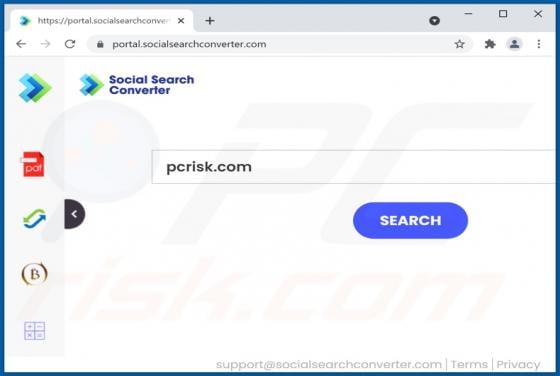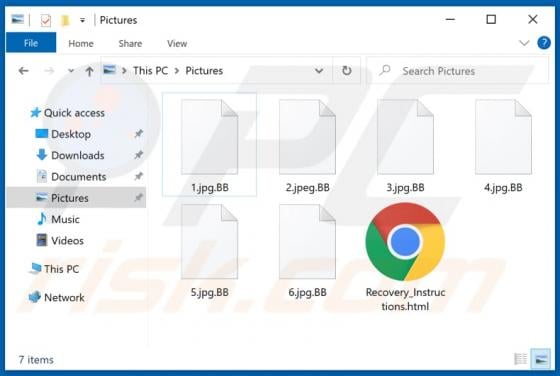
BB Ransomware
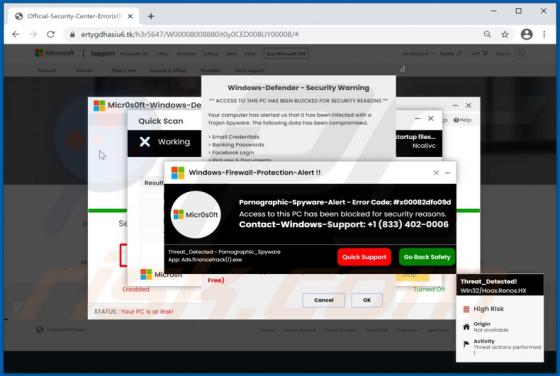
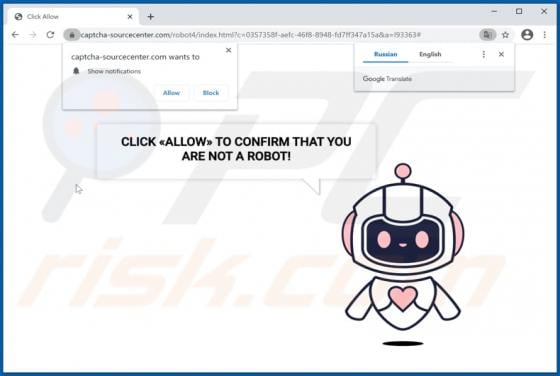
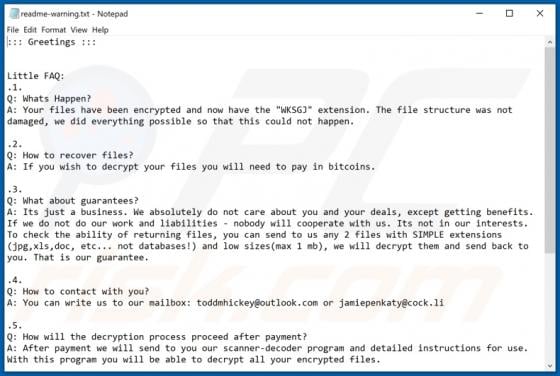
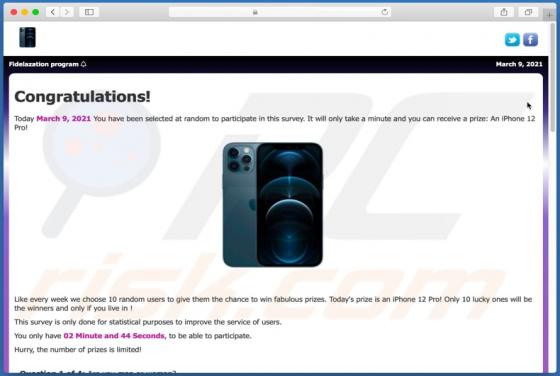
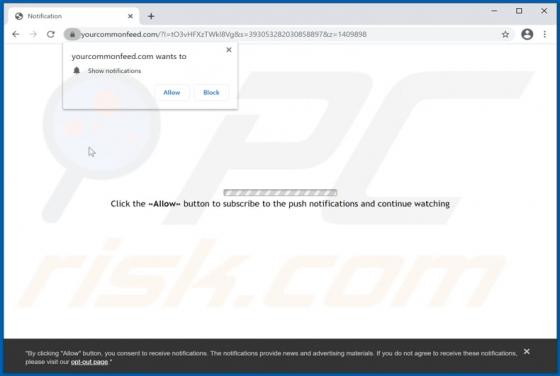
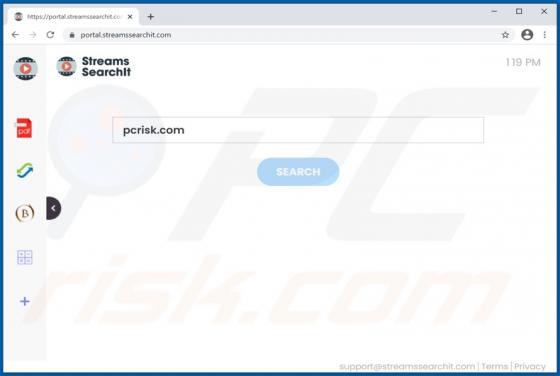
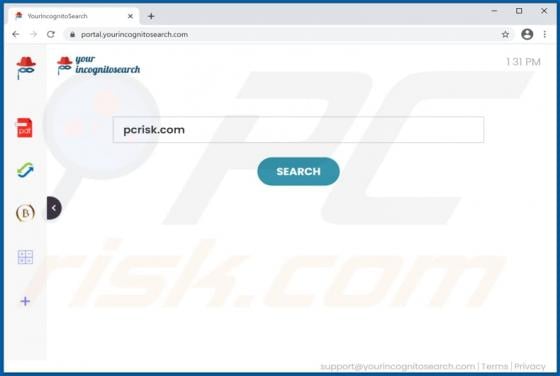
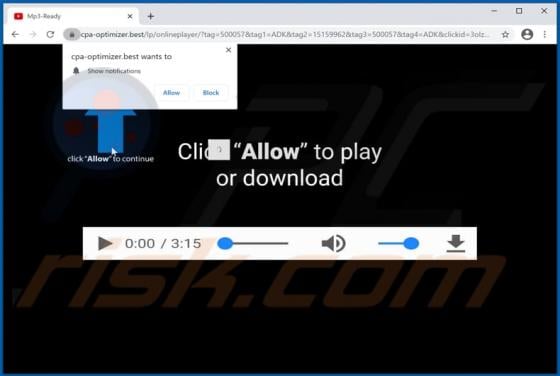
Users who have computers infected with ransomware cannot access or use their files and can also lose access to the entire operating system. Typically, ransomware encrypts files with a strong cryptographic algorithm and keeps them inaccessible unless a ransom is paid. BB is a ransomware variant be