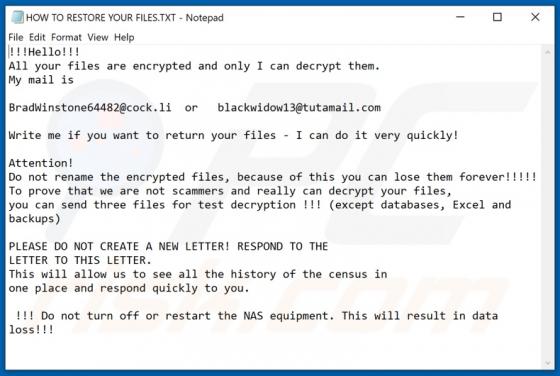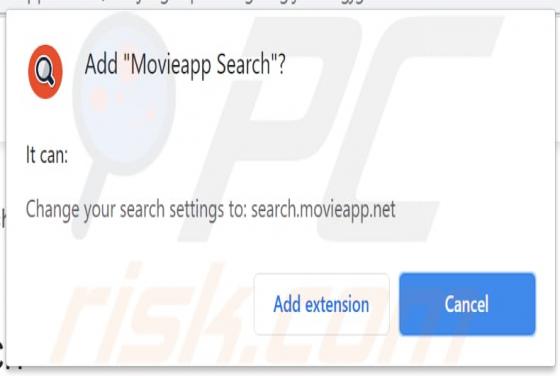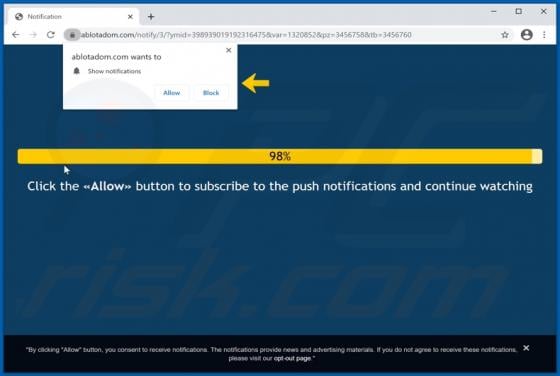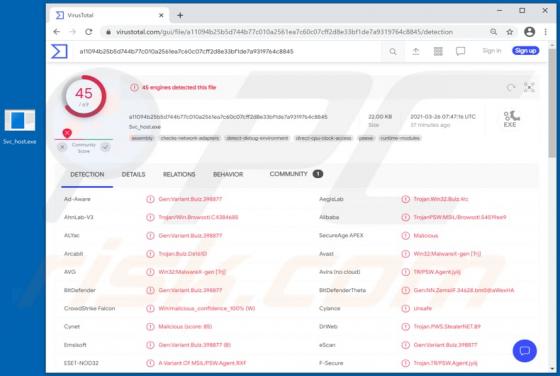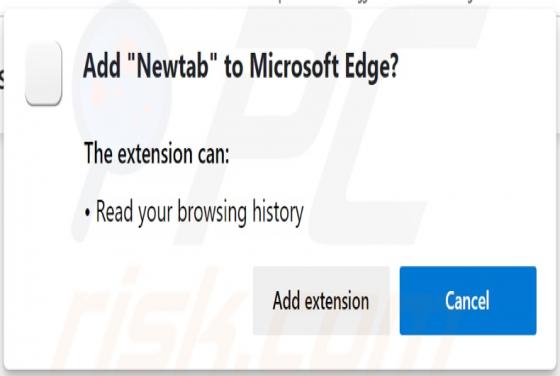
Newtab Browser Hijacker
Newtab is dubious software that promotes the fxsmash.xyz fake search engine by modifying browser settings. Therefore, Newtab is classified as a browser hijacker. Additionally, Newtab collects browsing-related information. Since most users download/install browser hijackers inadvertently, they are