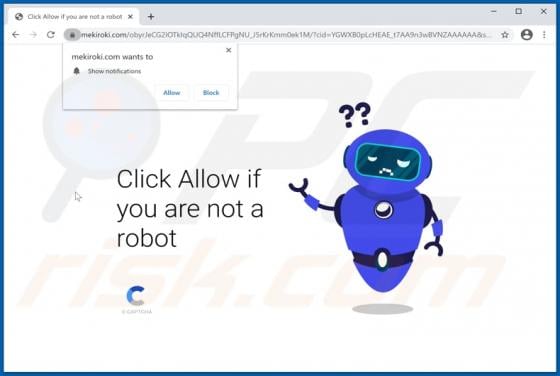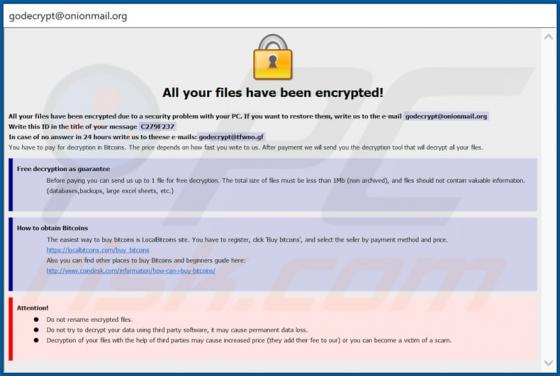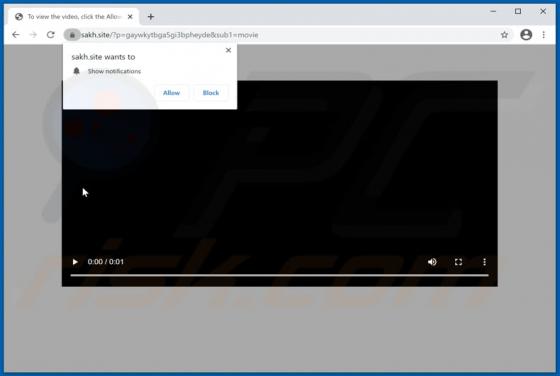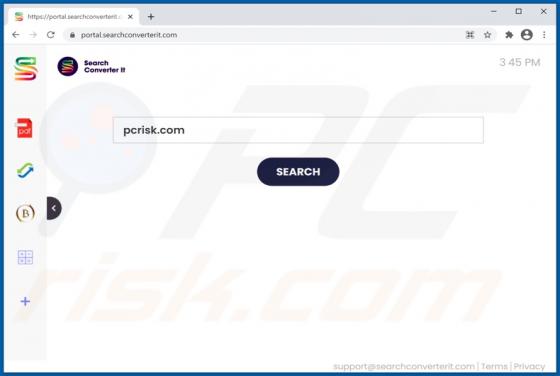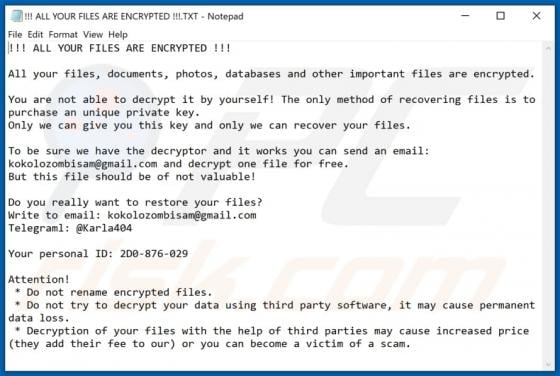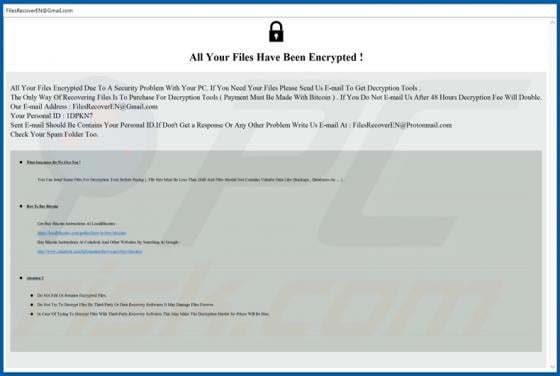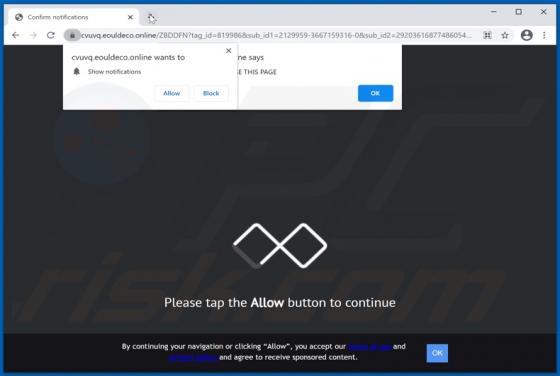
Eouldeco.online Ads
Sharing similarities with mekiroki.com, sakh.site, mobilemediahits.com, cfplay.online, and countless others, eouldeco[.]online is a rogue website. It operates by delivering dubious content and redirecting visitors to other untrusted/malicious sites. Users seldom enter these web pages intentionall