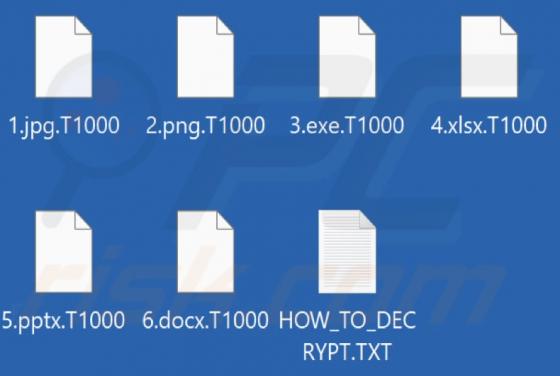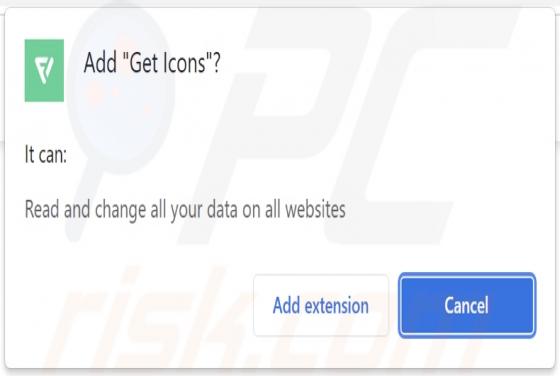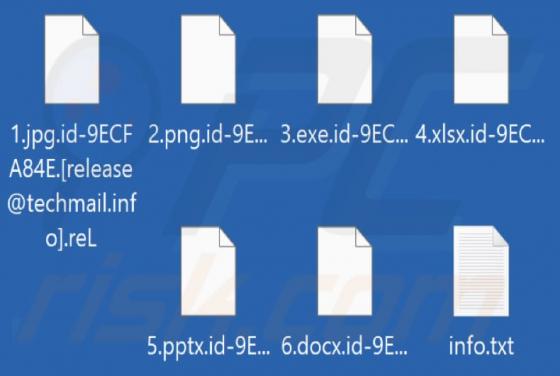
Pick Dark Browser Hijacker
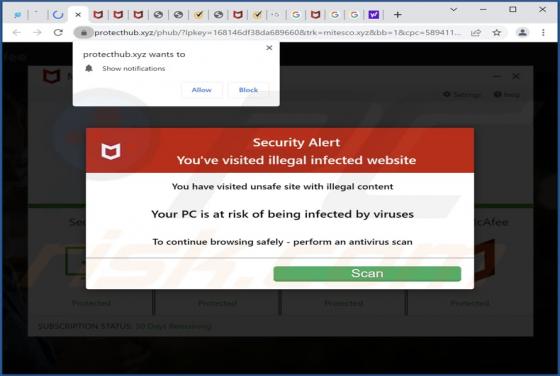
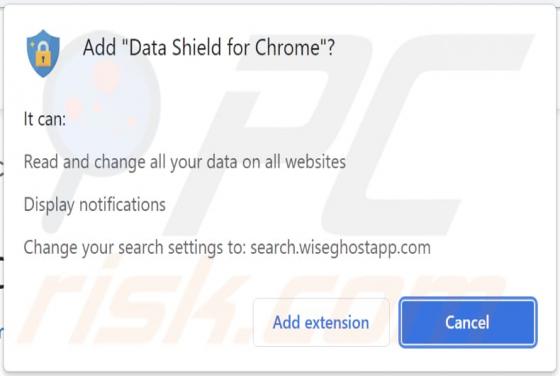
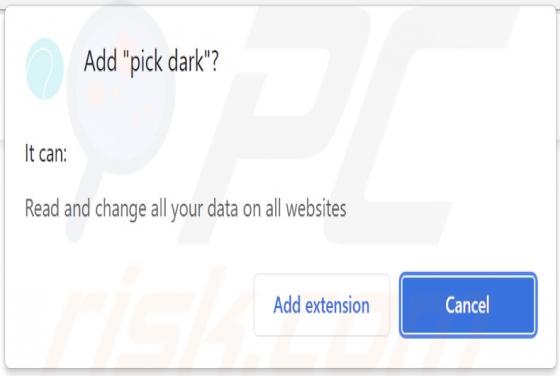
Our researchers discovered the pick dark browser extension during a routine inspection of deceptive download pages. This piece of software promises to enable dark mode for simple design websites. However, we determined that pick dark operates as a browser hijacker and promotes the getsins.com fake