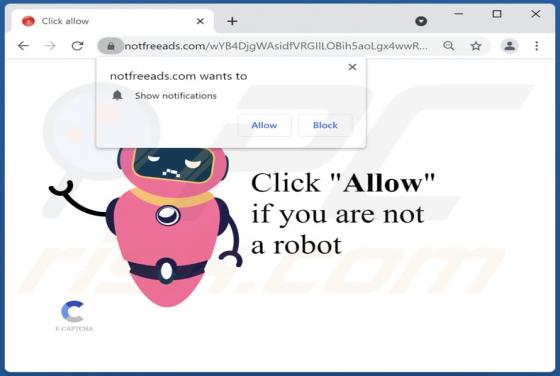
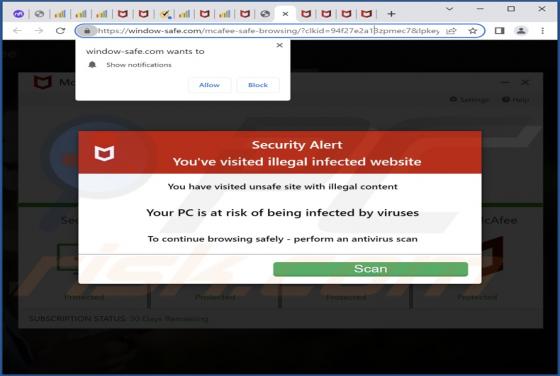
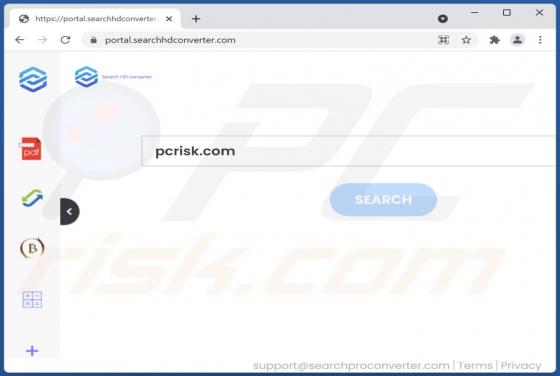
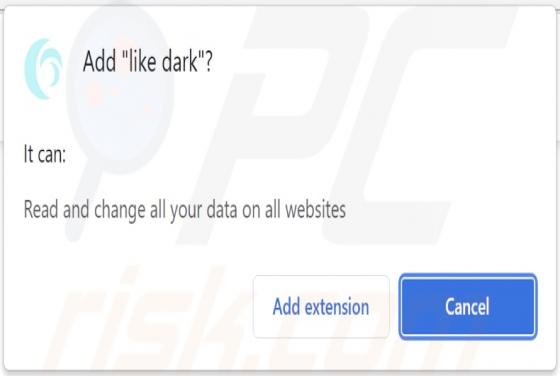
Whisper Stealer Malware
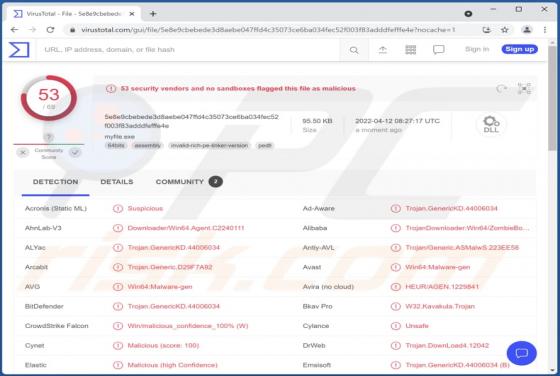
Whisper Stealer is an information stealer targeting Chromium and Gecko browsers, cryptocurrency wallets, Discord tokens, and Telegram sessions (and other data). It is promoted (and sold) on hacker forums. There are five available subscription plans: 250 rubles for one month, 600 rubles for three