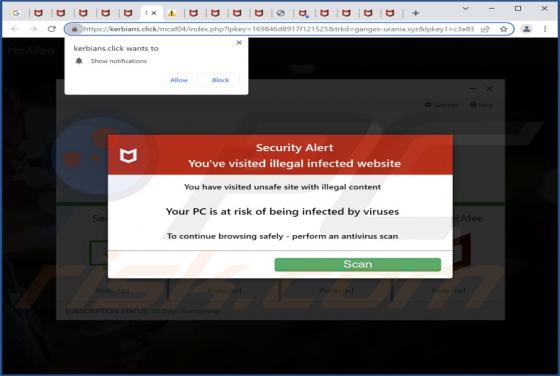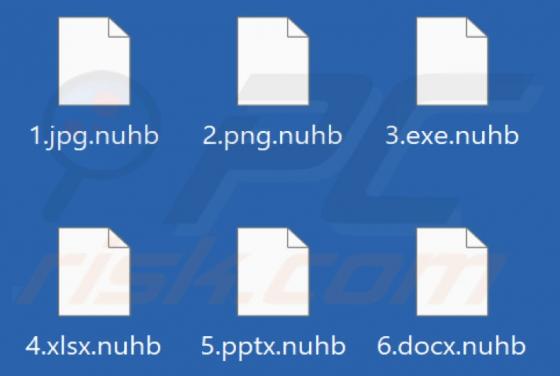
Nuhb Ransomware
We have discovered a new Djvu ransomware variant called Nuhb. It was found while examining malware samples submitted to VirusTotal. While analyzing Nuhb, we learned that it encrypts files and appends the ".nuhb" extension to filenames. Also, it provides a ransom note - it creates a text file named