DHL Express Import Shipment On Hold Email Virus
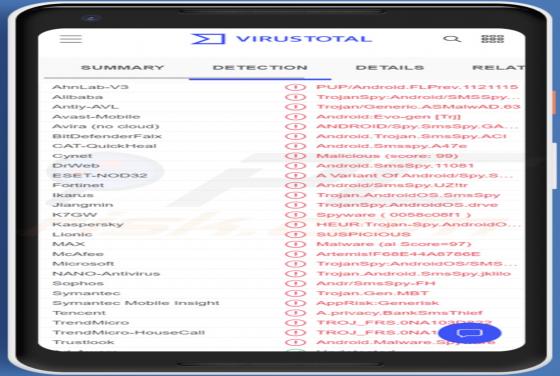
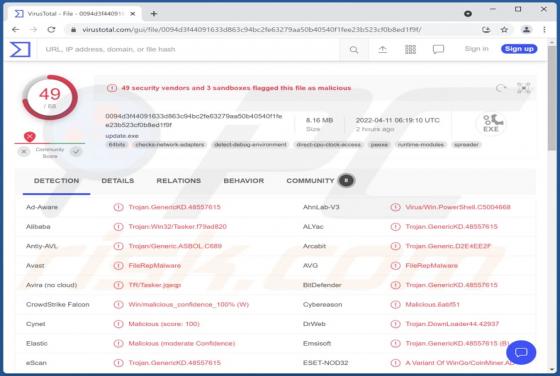
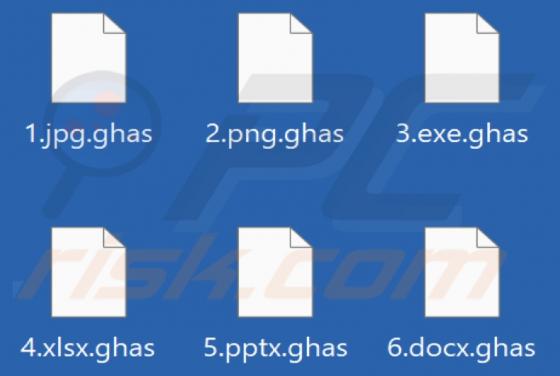
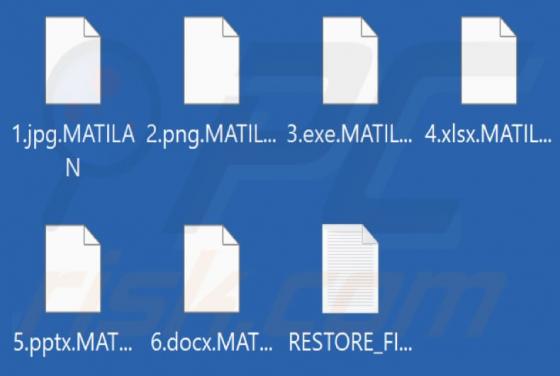
We have examined this email and found that the cybercriminals behind it attempt to trick recipients into executing a malicious file extracted from the attached file. It is disguised as a letter from DHL (a legitimate logistics company) regarding shipping documents that require review. Cybe