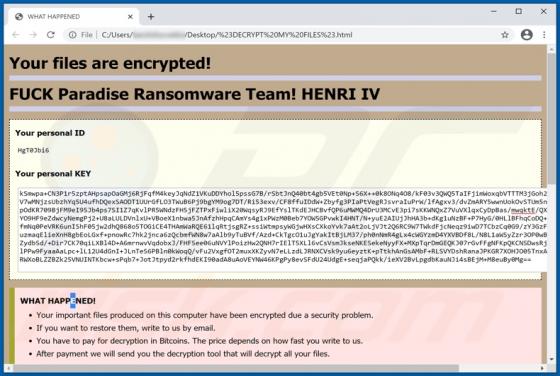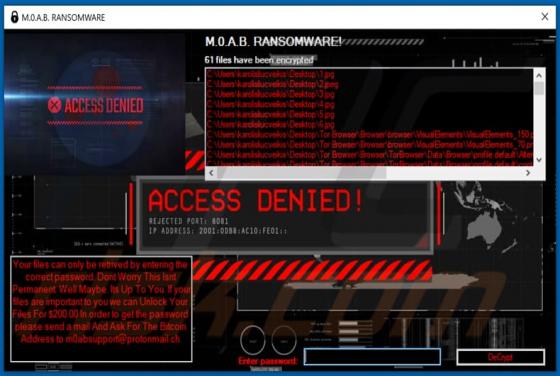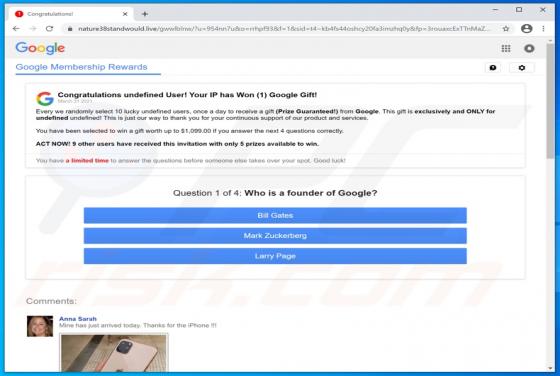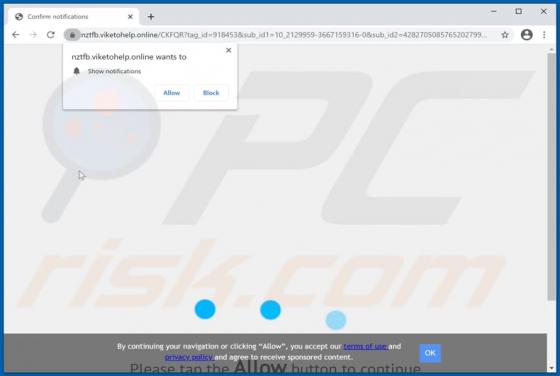
365Scores - Live Scores and Sports News
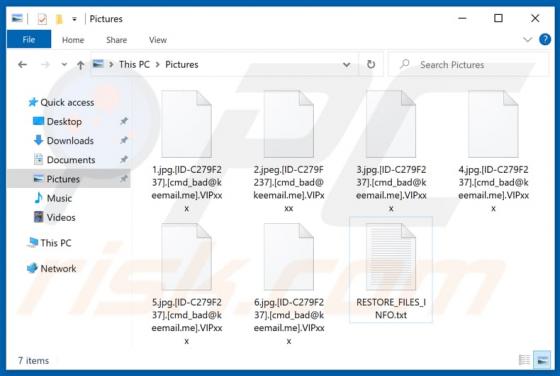
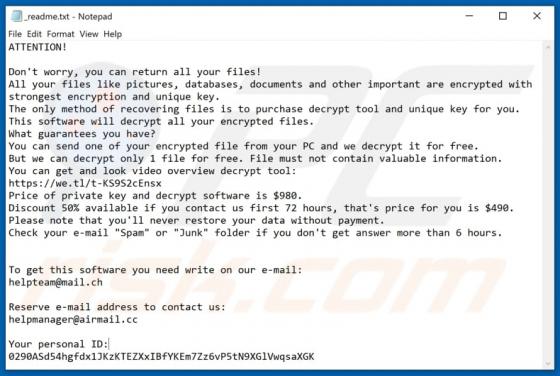
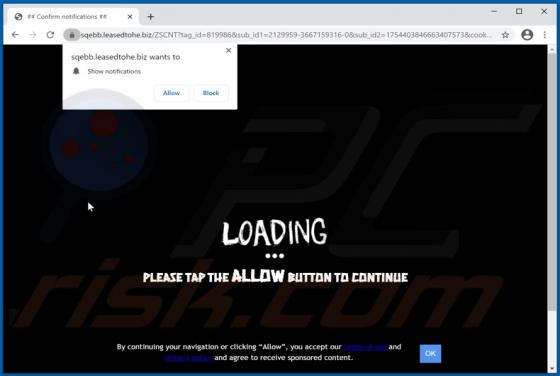
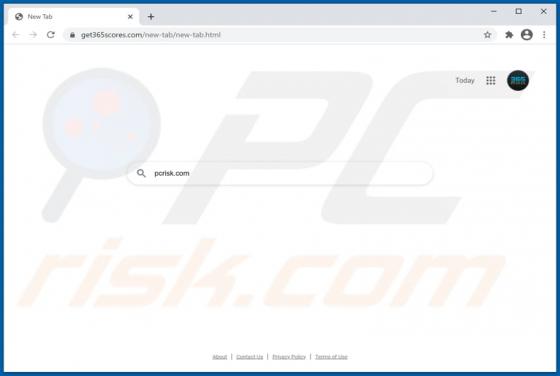
"365Scores - Live Scores and Sports News" is a typical browser hijacker: it hijacks browsers to promote a fake search engine (get365scores.com). Generally, apps of this type achieve this by changing browser settings. 365Scores - Live Scores and Sports News also reads browsing-related data. Typica