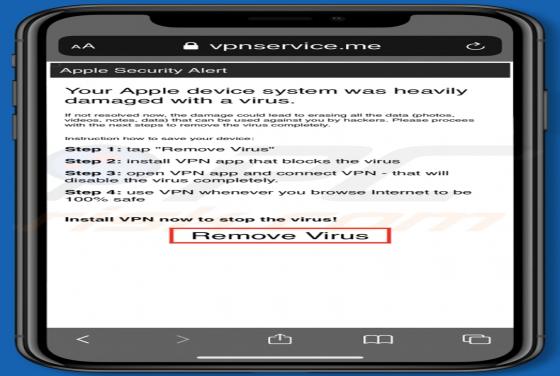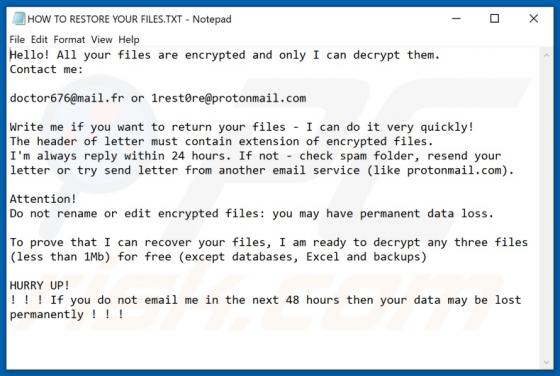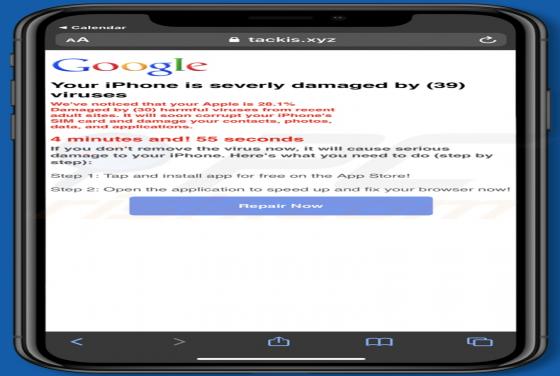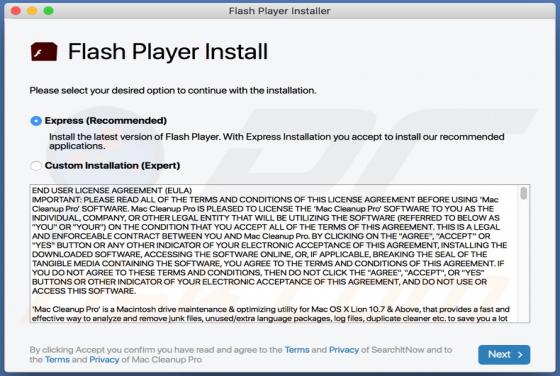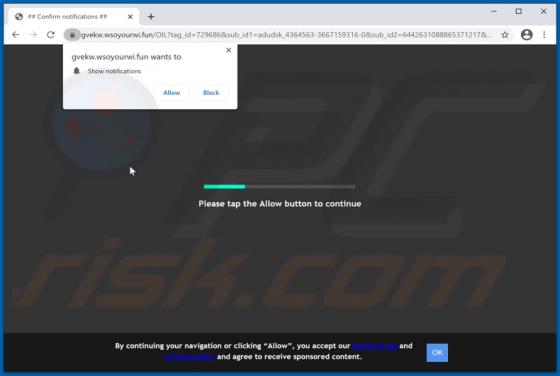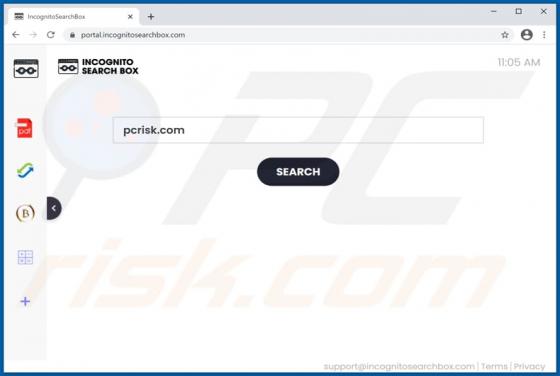
IncognitoSearchBox Browser Hijacker
Browser hijackers are potentially unwanted applications (PUAs) that are designed to promote fake search engines. Usually, applications of this type promote their search engines by changing browser settings. IncognitoSearchBox promotes the incognitosearchbox.com address. Additionally, most browser