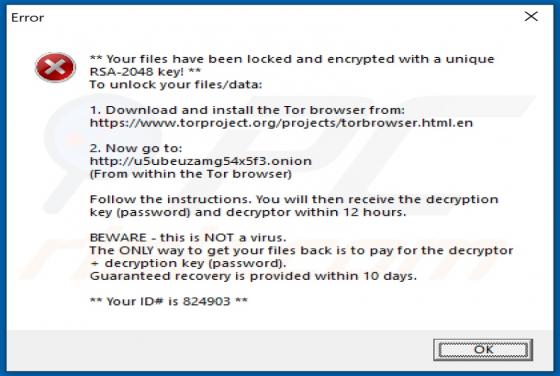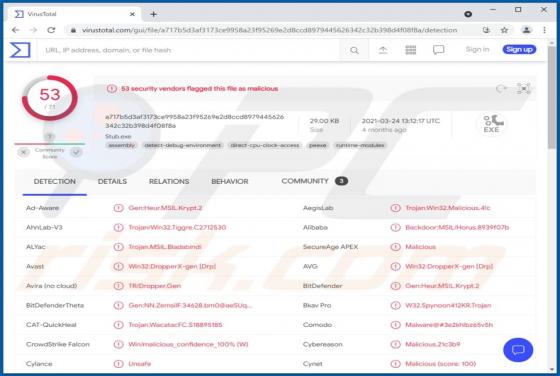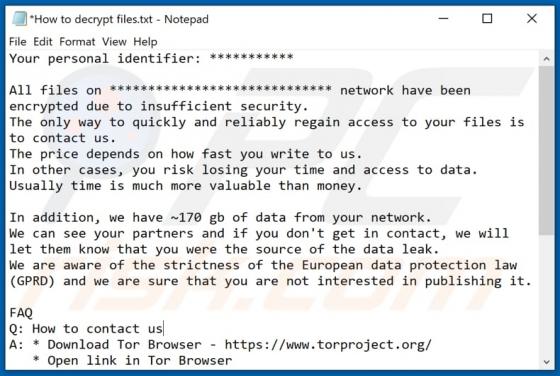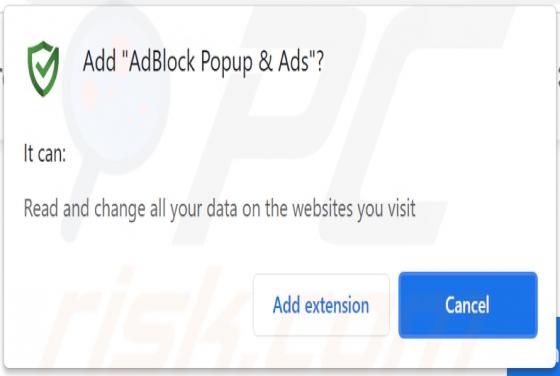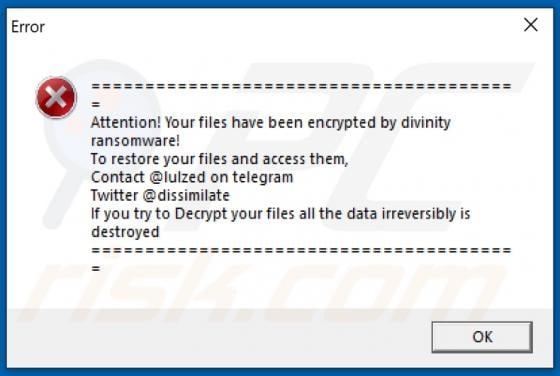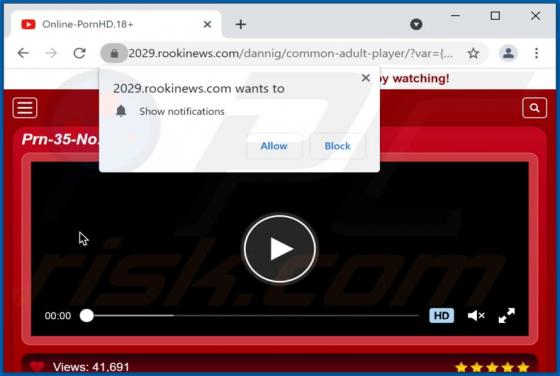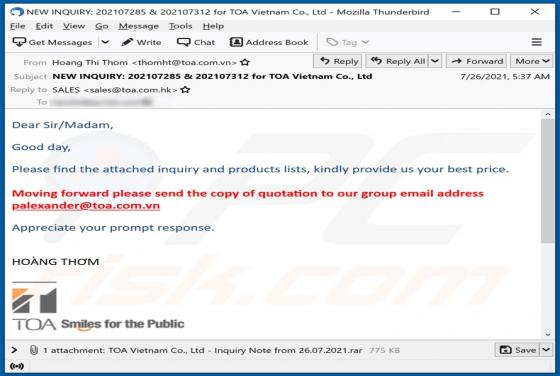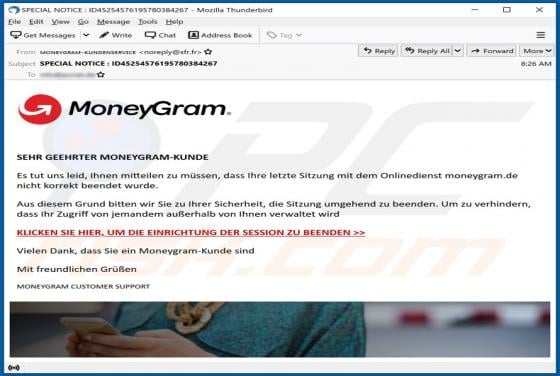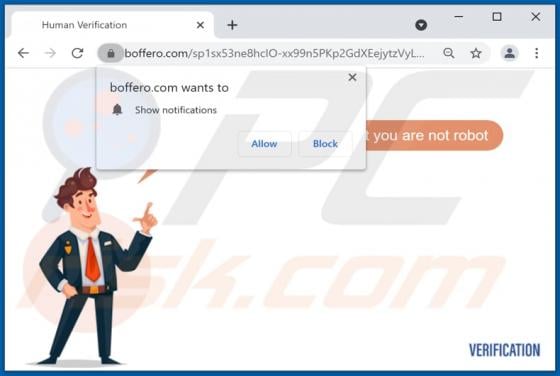
Boffero.com Ads
Boffero[.]com is designed to load a fake CAPTCHA test (to trick its visitors into allowing it to show notifications) and promote questionable pages. It is important to mention that users do not visit websites like boffero[.]com on purpose. Usually, these pages get opened via other shady pages, dub