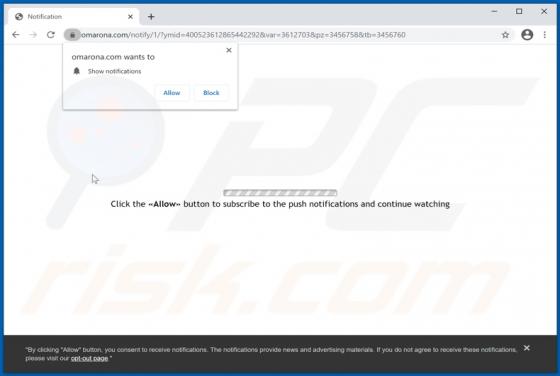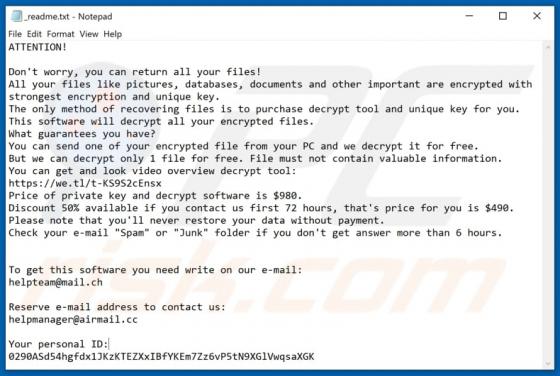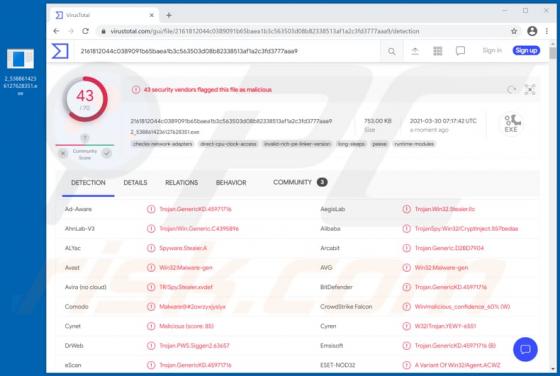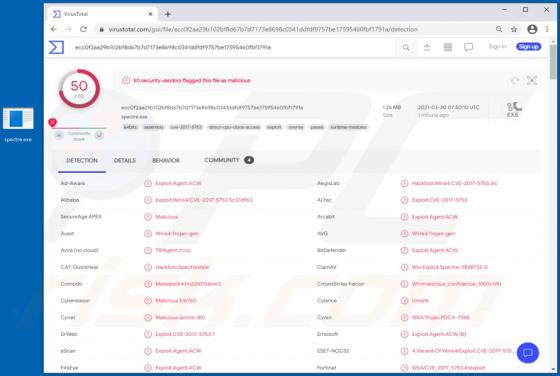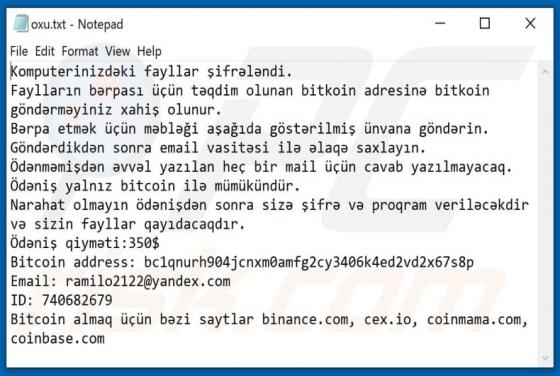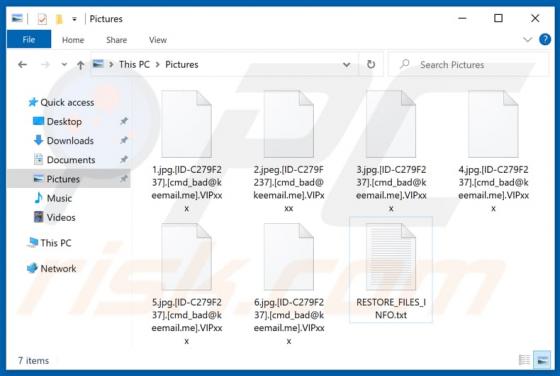
VIPxxx Ransomware
Ransomware-type malware encrypts files so that victims cannot use or access them without valid decryption keys/programs purchased from the attackers. VIPxxx also renames files by appending the victim's ID, cmd_bad@keemail.me email address, and the ".VIPxxx" extension to filenames. For example, "1