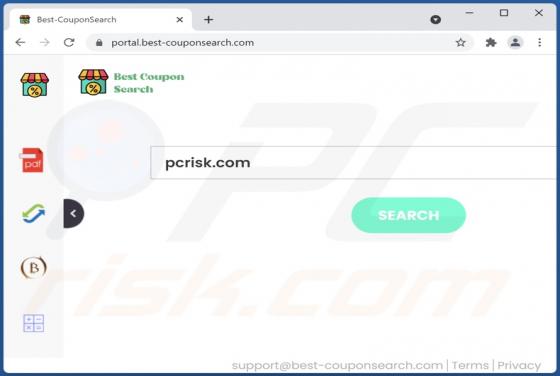
Best-CouponSearch Browser Hijacker
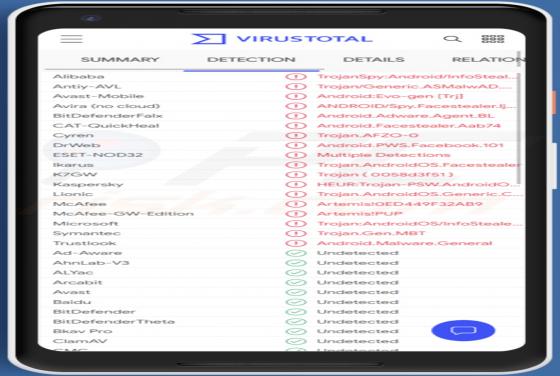
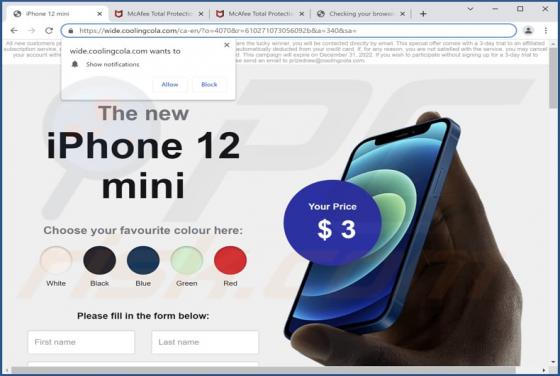
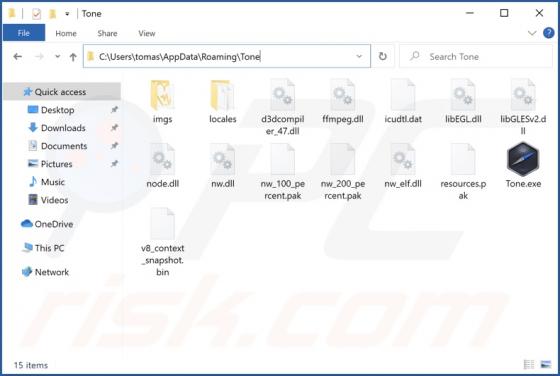
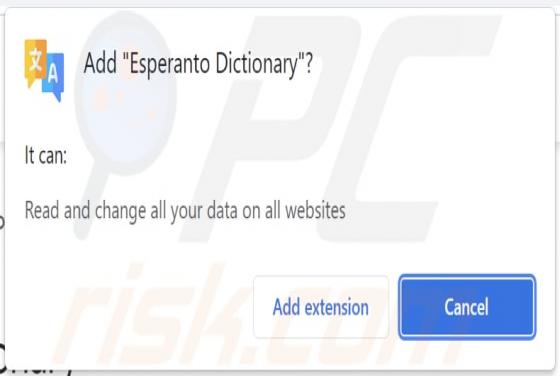
After installing the Best-CouponSearch browser extension onto our test system, we noticed unwanted redirects to the best-couponsearch.com fake search engine. This was caused by modifications the extension made to browser settings. The described behavior classifies Best-CouponSearch as a browser hi