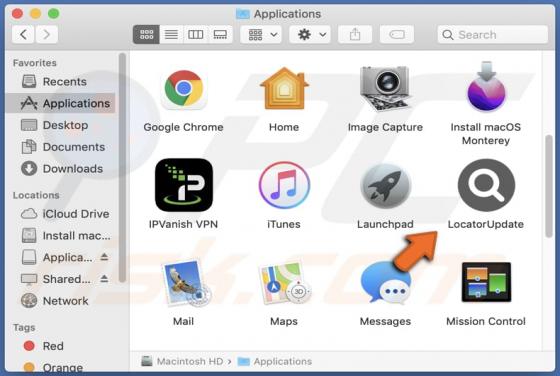
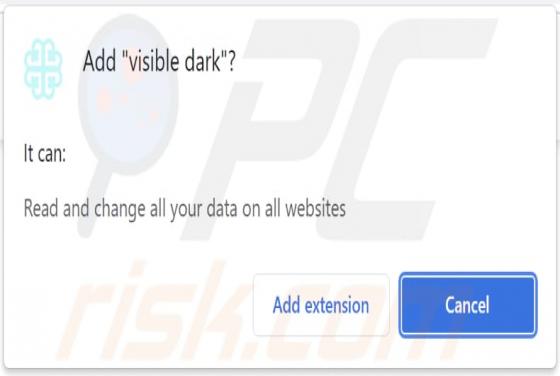
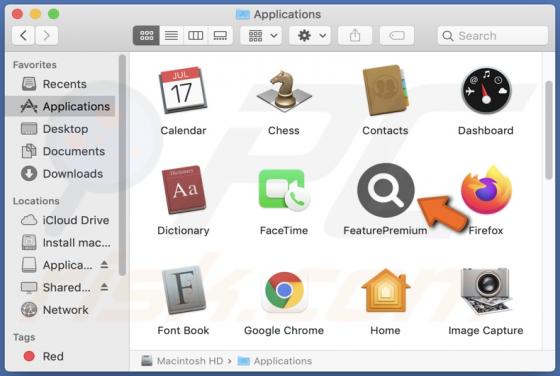
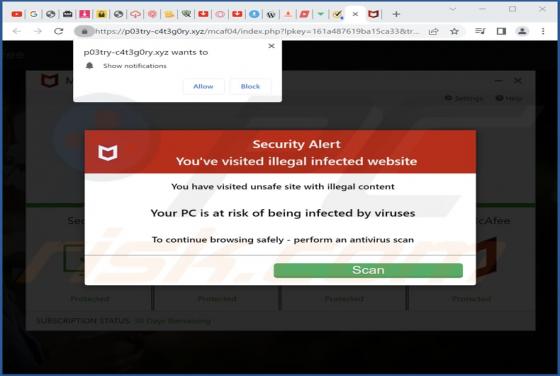
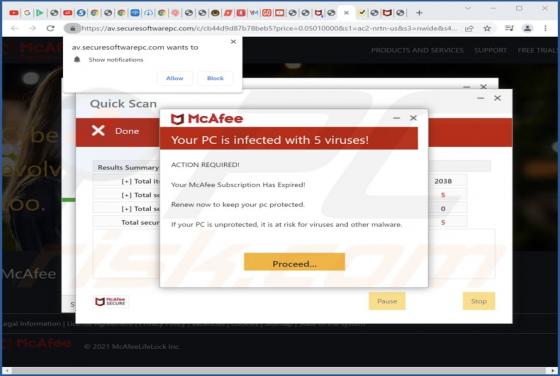
DeezNuts Crypter Ransomware
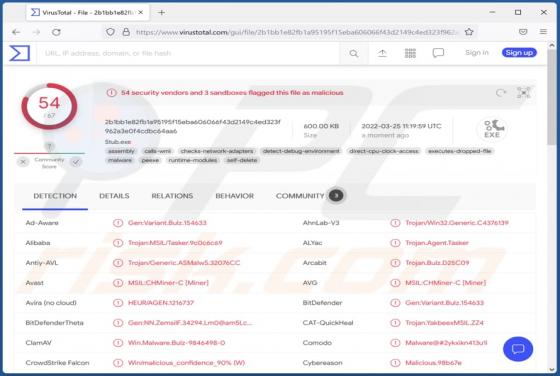
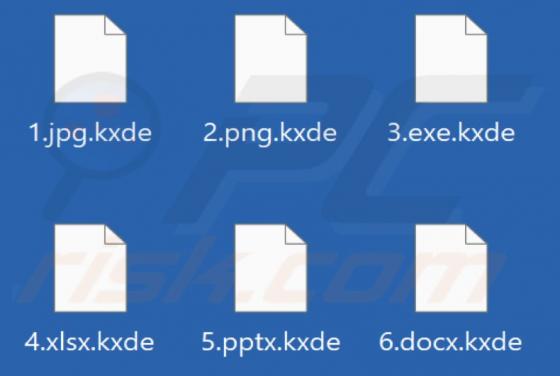
DeezNuts Crypter is a piece of malicious software classified as ransomware. Our research team found it while inspecting new submissions to VirusTotal. After being launched on our test machine, this ransomware encrypted files and renamed them by inserting ".deeznuts-crypter" between the original f