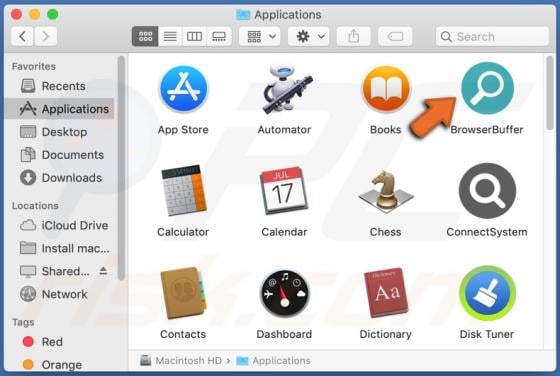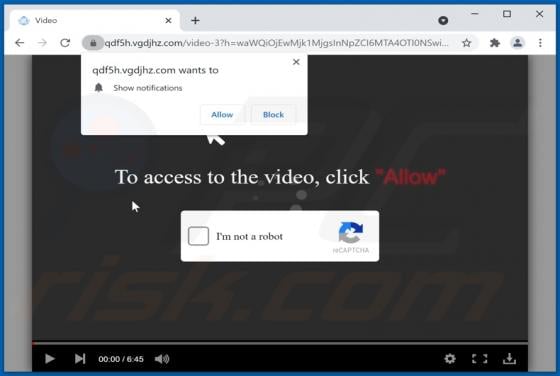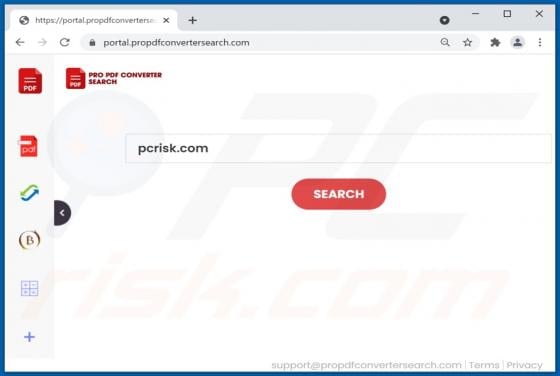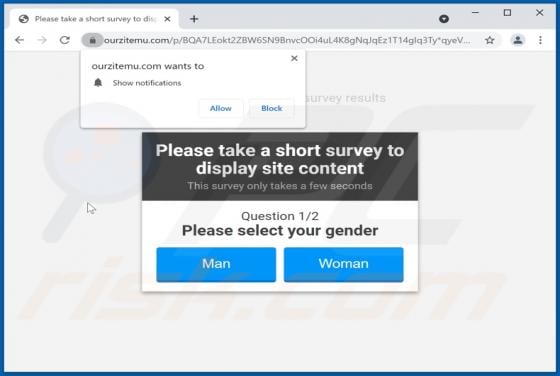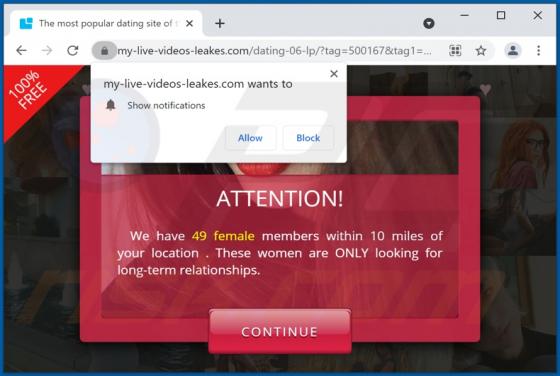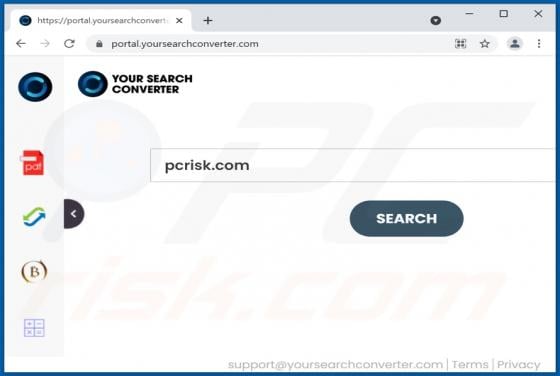
YourSearchConverter Browser Hijacker
YourSearchConverter is a browser hijacker that promotes the yoursearchconverter.com fake search engine. It operates by modifying browser settings to cause redirects to its web searcher. This rogue browser extension likely spies on users' browsing activity as well. Since most users inadvertently do