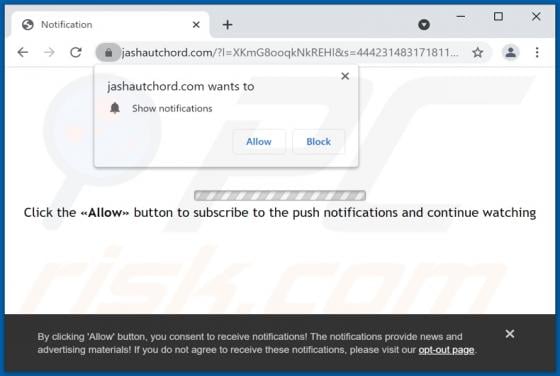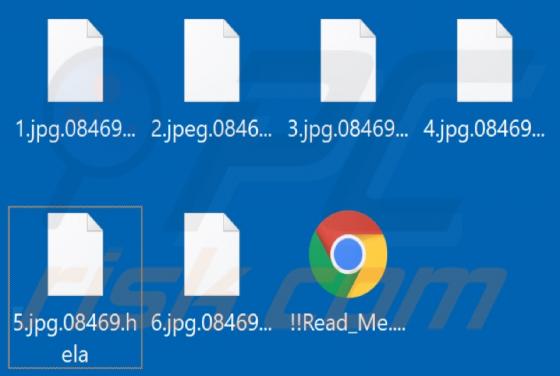
Hela Ransomware
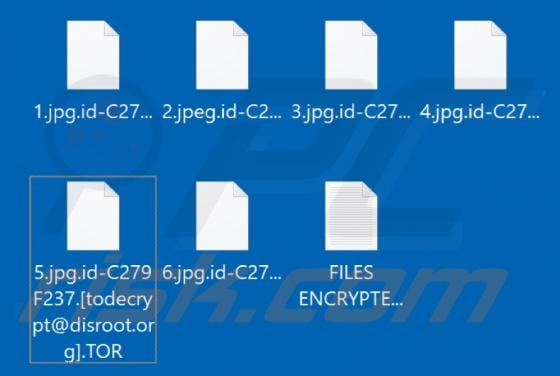
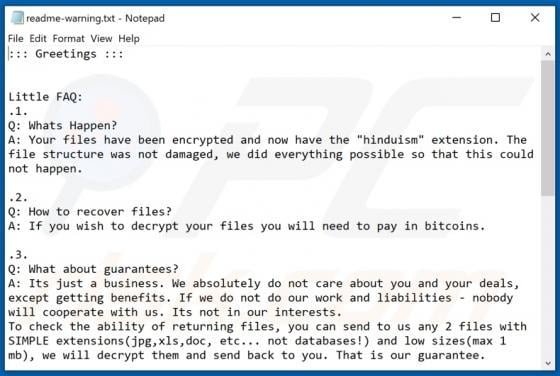
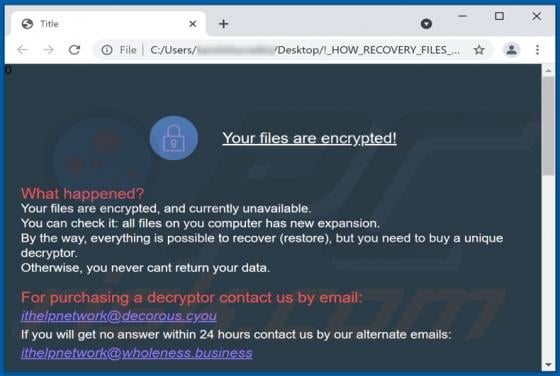
Hela is a new variant of the Ragnarok ransomware. It operates by encrypting data and demanding payment for the decryption. In other words, Hela ransomware renders files inaccessible and asks victims to pay - to recover access to their data. During the encryption process, affected files are append