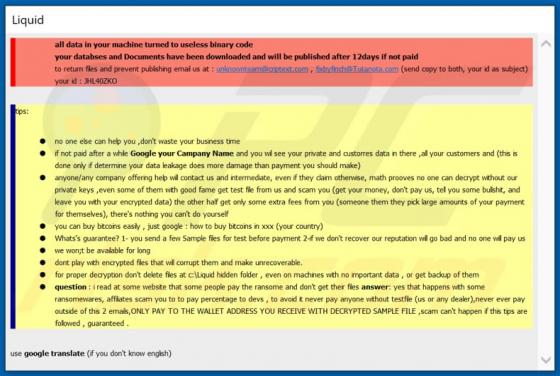
Liquid Ransomware
Liquid is a type of malware that prevents victims from accessing their files (it encrypts them) unless a ransom is paid. It also renames files and creates the "Liquid.hta" file (ransom note). Liquid ransomware renames filenames by prepending the victim's ID, unknownteam@criptext.com email address