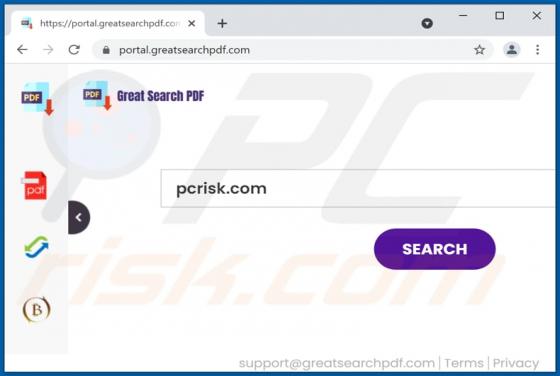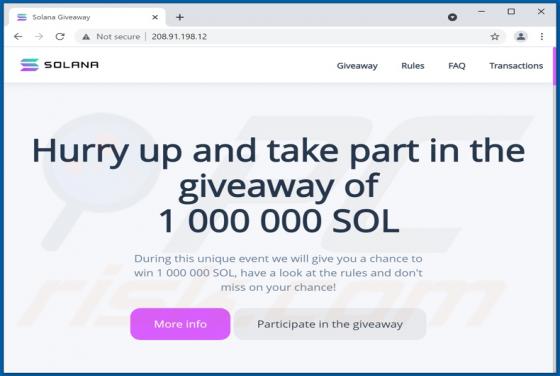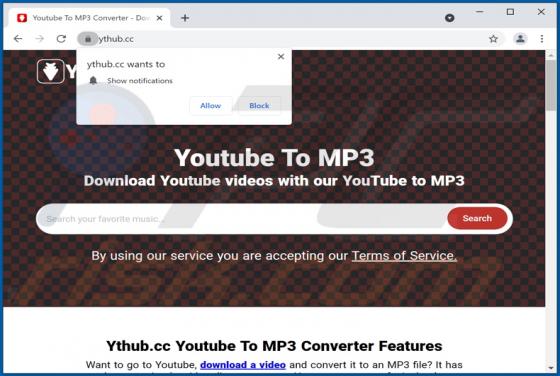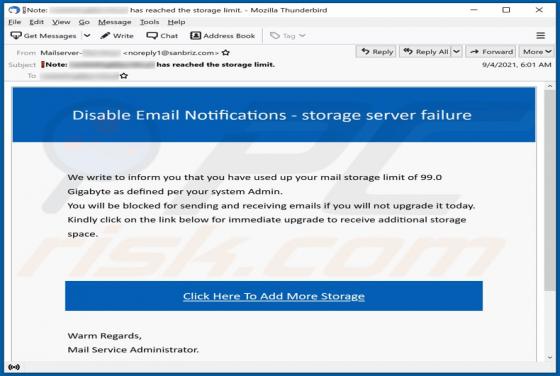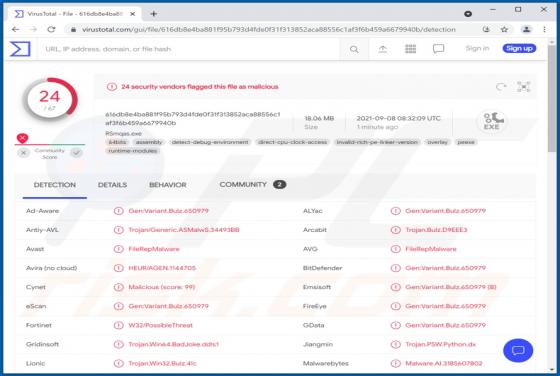
Kuukostealer Malware
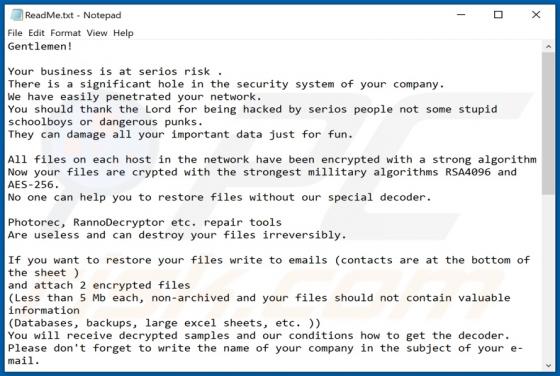
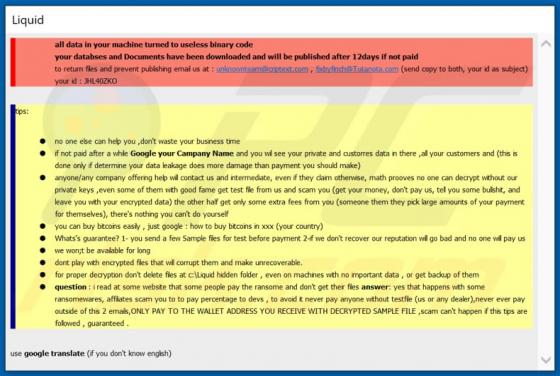
Kuukostealer is a malicious program written in the Python programming language. The primary functionality of this malware is extraction of personal and vulnerable information from infected systems. Kuukostealer has keylogging abilities. In other words, it records keystrokes. Typically, cyb