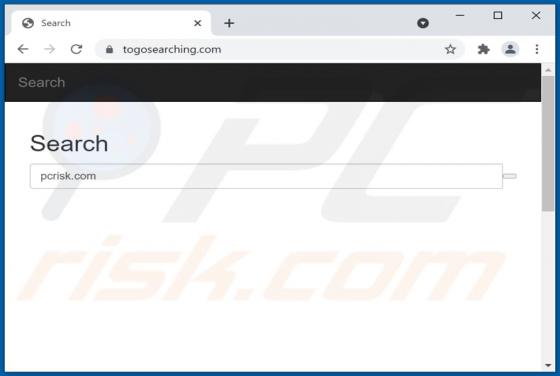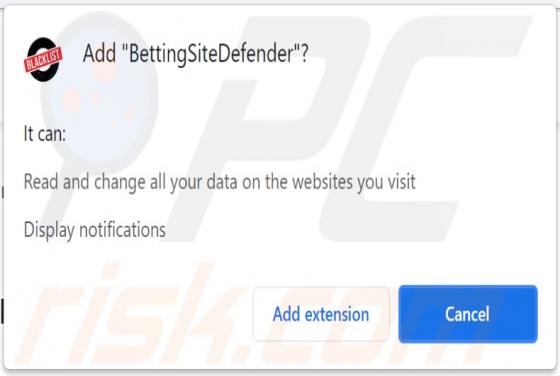
BettingSiteDefender Adware
BettingSiteDefender is advertised as an extension that checks blacklisted websites and prevents a browser from opening them. However, this app has the qualities of adware - it generates revenue for its developer by displaying advertisements. Also, it can read and change data on the websites that u