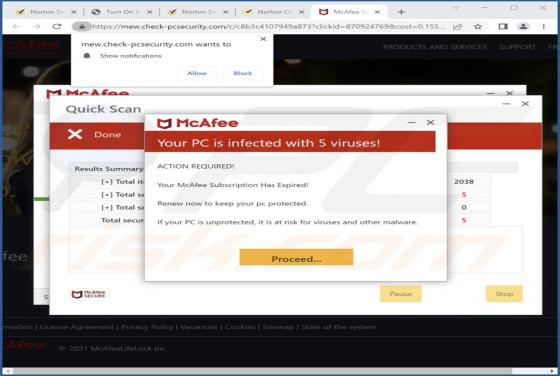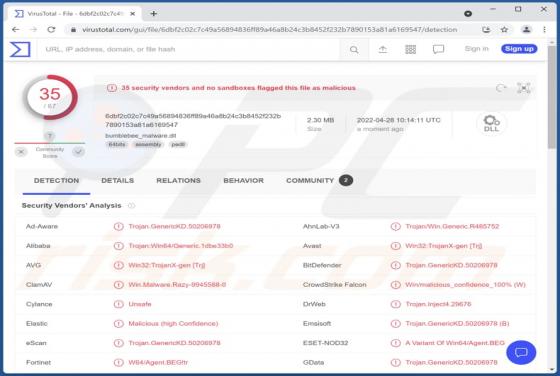
Bumblebee Malware
Bumblebee is the name of a malware loader. It is known that cybercriminals use it as a downloader for Cobalt Strike and possibly other malware such as ransomware. Bumblebee appears to be a replacement for BazaLoader - another malware loader. Bumblebee is delivered via ISO files that contai