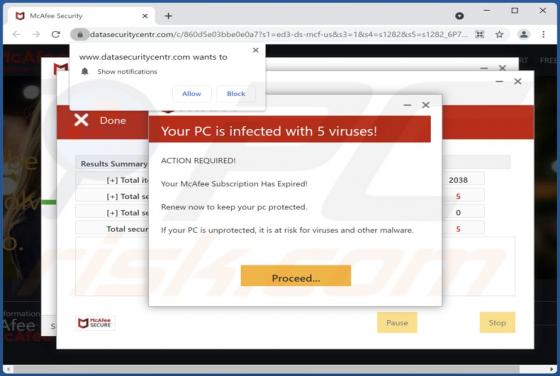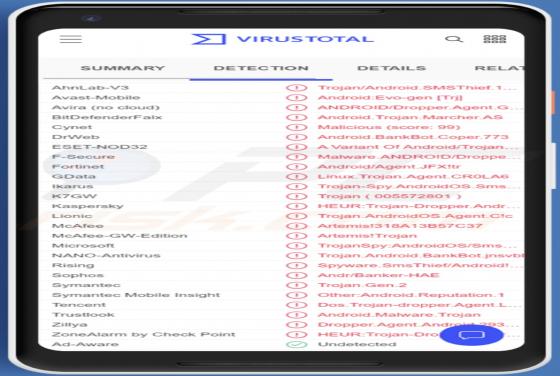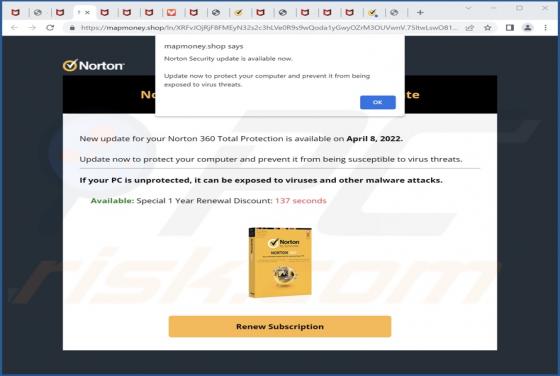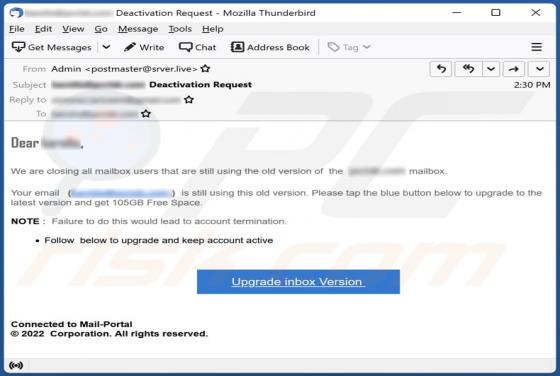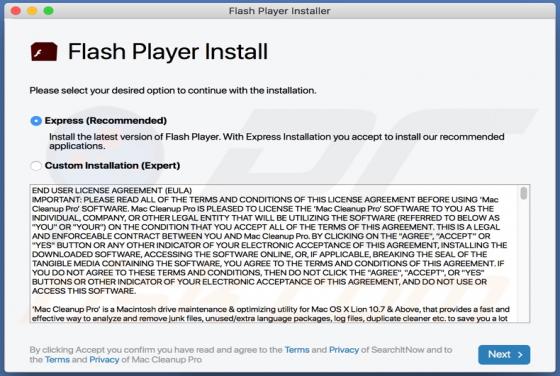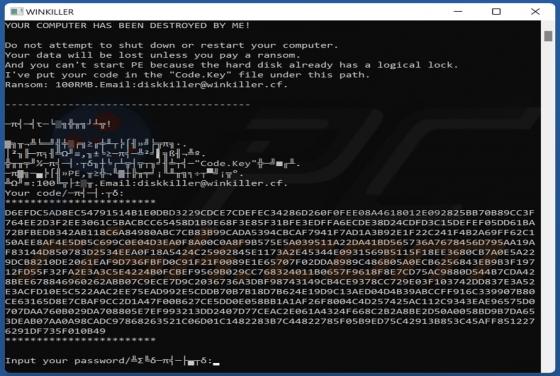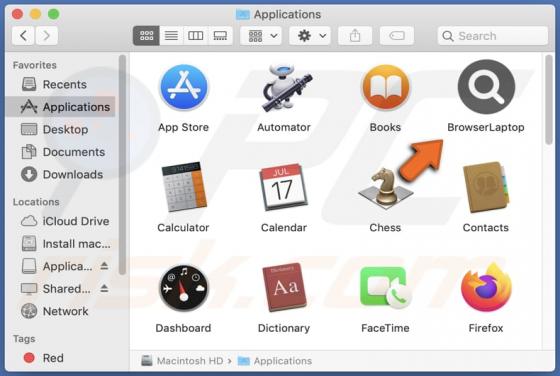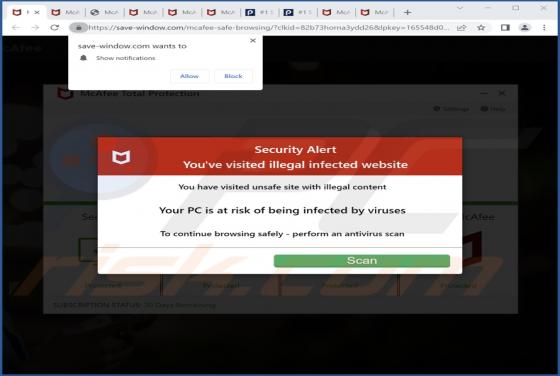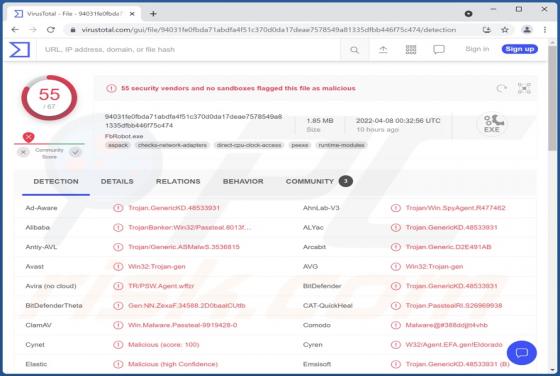
FFDroider Stealer
FFDroider is a malicious program classified as a stealer. It is designed to extract and exfiltrate sensitive data from infected devices. FFDroider targets popular social media and e-commerce platforms in particular. FFDroider has been observed evading detection by masquerading as the Teleg