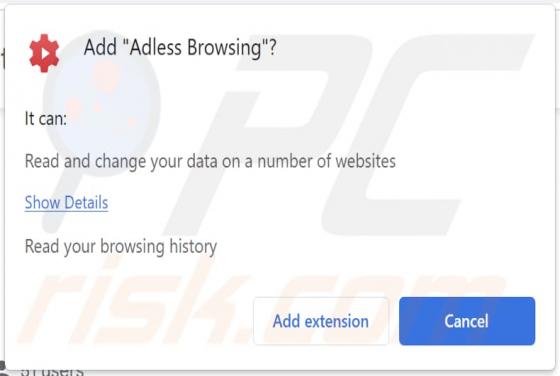
Adless Browsing Adware
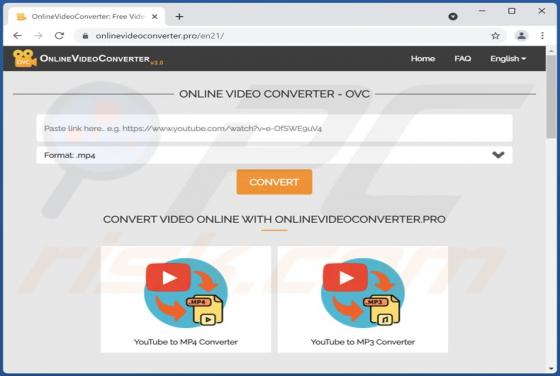
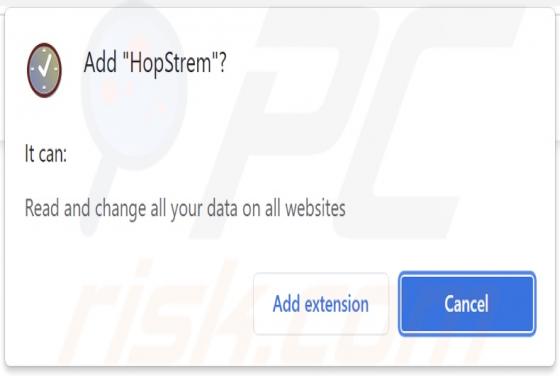
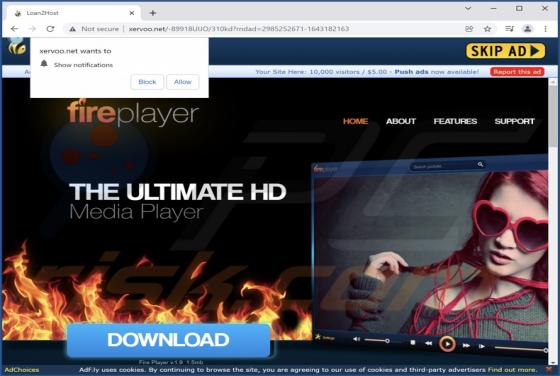
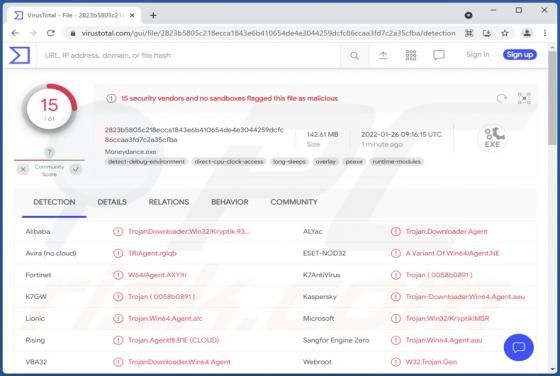
We have discovered the Adless Browsing extension on a deceptive website, suggesting that it may be necessary to install a free extension to continue browsing the page. After installing and analyzing Adless Browsing, we have found that it generates advertisements (it functions as adware). A