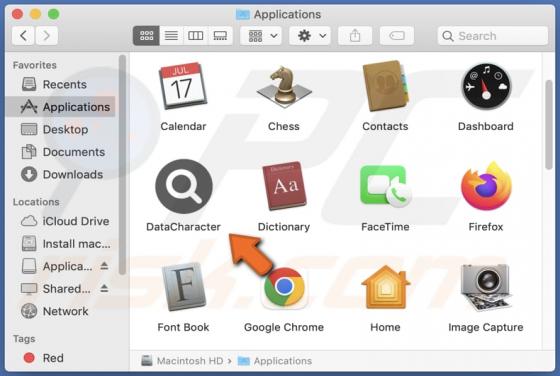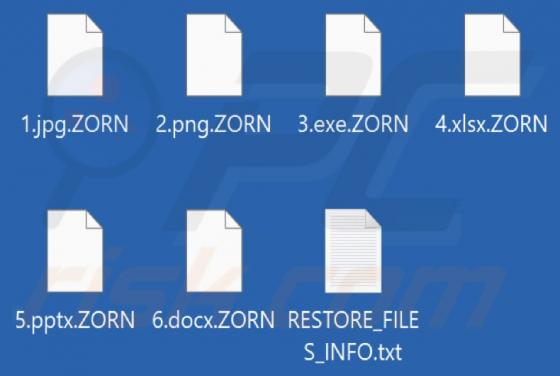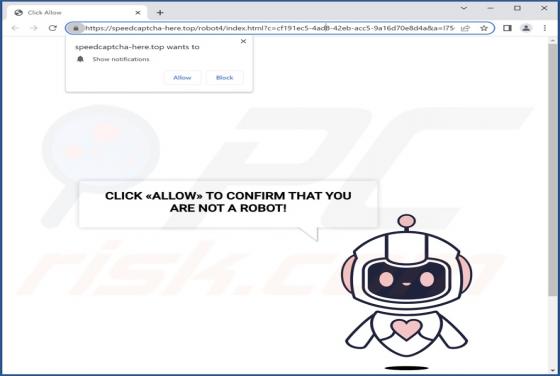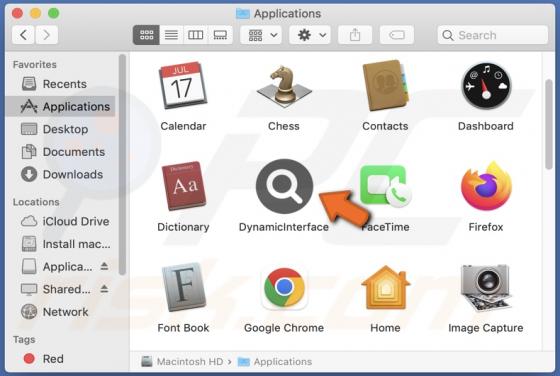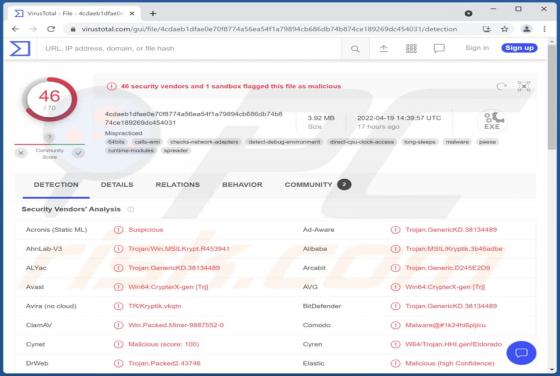
Kratos Silent Miner
Kratos Silent Miner is the name of ETC (Ethereum Classic) and ETH (Ethereum) cryptocurrency miner with various options and builds. We have discovered this miner on a hacker forum. Its developer offers to purchase a monthly subscription (with 24/7 support on Telegram) for $100. Kratos Silen